Android HackTheBox Challenge – Don’t Overreact Write-Up
This is a Write Up on how to complete the challenge Don’t Overreact on Hack The Box.
* We will be using JADX-GUI (Dex to Java decompiler) to solve this lab.
JADX-GUI is a graphical user interface (GUI) for the JADX decompiler. JADX is a tool that allows you to reverse-engineer Android APK files by converting DEX (Dalvik Executable) files back into Java source code. The GUI version of JADX provides an easier way for us to decompile APKs and view the resulting code.
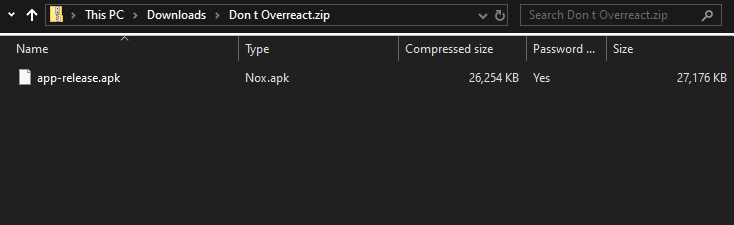
First we will download Don’t Overreact from HTB Challenges. Once downloaded we can extract the files to our workspace.
The password get the files is hackthebox.
Now drag and drop the app-release.apk to our emulator device. *Note that an emulator is not needed to solve this lab. However if you can set one up it would make future challenges easier to solve.
You should now see it in your apps.
Opening the app reveals a Hack the Box background.
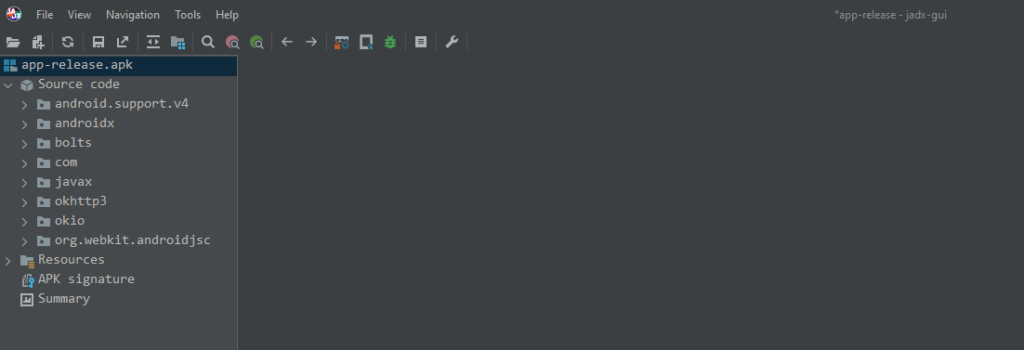
We can drag and drop our .apk file into JADX-GUI.
From here we can see several drop-down menus for the .apk file.
Let’s do a quick breakdown of the de-compiled .apk file in JADX-GUI.
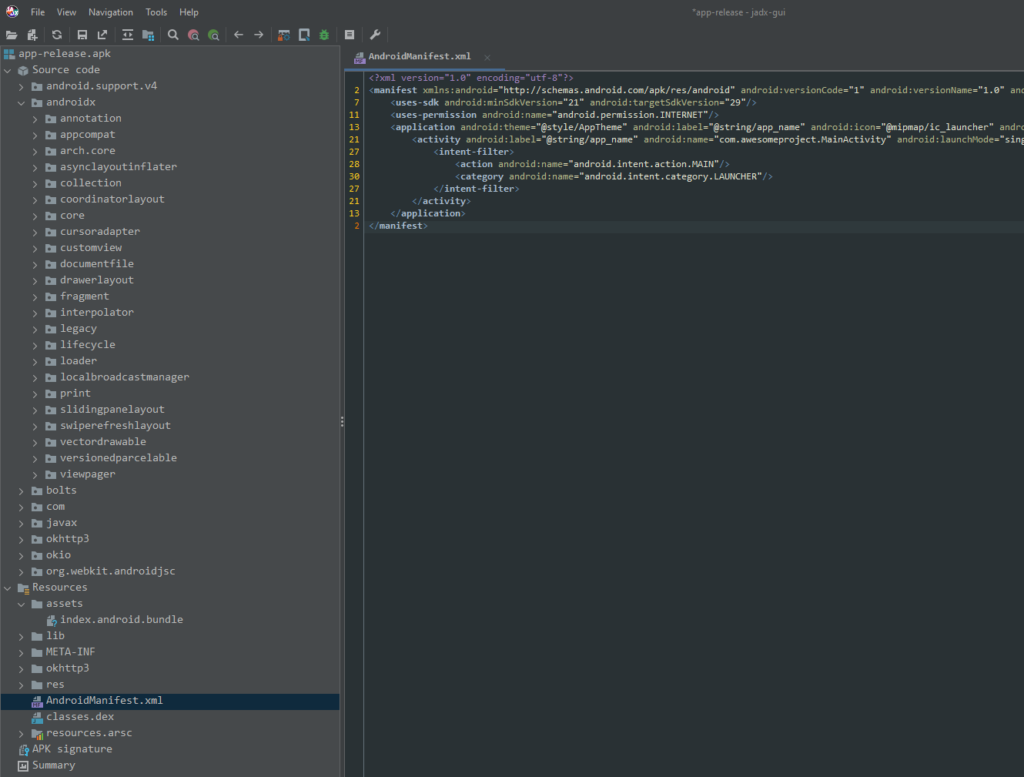
The Source Code Directory refers to the location within the application where all the de-compiled Java source files are organized and stored. It acts as a virtual file structure, displaying the various Java classes, methods, and other resources that have been extracted from the .apk. Essentially, it serves as the central hub for viewing and exploring the app’s code and resources in a structured, accessible format.
The Resource Directory is where non-code assets from the de-compiled APK are stored and displayed. This includes various resources like XML files (layout files, AndroidManifest.xml), images, and other assets used by the app.
JADX-GUI makes it easier for us to navigate through everything, to look for important and sensitive data.
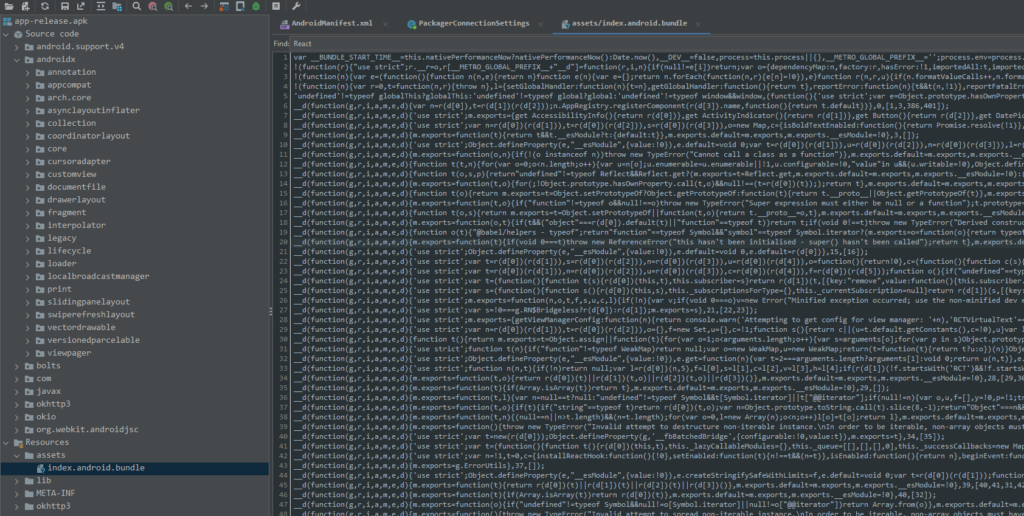
Observing the index.android.bundle file we can see we are working with a React Native application.
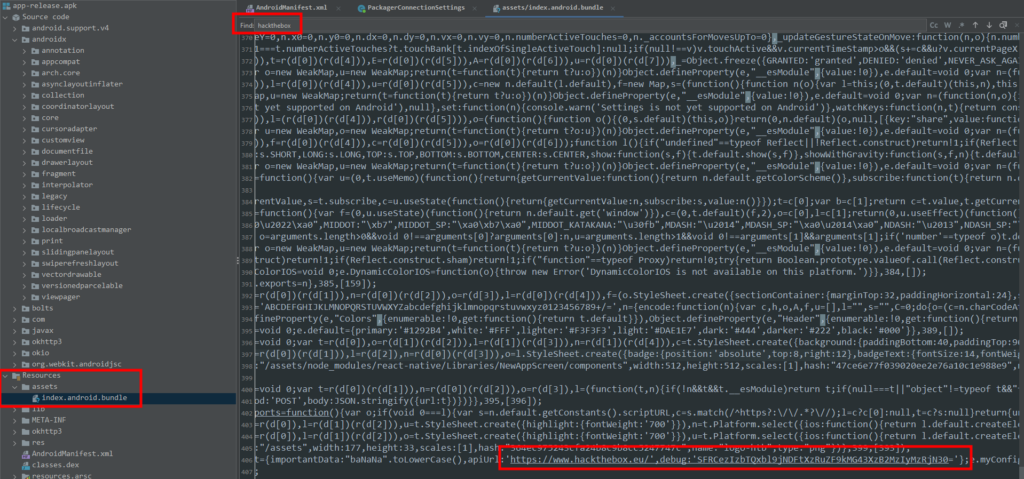
Searching through this file we can find a reference to hackthebox at the bottom of the file and a reference to a debug API Url.
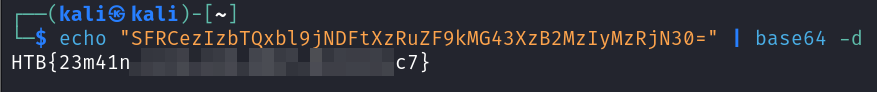
We can use the base64 -d command to decode this string.
Decoding the string contains the flag needed to solve this challenge.
That completes the challenge! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod