User role controlled by request parameter
In this post we will walk step by step through how to solve User role controlled by request parameter on PortSwigger. This lab’s difficulty is Apprentice and it is the third lab in the SQL Injection labs on Portswigger.
Link to lab: https://portswigger.net/web-security/access-control/lab-user-role-controlled-by-request-parameter
To start the lab click the ‘Access the Lab’ button. A modern browser is all we need to solve this lab.
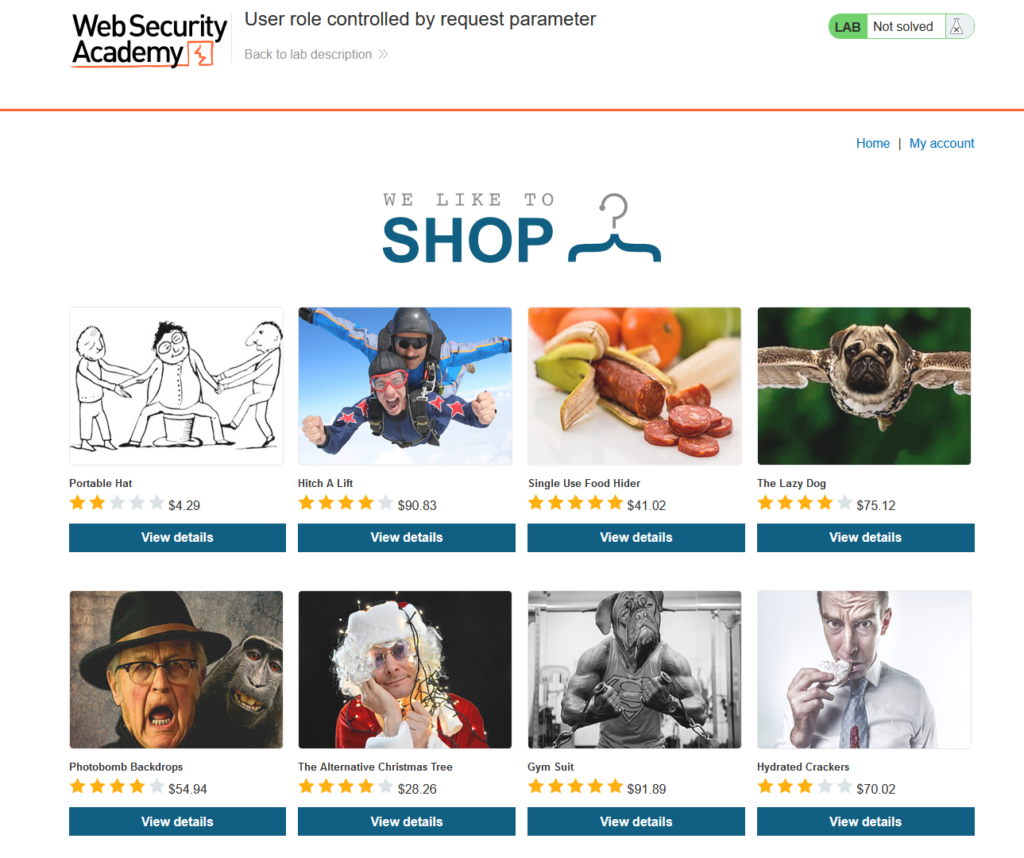
Starting the lab we are presented with a shop page that displays multiple categories. Don’t stress if your categories are different than the screenshot. PortSwigger Labs can change content each time the lab is started.
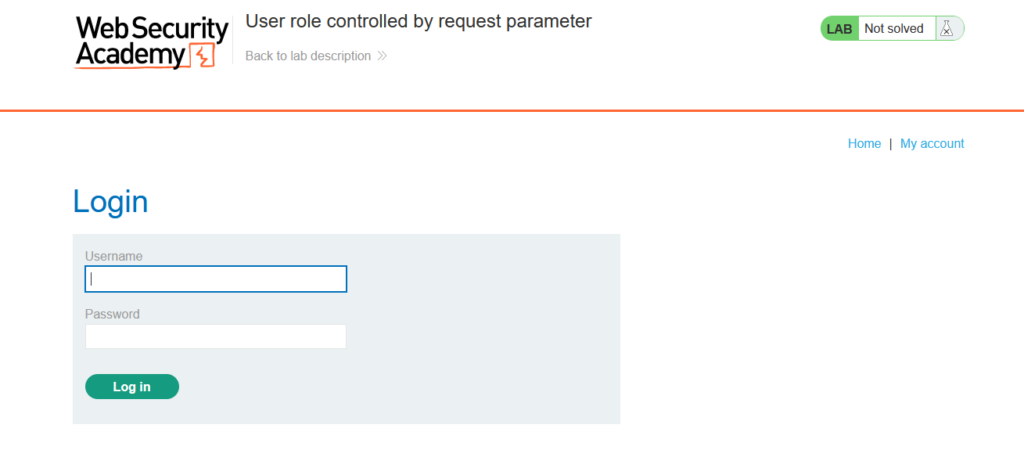
Clicking on the My Account link takes us to a login page. We can use the credentials provided to us at the beginning to authenticate. The credentials are wiener:peter.
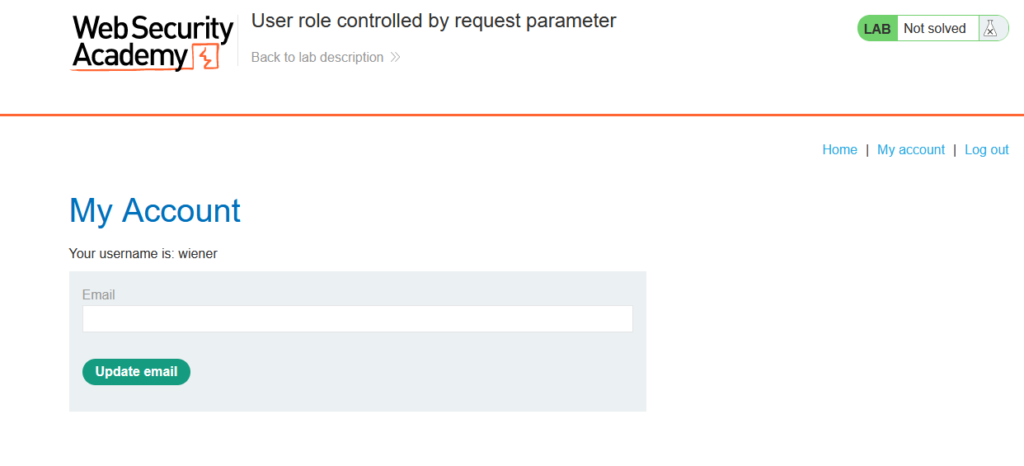
Now that we have logged in we can explore the application as an authenticated user.
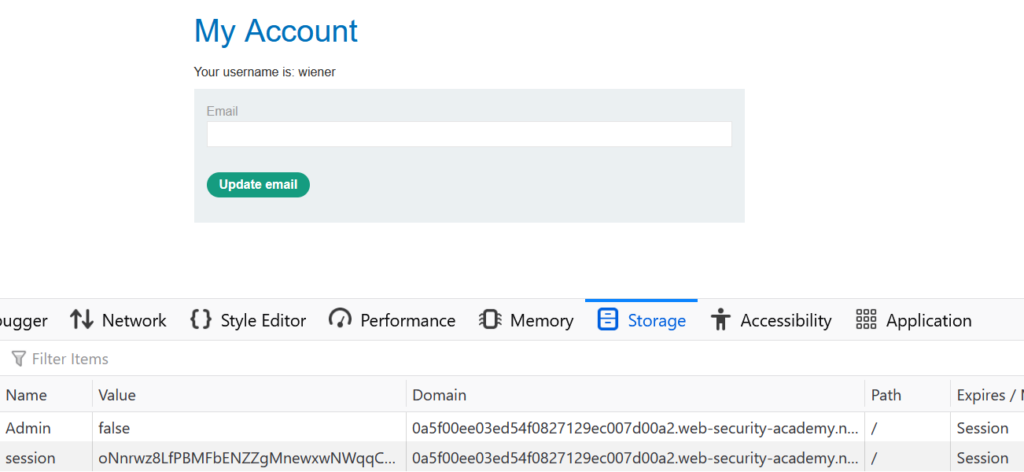
Reviewing the cookies we notice a session cookie named Admin and it is set to false.
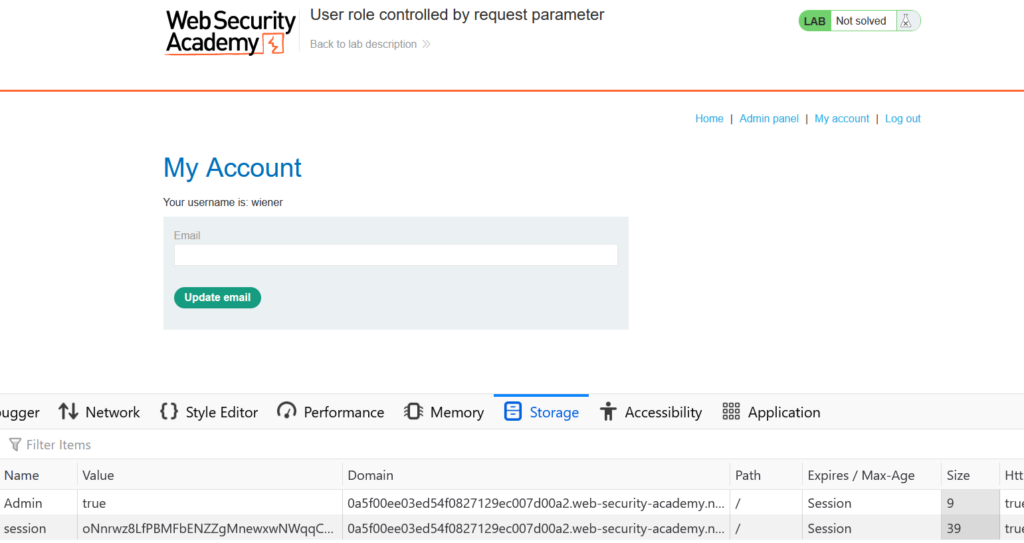
Setting the cookie value from false to true, and refreshing the page displays an Admin panel in the top right corner.
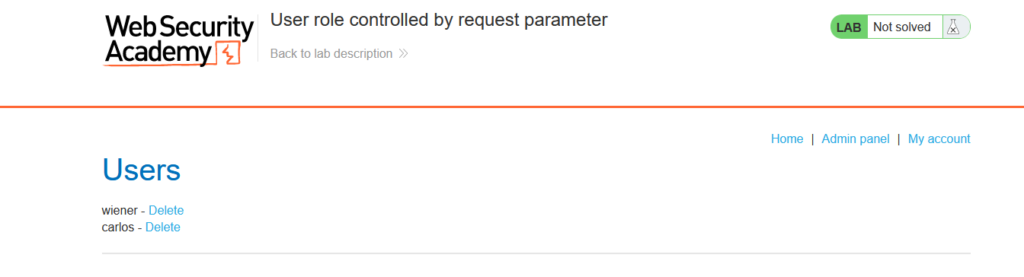
We have successfully elevated our privileges by abusing a cookie and we can solve the lab by deleting the Carlos user.
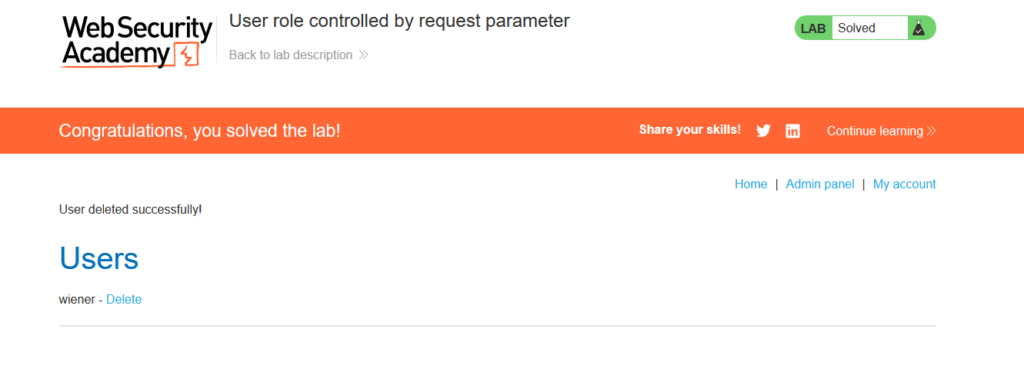
Deleting the user Carlos solves the lab! Congratulations.
That completes the lab! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod