DOM XSS in innerHTML sink using source location.search
In this post we will walk step by step through how to solve DOM XSS in innerHTML sink using source location.search on PortSwigger. This lab’s difficulty is Apprentice and it is the fourth lab in the Cross-Site Scripting labs on Portswigger.
Link to lab: https://portswigger.net/web-security/cross-site-scripting/dom-based/lab-innerhtml-sink
To solve this lab, perform a cross-site scripting attack that calls the alert function.
To start the lab click the ‘Access the Lab’ button.
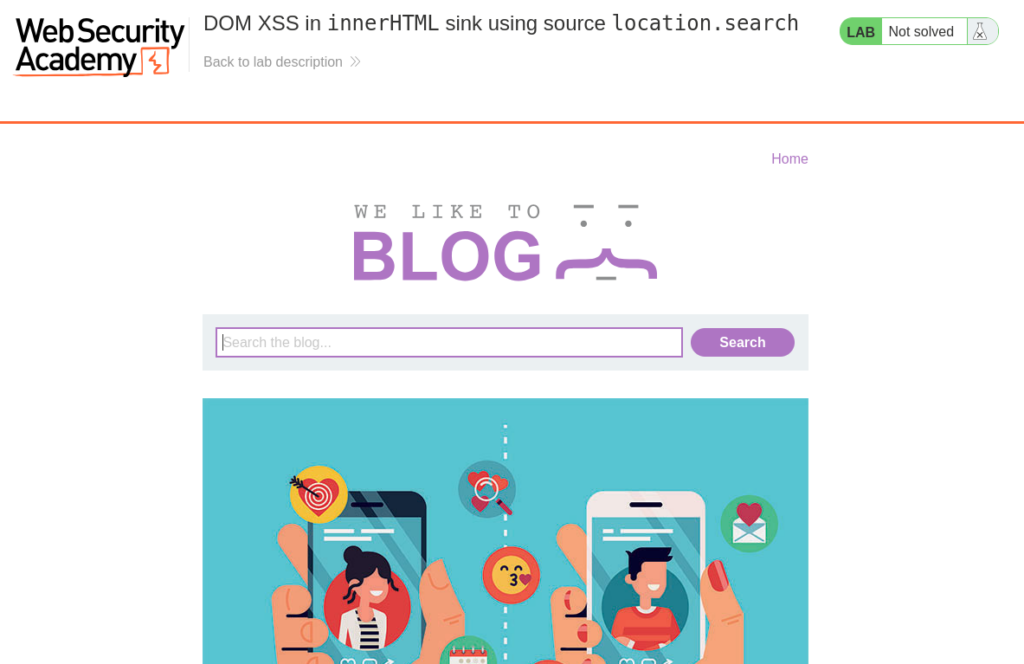
When we begin the lab we will be greeted with a blog page featuring a search field and a variety of blog posts. Don’t worry if the content differs from the screenshot; PortSwigger Labs can modify the content each time the lab is initiated.
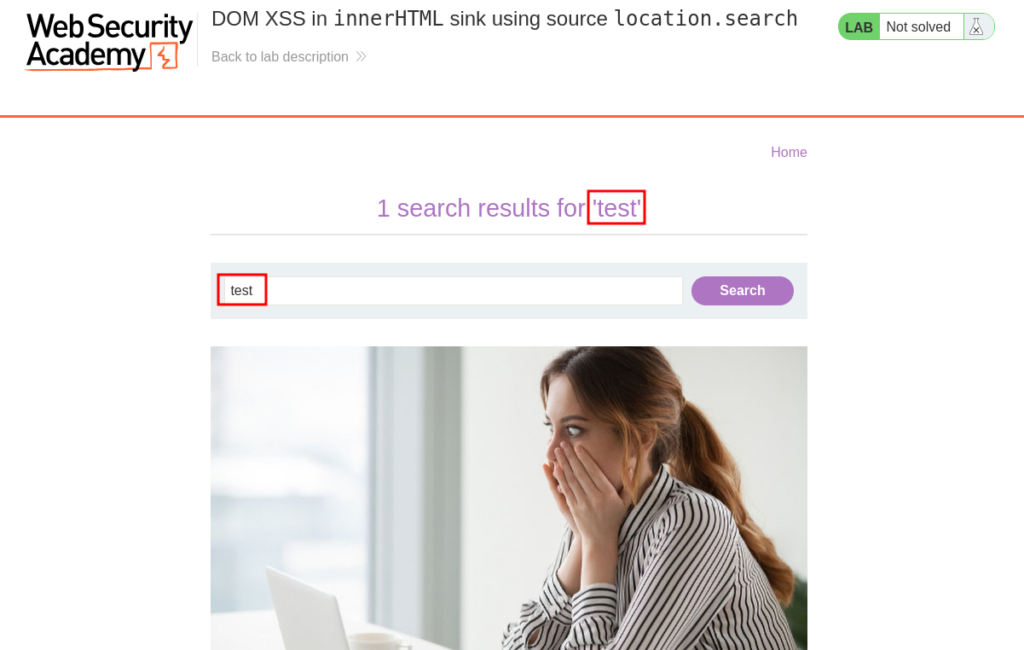
To start our test let’s begin by using the ‘Search for blog’ field. Type ‘test’ into the search field and then click the ‘Search’ button. This action will load the page with ‘test’ being reflected back, and prominently displayed on the page.
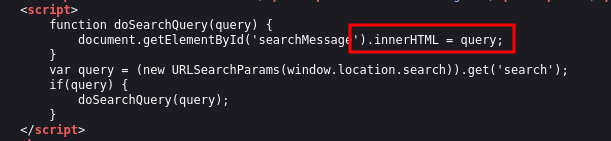
When examining the JavaScript code we can see the code utilize the inner.HTML to write content to the DOM and has the capability to process user input from window.location.search.
In JavaScript using inner.HTML can be considered a bad practice in most situations, particularly in modern web development practices as it does not sanitize input and renders content as HTML.
Understanding this, we can exploit inner.HTML and the output of location.search to inject a JavaScript payload into the application.
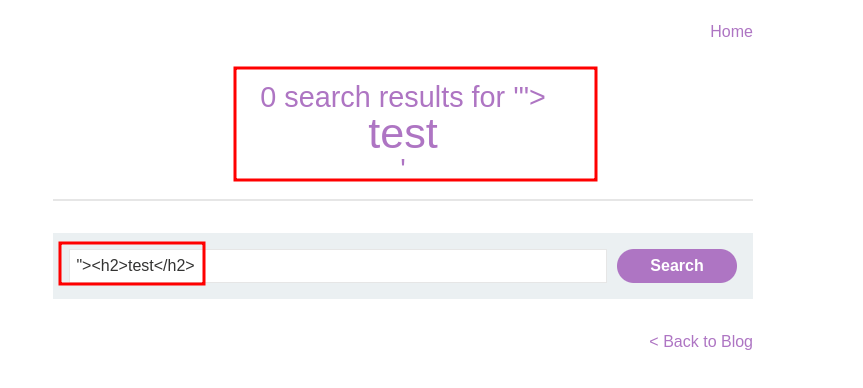
We can start with a simple HTML payload to validate if this is vulnerable to HTML Injection.
"><h2>test</h2>
Using this payload we can observe the <h2>test</h2> as been rendered onto the page. This would imply that we have found an injection point.
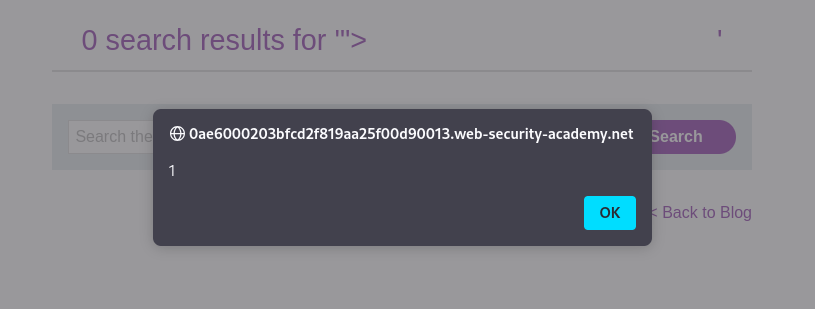
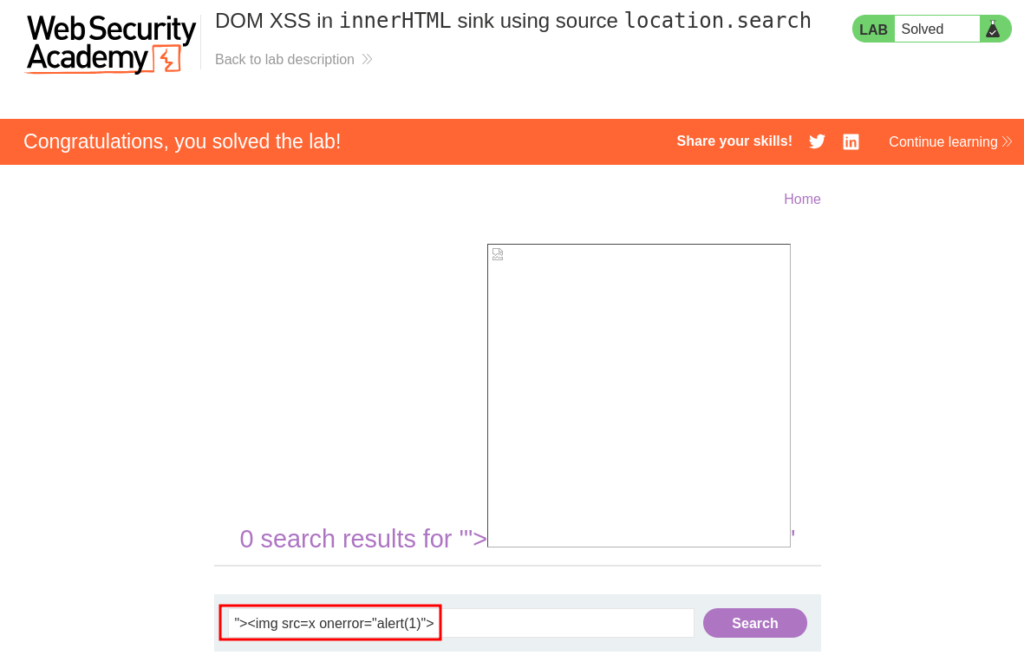
Using the payload "><img src=x onerror="alert(1)"> we can inject our JavaScript code into the web page. The code will go into location.search and then be interpreted by inner.HTML.
By successfully executing JavaScript on the web page we’ve effectively solved the lab!
That completes the lab! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod