Android HackTheBox Challenge – Pinned Write-Up
This is a Write Up on how to complete the challenge Pinned on Hack The Box.
*You will need to have a proxy utility like Burp and a device to complete this challenge. Here is a link to my guide on setting both up if needed.
The API Version for HTB Challenges needs to be level 29 or earlier.
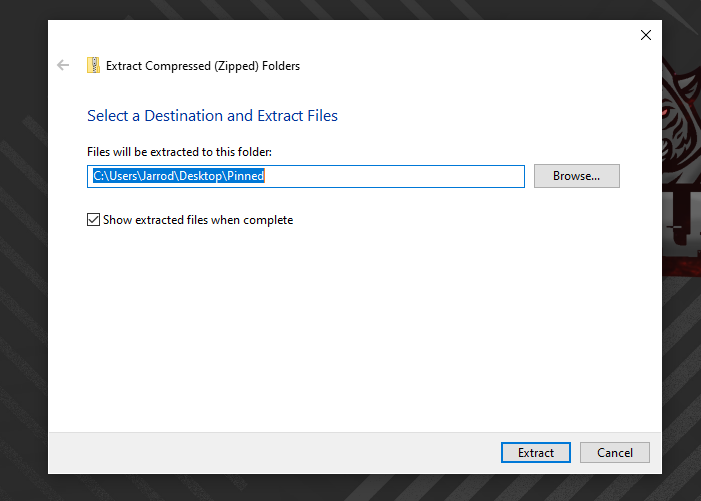
First we will download Pinned from HTB Challenges. Once downloaded we can extract the files to our workspace.
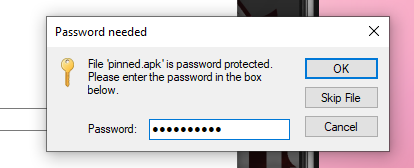
The password is hackthebox to get the files.
Now we have access to the pinned.apk file.
You can drag and drop the pinned.apk to the emulator device.
You should now see Pinned in your apps.
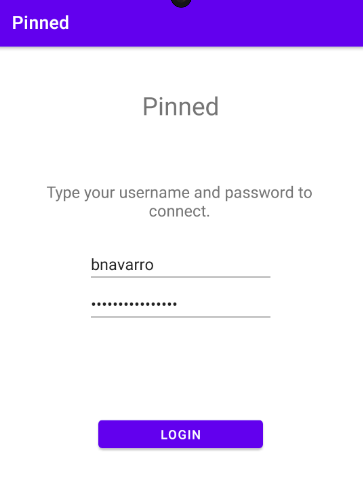
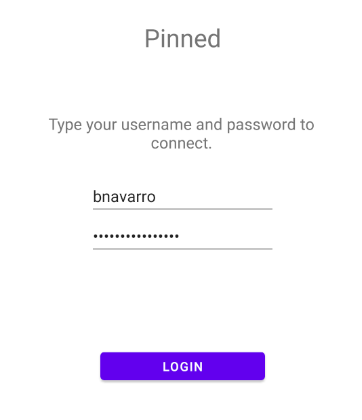
Opening the app should reveal this login form. We are now ready to test this Android application.
The goal of this lab is to perform a SSL Pinning Bypass.
SSL pinning refers to a security technique used to prevent man-in-the-middle (MitM) attacks when establishing secure connections over HTTPS (SSL/TLS) between a mobile app and a server. This is preventing us from viewing HTTP requests/responses in Burp.
We will use Frida to bypass the SSL Pinning for this application and allow us to see the HTTP requests and responses in Burp Suite.
Frida can be installed with pip (python package manager)
pip install frida-tools
We can setup the Frida server by imputing the following commands:
unxz frida-server-[version]-android-x86.xz (unzip file) adb push frida-server-16.1.4-android-x86 /data/local/tmp/frida-server (move frida server to /data/local/tmp/) adb shell "chmod 755 /data/local/tmp/frida-server" adb shell (connect to device in shell) /data/local/tmp/frida-server & (start frida server)
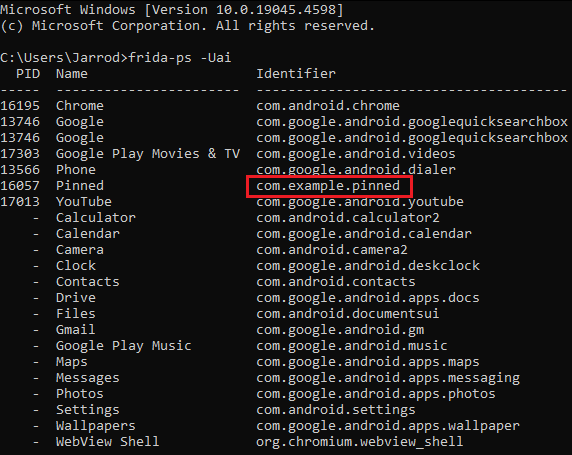
With Frida server started on our emulator/device we can run a Frida command to identify running processes.
frida-ps -Uai
We should see our Pinned apk running. This means we can interact with this application.
Now we need to use a Frida script to perform our SSL Pinning bypass.
We will leverage this script.
We need do one last bit of prep work. Reading the script reveals we need a certificate in order to execute this. Running without the certificate will cause the Frida script to fail and result in this error:
We can use the same cert we exported from Burp Suite, that we also stored on the emulator in /sdcard. Running:
adb shell "cp /sdcard/burp.crt /data/local/tmp/cert-der.crt" adb shell "chmod 755 /data/local/tmp/cert-der.crt"
This will take the burp certificate we placed there earlier and copy the certificate to what the script is looking for it.
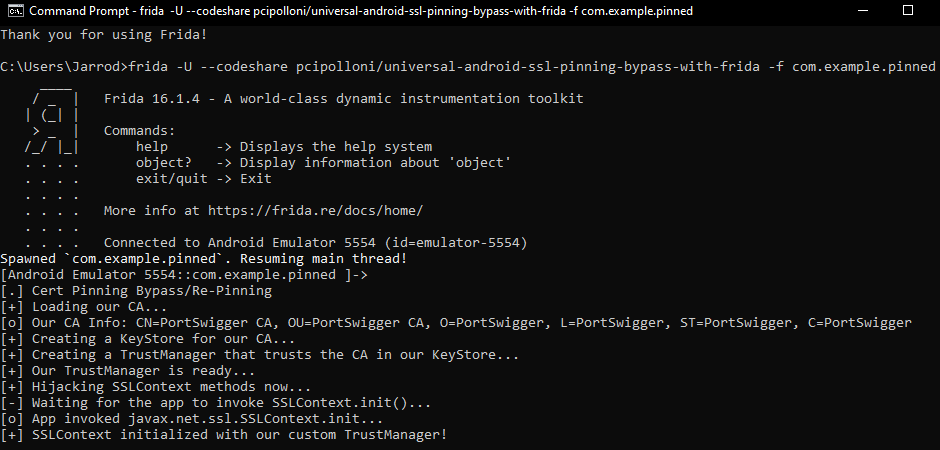
Now to execute the Frida SSL Pinning Bypass Script. To use the script we can run:
frida -U --codeshare pcipolloni/universal-android-ssl-pinning-bypass-with-frida -f com.example.pinned
Our Frida script should fire off and open Pinned on our emulator.
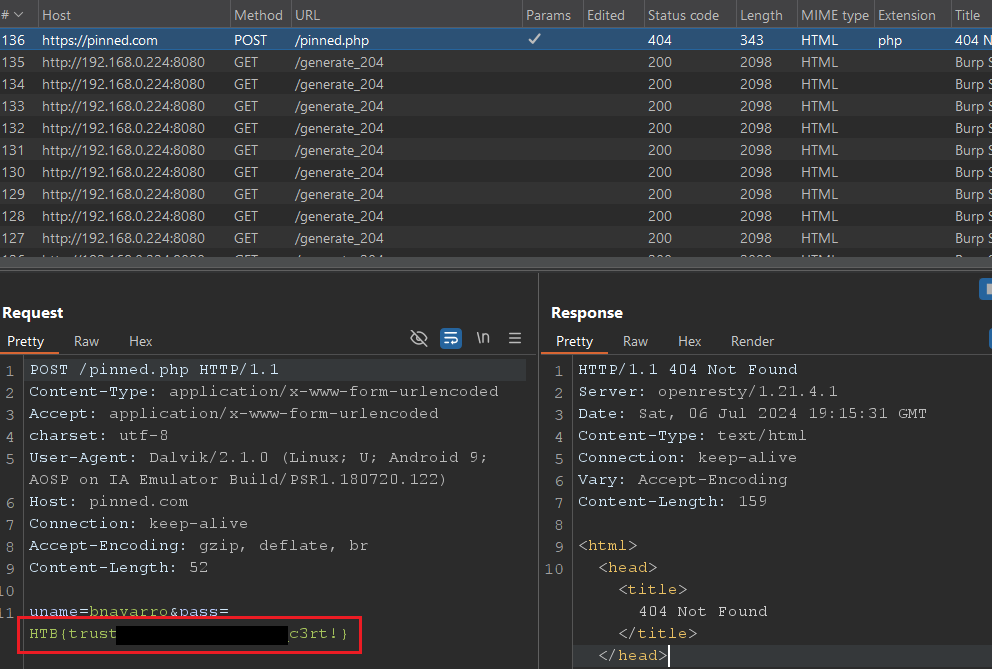
Clicking Login should now send a request through Burp. That means for this application we have bypassed the SSL Pinning and can analyze HTTP requests.
Here in Burp we can see the POST request and the flag.
That completes the challenge! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod