DOM XSS in jQuery anchor href attribute sink using location.search source
In this post we will walk step by step through how to solve DOM XSS in jQuery anchor href attribute sink using location.search source on PortSwigger Academy. This lab’s difficulty is Apprentice and it is the fifth lab in the Cross-Site Scripting labs on Portswigger.
Link to lab: https://portswigger.net/web-security/cross-site-scripting/dom-based/lab-jquery-href-attribute-sink
To solve this lab, make the “back” link alert document.cookie.
To start the lab click the ‘Access the Lab’ button.
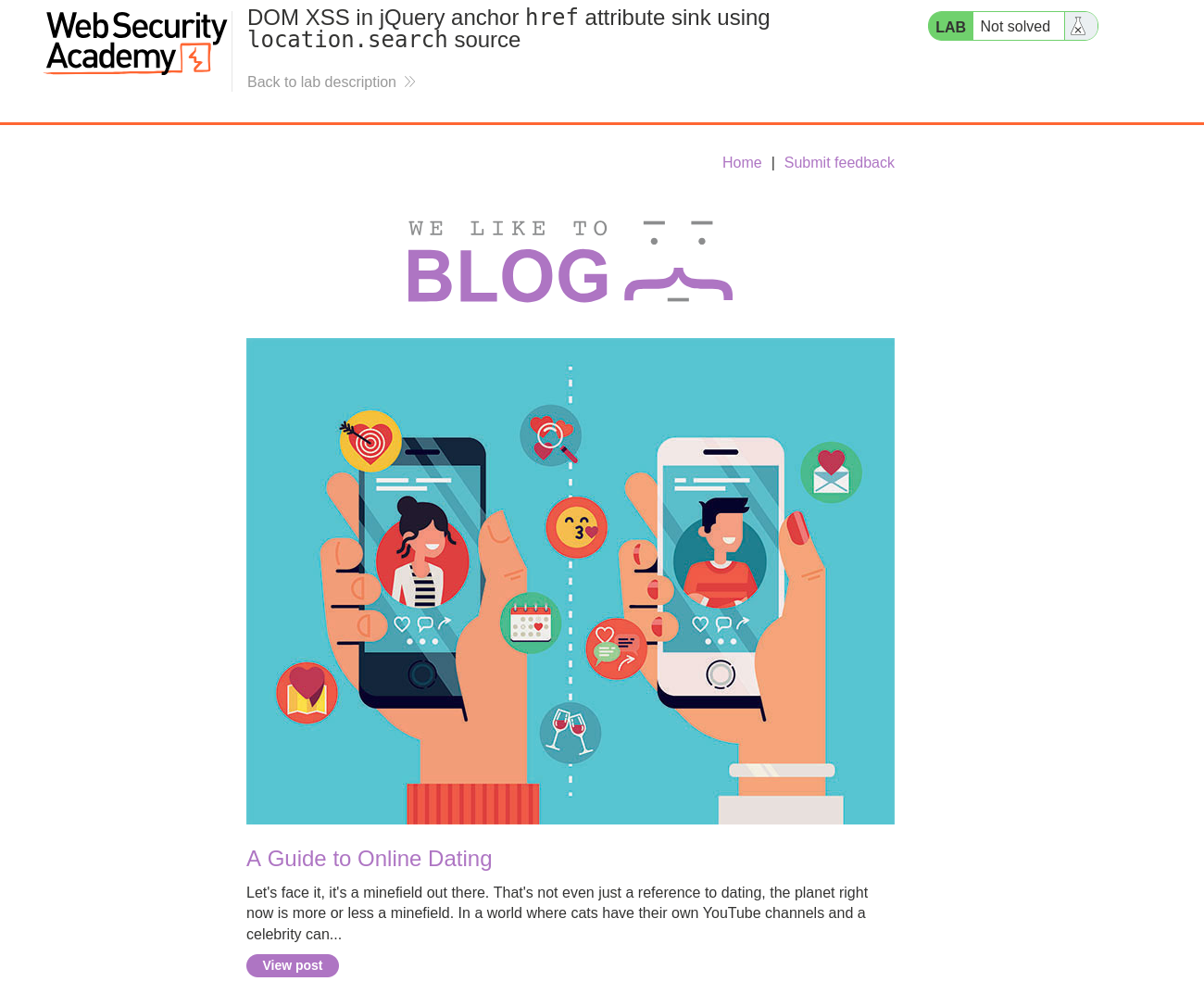
When we begin the lab we will be greeted with a blog page featuring a search field and a variety of blog posts. Don’t worry if the content differs from the screenshot; PortSwigger Labs can modify the content each time the lab is initiated.
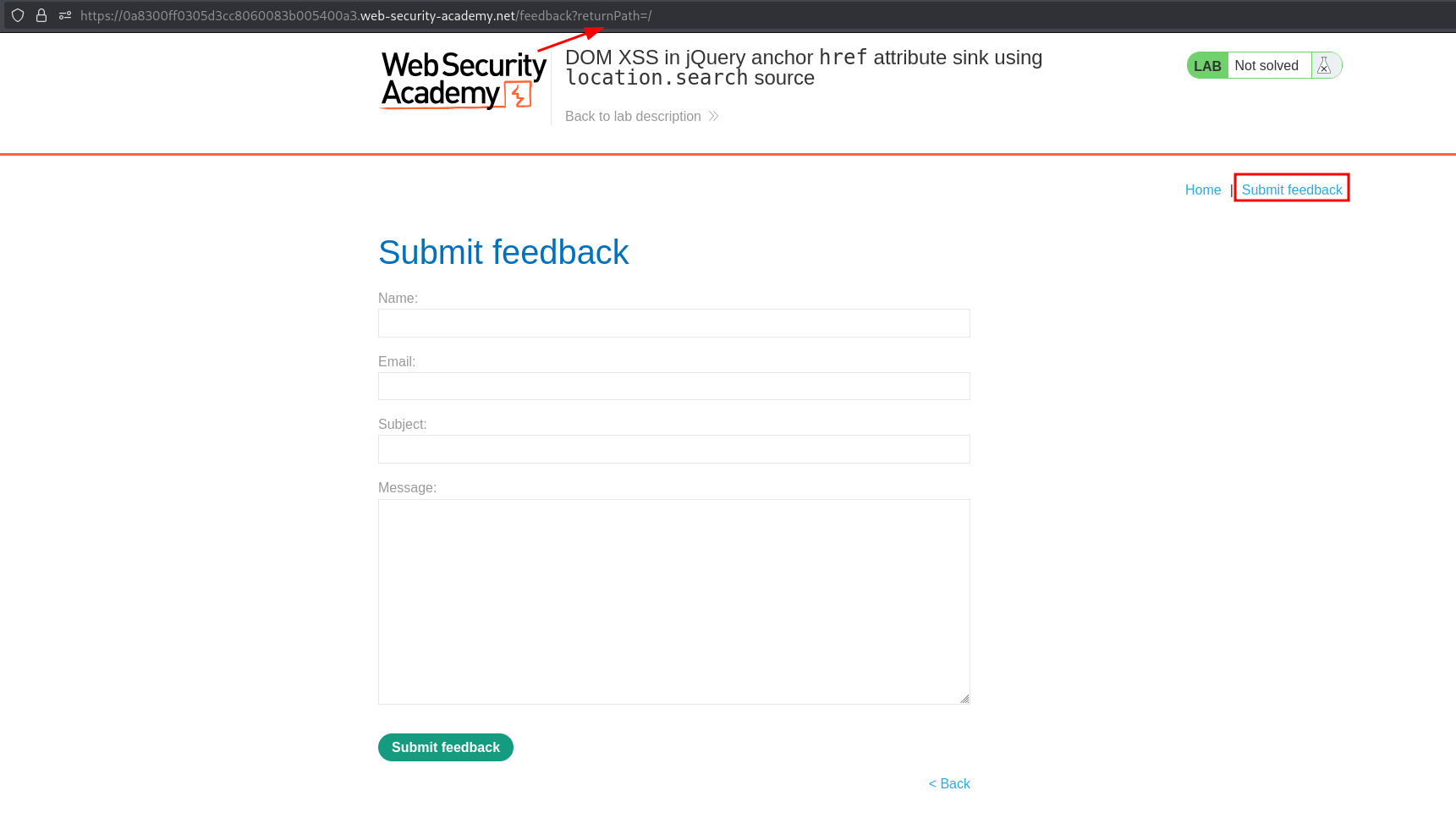
Clicking the Submit feedback link shows a returnPath parameter in the URL with a value of /.
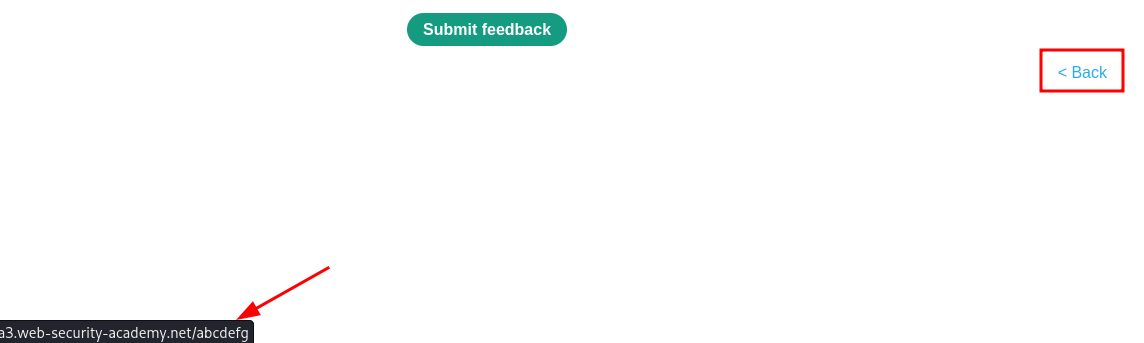
Adding abcdefg to the returnPath and pressing Enter reveals that the Back link at the bottom has abcdefg in the URL.
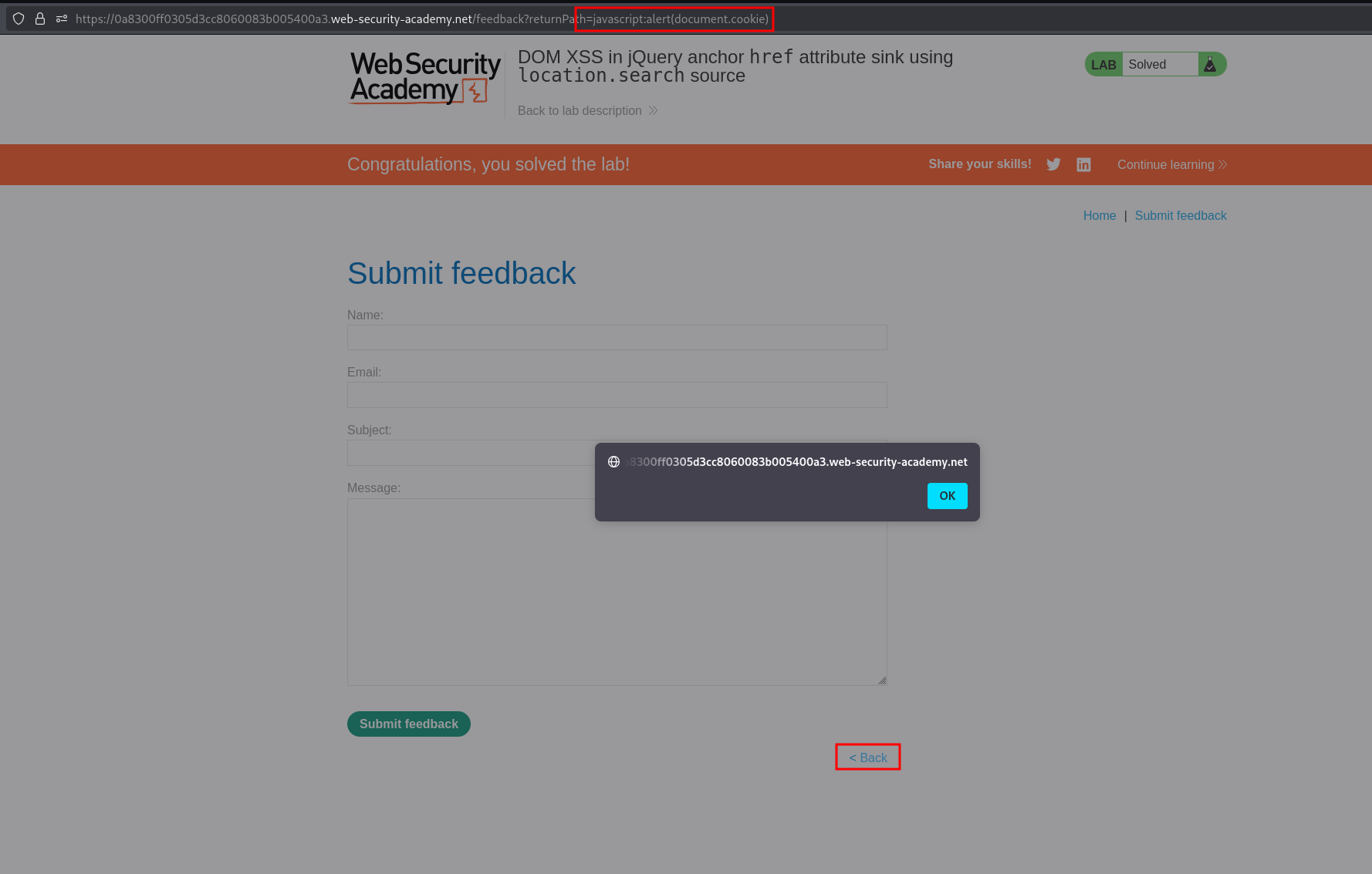
Knowing we can make a value reflect in the returnPath param we can use the payload javascript:alert(document.cookie) to possibly obtain XSS.
If you’re unfamiliar with javascript:alert(), this uses the JavaScript pseudo-protocol, also known as the javascript: URL scheme. This special type of URL allows JavaScript code to execute directly when used in the browser’s address bar or in HTML attributes like href. When the browser encounters a javascript: URL it runs the code following the colon instead of navigating to a new page.
Adding in the payload and pressing Enter, then clicking the Back link triggers the XSS payload in the web browser.
That completes the lab! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod